‘[email protected]’ Ransomware – Depth Investigation
Unlike infamous ransomware-type Trojans, ‘[email protected]’ Ransomware uses a hundred hard-coded email accounts to process its transmission and communication with C&C servers. These emails have very similar pattern. Even, some other ransomware have also been suspected to be the creation of ‘[email protected]’ Ransomware developers. As you can see, Ransomware,’[email protected]’ Ransomware and ‘[email protected] File Extension’ Ransomware have same naming pattern. However, we aren’t sure whether they are associated with each other or not. Since the ransomware is very new, at the time of writing, there is no strong evidence that verify distribution channels used by this ransomware. In other words, none knows how this ransomware is delivered to potential victims computer. ‘[email protected]’ file encoder is early discovered by cyber security community. Its executable file was found on numerous online security platform. May be, its developers are running few tests before releasing it publicly.

According to security investigators ‘[email protected]’ Ransomware must be in-Dev version because it features a critical flaw. This flaw force this file encoder program to display a message box with decryption password immediately before the file encoding process starts. Besides, the decryption password (private key) can be found into Registry Entries of affected Windows-machine. Though, experts rate this ransomware as a dummy project. However, ‘[email protected]’ Ransomware enciphers file containers hosted on Removable Drives, Local Disks or Network Attached Storage just right after a victim run macro-enabled script with administrative privilege. Identifying infected files so easy because the ransomware changes encrypted files icons into a binary code and appends ‘.ENC’ suffix to each enciphered file. For example, WalkingDead7.rar will be transcoded as WakingDead7.rar.enc. These types of file become completely useless and inaccessible.
Highlights of ‘[email protected]’ Ransomware infection
‘[email protected]’ Ransomware presents an HTA app entitled as ‘YOUR PC HAS BEEN BLOCKED’ with a Countdown Timer which shows decreasing of time from 24 hours. It demands 100 USD as ransom fee and suggest victims to write emails to ‘[email protected]’ including PC name, email, wallet address etc.
However, security experts have revealed a code (password) ‘g3On18lf’ that the ransomware shows whenever ransomware’s executable starts. Further, various AV vendors also flag following threats associated with ‘[email protected]’ Ransomware:
- -ILCrypt
- -TR/Spy.Gen
- -Trojan.Dropper.Generic
- -Trojan.MSIL.gen.a.1
- -Trojan.Zusy.D27131
- -Win32:GenMaliciousA-VFO [Trj]
- -Gen:Variant.Zusy.160049 (B)
- -HEUR:Trojan.Win32.Generic
They also revealed following email IDs associated with ‘[email protected]’ Ransomware:
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
Therefore, we recommend you not to contact ransomware developers. Instead you should try alternative methods to delete ‘[email protected]’ Ransomware from affected computer. Also, to safe guard your computer in future, you must keep your Antivirus software up-to-date and activated always. Finally, you should follow the given ‘[email protected]’ Ransomware removal and file restoring instructions:
Reference Video on How to Get Rid of ‘[email protected]’ Ransomware – Manual Removal Guide
Free Scan your Windows PC to detect ‘[email protected]’ Ransomware
Remove ‘[email protected]’ Ransomware From Your PC
Step 1: Remove ‘[email protected]’ Ransomware in Safe Mode with Command Prompt
- First of all disconnect your PC with network connection.
- Click restart button and keep pressing F8 key regularly while system restart.

- You will see “Windows Advanced Options Menu” on your computer screen.
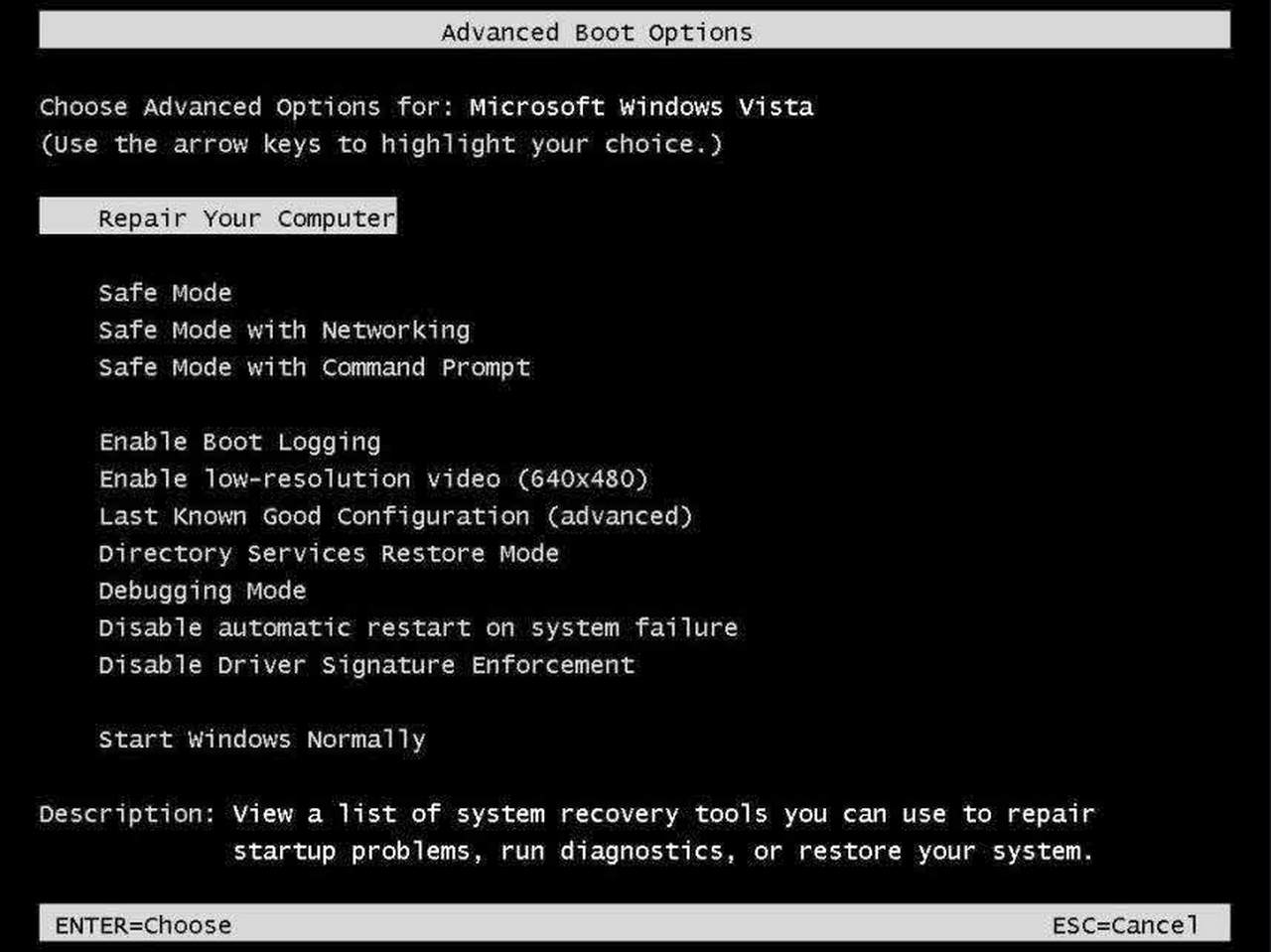
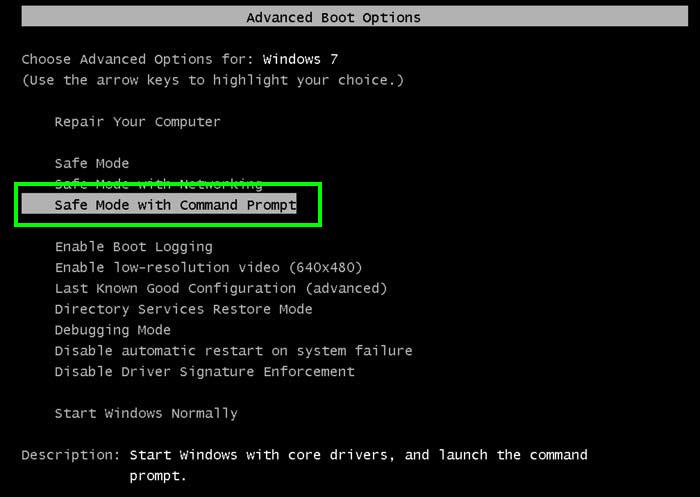
- Select “Safe Mode with Command Prompt” and press Enter key.
- You must login your computer with Administrator account for full privilege.
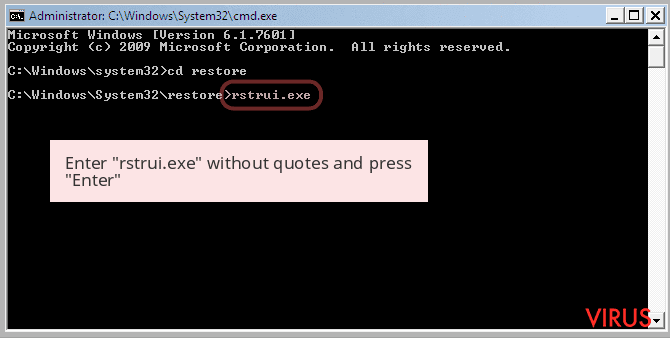
- Once the Command Prompt appears then type rstrui.exe and press Enter
- Now follow the prompts on your screen to complete system restore.
Step 2: Remove ‘[email protected]’ Ransomware using MSConfig in Safe Mode:
- Power off your computer and restart again.
- While booting press the “F8 key” continuously to open “Windows Advanced Options Menu”.

- Use the arrow keys to select “Safe Mode” option and press Enter key.

- Once system get started go to Start menu. Type “msconfig” in the search box and launch the application.
- Go to the Startup tab and look for files from %AppData% or %Temp% folders using rundll32.exe. See an example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N1
- Disable all the malicious entries and save the changes.
- Now restart your computer normally.
Step 3 : Kill Malicious Process Related To ‘[email protected]’ Ransomware
- Press Alt+Ctrl+Del buttons together.

- It will open the Task manager on your screen.
- Go to Process Tab and find ‘[email protected]’ Ransomware related process.
- Click the End Process Now button to stop the running process.
Step 4 : Remove ‘[email protected]’ Ransomware Virus From Registry Entry
- Press “Windows + R” key together to open Run Box.

- Type “regedit” and click OK button.

- Find and remove ‘[email protected]’ Ransomware related entries.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Runonce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
Now hopefully you have completely removed the ‘[email protected]’ Ransomware virus from your computer. If you are still get ransom message from the threat or unable to access your files, then it means that virus still remain into your computer. In such situation you don’t have any other option except removing this virus using any powerful malware removal tool.
Whereas if you have any backup of your infected or encrypted files, then you can also reinstall your Windows OS. This will erase all your files and data as along with the ‘[email protected]’ Ransomware infection. You will get a completely empty computer system with no files. Now you can use your backup to get your files. If you don’t have any backup then using malware removal tool is a better option for you.
If you have any query or question regarding your computer, then you can easily ask your problem to our experts. Go to the Ask Any Question page and get the answer for your query directly from out experts.




