This post is all about 6 most deadliest data as well as file encrypting trojan that has targeted and attacked millions of Windows PC till date. To get complete details regarding this, keep reading this post till end.
## 1. WannaCry Ransomware : Infected More Than 230,000 Windows Systems
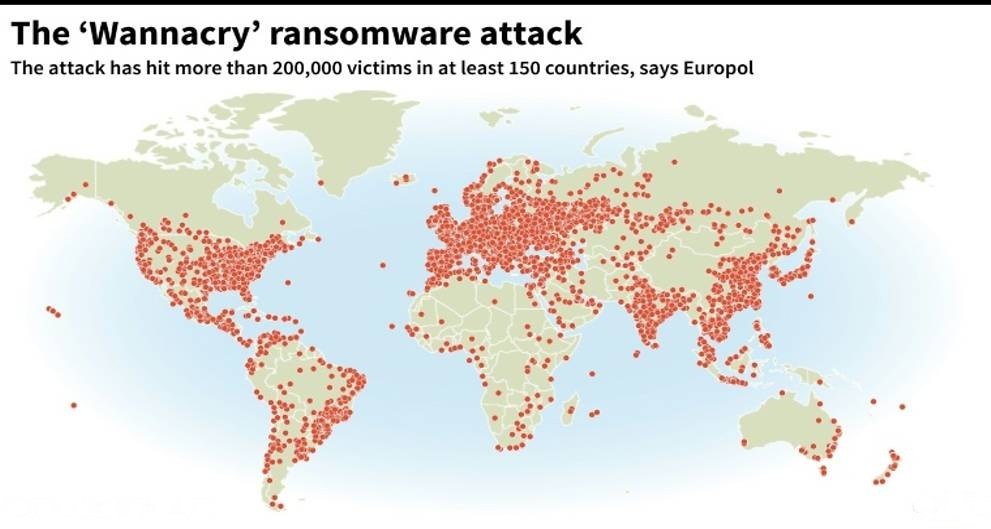
WannaCry ransomware recently infected almost more than 230,000 Windows system user within short period of time. Many of the system which were compromised belonged to the government hospitals and agencies. During the major WannaCry ransomware outbreak in the May 2017, there were several countries that were targeted with this infection including China, Russia, Taiwan, Brazil and even India. It infected both individual System users as well as government hospitals, organizations, railway companies, universities, telecommunications provides and tech firms in over 150 countries.
Malicious Doings of WannaCry Ransomware
It is really one of the widespread ransomware attack that mainly targets network using the SMBv1 which is a protocol that helps systems to communicate with the printers and several other devices connected to network. Several variants of WannaCry ransomware were reported thereafter with different names including WCry Ransomware, WannaCrypt0r Ransomware, WannaCrypt0r 2.0 Ransomware and much more. It actually takes advantages of Windows Computer to lock all stored files and block system users from accessing them unless they pay $300 BTC within 3 days. The creators of this ransomware also claims to double the price, if they don’t pay ransom fee within the given time period. In 2014, the team of cyber hackers knew how to use BTC in their operation. In 2015, they created a malicious backdoor and in 2016 they were involved in the $81m cyber-attack on Central Bank of Bangladesh.
Infiltration Method Opted By WannaCry Ransomware
According to the depth analysis by researchers, WannaCry Ransomware behaved as a worm that replicate itself and lurk inside the Windows Computer secretly without user awareness. It uses two advanced attack methods that detected in the leaked arsenal of NSA (DOUBLEPULSAR and EXTERNALBLUE). Experts also detected evidence that linked ransomware outbreak to North-Korean Lazarus Group. The developers of WannaCry Ransomware uses several deceptive ways but among all spam campaigns is one of the most common infiltration way through which it attack Windows System. Spam messages usually contain malicious attachments and links, opening of any spam messages or downloading of any malicious attachments may lead you to this infection. Besides, it can also attack your System through bundling method, pirated software, infected game server, malicious site, exploit kits, drive-by-downloads and much more.
Precaution Tips To Avoid PC Against WannaCry Ransomware
Once getting familiar with the infiltration channels of WannaCry Ransomware, you can easily avoid your System from the attack of ransomware by opting some safeguard tips. To stay yourself and your PC safe from the attack of WannaCry Ransomware, follow these simple prevention tips :
- Keep your installed application and software always up-to-date especially Operating System.
- Make sure that you are using a trusted and well-reputed anti-virus software.
- Don’t open any spam message or attachment that come to your inbox from unknown persons.
- Use always Custom/Advanced installation option to install any freeware packages or application.
- Avoid to visit any gambling website or unsafe domain that offers several digital downloads.
## 2. Petya Ransomware : Another Variant of Ransomware That Attacks Wide Range of Windows PC

Petya Ransomware is a variant of worst ransomware infection that has been activated over the Windows PC since at least March 2016 but it has been resurfaced by the group of hackers in June 2017. Like the other variant of ransomware, it follow the same principle as traditional ransomware do but the noticeable thing about this malware is that rather than locking file after file, it encrypt the MFT (Master File Table) to stop user to access entire hard drive. Although some of its versions are known to encrypt both files and MFT.
Want to know who is targeting with Petya Ransomware?
Petya Ransomware is supposed to be behind massive ransomware attack that infected organizations and companies across the global world in late June 2017. In that attack, the most affected country was Ukraine with the Ukrainian National Bank, the Kiev metro and several other airports. Several MNCs also reported being affected with Petya Ransomware including WPP, Maersk, Mondelez or Vivea.
Generally, it has targeted the HR departments in the private companies and public agencies with the false email applications that contain a download link of Dropbox. The download links often download an .exe file to encrypt the user’s stored files and make computer useless unless victims pay the predetermined amount of ransom fee in BTC. Some of the experts reported a new ransomware has been emerged in March 2017 named PetWrap. It is a patched version of original Petya Ransomware that comes with several modifications.
How to know your System infected with Petya Ransomware?
Once Petya Ransomware gets activated on your PC successfully, it will prevent you from accessing your files and PC normally. After making files inaccessible or unreadable, it causes blue screen of death error. It has started to locking your master table file and display several fake alerts, notifications or warning messages to trick you. Often, it project a skull onto a red a background and ransom demanding message that ask victim to pay ransom fee in bitcoin in exchange for getting the unique decryption key and decrypting files. But you should not pay the ransom demanded fee because researchers noted that hackers often ignore victim once ransom fee is submitted. Therefore, it is required to get rid of Petya Ransomware rather than making a deal with the cyber criminals.
How Petya Ransomware Infect Windows System?
At this time, nobody really knows about the infiltration method of Petya Ransomware but it has been suspected that it follow the same distribution channel as other ransomware do. Generally, it spread via spam messages that contain infected attachments and malicious links. If you access any message of your inbox or download any attachment that sent to your inbox from the unknown sender then it secretly penetrate inside your Computer. Besides, spam campaigns, it can also attack your PC when you download any pirated software or cost-free packages, use any infected device, share file over the P2P network and much more. Apart from these distribution channels, its creator always changes its infiltration way to attack PC but mainly distribute via the Internet.
How to prevent PC against Petya Ransomware attack?
After getting detail of Petya Ransomware’s infiltration method, you can easily avoid it by opting some safeguard tips or prevention measures including :
- Always keep your Operating System and installed application updated.
- Never open any suspicious email attachments and links.
- Use a trusted and legitimate anti-virus software.
- Choose Advanced/Custom installation option while installing freeware packages instead of opting default/typical one.
- Keep a backup copy of your all sensitive information and much more.
## 3. Cerber Ransomware : All Facts That You Must Aware About It

Cerber Ransomware is another member of the most dreaded Ransomware family which encrypts user’s all stored files using very strong file encryption algorithm. This variant of ransomware has an affiliate program for the team of cyber hacker. Like other ransomware, it encrypts files of the infected System users and demand huge amount of ransom fee in exchange for decrypting files and giving access to files back. It works in both means online as well as offline, so you cannot stop it’s infection by unplugging your Windows System.
Know Who is Cerber ransomware targeting?
Any Windows user can be a victim of Cerber ransomware except Computer users in the certain countries. If malware detect your PC is from Azerbaijan, Armenia, Kyrgyzstan, Georgia, Russia, Moldova, Kazakhstan, Ukraine, Uzbekistan, Tajikistan or Turkmenistan, it will automatically deactivate itself. But you have not be assume that you are safe if you are based in any of the listed countries. Because the creators of such an infection are evolved in attacking more and more Windows System.
Where does Cerber ransomware come from?
It may be come from Russia country. It thrives in Russian forums in depths of dark web, where Cerber ransomware can be purchased and deployed for around 40% ransom profits, payable to its creators. However, it refuses to attack the former Soviet countries but it does not mean that it cannot infect PCs of your country. Cerber ransomware uses lots of deceptive ways to attack PC but most of the cases, hackers victimized Windows Computer via spam emails. The victim usually receives an email or message with infected MS Office document attached. Besides, spam campaigns, this variant of ransomware can also affect your Windows Computer through P2P file sharing network, torrent hackers, exploit kit, P2P file sharing network, drive-by-downloads and much more.
How to recognize the attack of Cerber ransomware?
After lurking inside the Windows Computer successfully, first of all it will scan your System and then after try to locate the targeted files. It can infect all types of files. You can see it’s presence easily because it uses RSA and RC4 file encryption algorithms and renames the stored file by appending ‘.cerber’ file extension. Once targeting files and renaming them, it prevent System user from accessing their files normally. On the successful file encryption procedure, it changes desktop wallpaper and display a ransom note on the desktop screen.
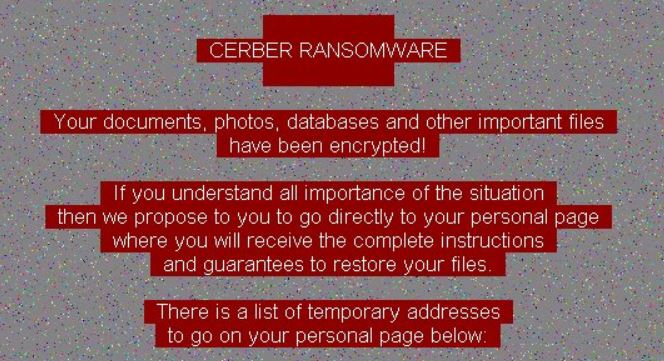
The ransom note may appear in the left on your desktop screen and inside of any folder that has encrypted file. Ransom note usually contain an instructions on how to pay ransom fee to attackers. Depending on BTC exchange rate, the amount of ransom fee may stretches from the several hundreds to thousand US dollars.
How To Prevent PC Against Cerber ransomware attack?
The file encryption procedure of Cerber ransomware is really unbreakable. Once your files get encrypted with such a ransomware, you cannot get them back easily even submitting the huge amount of ransom fee. You can avoid your crucial data by preventing your PC from the ransomware’s attack. For this, you have to opt some safeguard tips which are as follows :
- You have to keep an updated version of Operating System and existing application.
- Avoid to visit any insecure and malicious site.
- Never open any suspicious mail attachments and links.
- Select always Custom/Advanced installation mode instead of default/typical one.
- Use a trusted and legitimate anti-virus to protect your PC.
## 4. Locky Ransomware : Capable to encrypt more than 160 files types
Locky Ransomware : What do you know about it?
Locky Ransomware is another member of ransomware that was released in 2016 by the group of highly skilled and professional cyber hackers. It is designed in such a way that it can infect almost all version of Windows System. Being feature with most powerful features including complex spam campaigns, domain generation algorithm, generic PE packers and server-side encryption, it can encrypt more that 160 file types including databases and source code. According to the expert, this ransomware uses several scripting languages for attacking Windows PC.
Locky Ransomware mainly uses strong AES-128 + RSA-2048 cipher algorithm with the ECB to lock all stored files. After locking files, it make then inaccessible and generated an unique key on the server side. It is capable to encrypt files on all removable drives, fixed drives, RAM disk drives and Network drives. Once performing the encryption, it asks victim to make a ransom payment which may varies between 0.5 and 1.0 bitcoin.
Who is Locky Ransomware targeting?
Locky Ransomware has been considered as a most dangerous and harmful infection because it is capable to infect wide range of file formats including files used by the designers, engineers, testers and developers which means all small businesses as well as organizations are at the high risks. The top 10 countries that hit by the Locky Ransomware are Italy, France, Canada, Japan, Poland, Czech Republic, Germany, Italy, USA, Spain and Great Britain.
Where does Locky Ransomware appear from?

Being a member of the ransomware family, it open spreads via infected attachments and fake emails such as .xls, .zip or .doc files. Such an attachments or email documents do not displays the correct details and may ask user to enable the macro if the data encoding is incorrect. Spam email or malspam is a social engineering tactic used by hackers to trick system user because once somehow they enable macros, a binary file immediately start to executing and downloading this ransomware. Some of the people believe that Locky Ransomware comes from Russia because many of its related servers are there. The emails that infected with Locky Ransomware are usually disguised to look like they are coming from the legitimate sources. Opening of any spam attachment may lead you to this ransomware infection.
How To recognize the presence of Locky Ransomware?
If Locky Ransomware has execute into your PC then it will make your all file inaccessible and prevent you from accessing them normally. The encrypted files are usually given a new file extension that often named after the gods of Egyptian and Norse mythology including .odin, .osiris, .locky, .aesir or .thor. After that you will be prompted to pay the ransom fee in exchange for recovery key. The ransom message can be varied depending upon you Computer’s location.
Tips To Prevent PC Against Locky Ransomware
- Use always an updated anti-virus program or software.
- Don’t open any suspicious attachments or emails that come to your inbox from the unverified sources.
- Disable the MS Office macros by default.
- Keep a backup copy of your crucial files either online or an external drives.
- Be sure that you are using an updated version of Operating System.
- Use the Internet protection so that you can easily avoid the fake spam and emails.
## 5. CryptoLocker Ransomware : Another File Encrypting Ransomware
CryptoLocker Ransomware : What is it?
CryptoLocker Ransomware is a well known ransomware that is mainly capable to damage any data-driven organization. Between the September 2013 and May 2014, this variant of ransomware was known as a wide spreading ransomware infection that attack Windows PC at the wide range and infect around 500,000 system users. First of all, it was used the botnet named Gameover ZeuS botnet and infected spam email attachments to spread across the internet and infect almost all version of Windows Systems. According to the analysis report of researcher, it encrypts user’s all stored file using the strong RSA 2048 bit encryption algorithm and then victims are promoted to pay about $300 ransom fee to receive a password to decrypt the file.
In a crackdown entitled as ‘Operation Tovar’, a group of the security experts from Interpol, FBI, universities and security software vendors managed to stop cyber hackers. Such a ransomware has spawned a few clones including Cryptr0L0cker, Cryptowall, TorrentLocker and several other. In the recent years, the attacks of ransomware have become too much popular as well as dangerous which does not only make user’s stored data inaccessible but also keep their all privacy at the high risk.
CryptoLocker Ransomware : Where does CryptoLocker Ransomware come from?
CryptoLocker Ransomware usually infected the windows PC with an existing botnet through several malicious email attachments. When you open any spam message or attachment that appear in your inbox from an unknown sender then it secretly penetrate inside your Windows Computer without asking for your permission. The encrypted files usually stored on the local or mounted network drives. Since such a ransomware was not a virus, it did not spread across your network itself. Besides, it also uses drive-by-downloads, an exploit kit, torrent hackers, P2P file sharing sources, infected game server and much more to victimized Windows Computer.
CryptoLocker Ransomware : Signs Through Which You Can Recognize The Presence of It
Similar to the other variant of ransomware infection, you cannot identify its presences after the immediate infiltration. Because it secretly intrudes into the PC and perform several malicious tasks at the System background. You can notice its presence when it will lock your all stored files using weird file extension and prevent you from accessing your files. Once locking files, it will automatically change your desktop wallpaper and drop a ransom note that instruct victim on how to pay ransom fee.
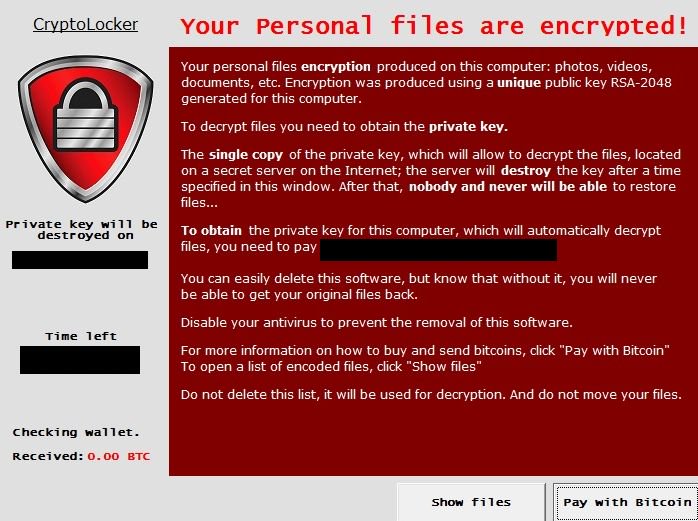
Is Paying Enough To CryptoLocker Ransomware’s Developers To Decrypt Files
Most of the innocent user think that they would decrypt their file after paying huge amount of ransom fee. But it is really not a wise decision because nobody could give you guarantee that you will decrypt your crucial files even paying the huge amount of ransom fee. Paying money to hackers is only encourage them to create more and more dangerous ransomware infection. When you will agree to pay ransom fee they will definitely ask for your sensitive data such as banking login details, username, system and network configuration details, debit or credit card details, password and much more. Thus, there is really no any need to pay ransom fee that demanded by the con artists of CryptoLocker Ransomware.
Safeguard Tips To Avoid PC Against CryptoLocker Ransomware
- Use a trusted and well-reputed anti-virus and keep it always up to date.
- Keep the regular backup of your all crucial files.
- Keep your installed application and OS always up-to-date.
- Avoid to give the administrative privileges to the user accounts.
- Before sharing any things on network, review the access control settings and much more.
## 6. Zeus trojan : An Online Banking Trojan That Can Steal Your All Personal Data

All Essential Facts That You Must Know About Zeus trojan
Zeus trojan also known as Zitmo and Zbot, it is one of the most widespread banking trojan infection today. It has been around since 2006 and having infected almost tens of millions of PCs. Such a variant of malware is available on the Windows PC as a toolkit, so that cyber hackers can use source code to build their own variants. Once, your PC is infected with Zeus trojan, it will take control of your Computer to download files, reboot, Computer shut down, causing System crash, deleted important Computer files and collect passwords from the protected storage. However, cyber hackers commonly use it to monitor the targeted sites, add fields and steal almost all crucial detail.
Who is Zeus trojan targeting?
Any Windows System users can be become a victim of Zeus trojan infection. Its first development, Zbot has been used by group of cyber criminals to gather detail from US department of the transportation, NASA, The Bank of America and some of the most popular private companies including ABC, Cisco, Oracle, Amazon and Monster.com.
How does PC infect with Zeus trojan?
Being a member of the notorious Trojan community, Zeus trojan make its own way to Windows PC via hacked or compromised sites or spam emails. The spam emails often appear to be sent from the trusted or legitimate sources. For example Starbucks may invite you to the special event, Linkedln or Facebook may ask you to log in your account and accept some of the friend request, invite you to download an executable file and much more. Apart from these, its creators uses several stealth techniques to attack Windows System.
How To Recognize Zeus trojan?
Similar to the other banking Trojan infection, its impact is very harmful for Computer users. This malware is designed to reside on the User’s PC without their intention to ruin PC slowly. Due to the presence of such a malware, you may notice that your System behaves too much slower than before, unnecessary modification is registry entries, crucial system files, System crash, BSoD error and much more. It is responsible to make your all stored data and file inaccessible and ask victim to pay ransom fee in order to decrypt file and access PC normally. But you should pay the demanded ransom fee under any circumstances. Because there are no any assurances provided by its developer that you will get the free decryption tool even paying the ransom fee.
How To Protect Windows PC Against Zeus trojan?
Once getting familiar with the infiltration method of Zeus trojan and it’s negative impact, you can opt some safeguard tips to avoid PC from the attack of Zeus trojan or other banking Trojan infection. Some of the most common precaution measures are listed below :
- Turn on your System restore feature and disable the macros in MS Office suite.
- Keep a Backup of your all crucial data on regular basis.
- Don’t open any suspicious email attachment that come to your inbox via unknown sender.
- Use only Custom/Advanced option to install any cost-free packages.
- Use very strong and unique passwords to keep your account protected.
