Complete Description on Jhon Woddy Ransomware
Malware researchers have identified a new file-encrypting malware named as Jhon Woddy Ransomware. As usual for such type of cyber threats, it enters to the targeted computer, locate possible vital system files, and then encode them by using sophisticated AES encryption algorithm. Although, media indirectly invites the cyber hackers in order to get onto the track again with a new ransomware infection and few con artists already respond to such invitation. There are have been lots of ransomware threats with odd titles appearing into the online marketing. After a depth analysis, it looks like the Jhon Woddy Ransomware virus does not seem to possess an intricate components. Even though, the malware has become a trend among cyber crooks, but the threat doesn't target the mobile owner yet.
At the time of writing this article, there have been no research report yet whether the Jhon Woddy Ransomware will evolve to a bigger cyber campaign. Luckily, a very low number of this ransomware infections were detected. Generally, the criminal hackers take inspiration from film industry, pop culture, or mythology in order to give names to their creations. However, many might speculate whether there is hidden alerts behind this ransomware. Though, the malware reminds the name of Hollywood actor named John Woody, such similarity might be just coincidental. Speaking about the capabilities of Jhon Woddy Ransomware, it encrypts the system files placed on a desktop and stored on local disk. What's more, never try to pay the ransom money because it doesn't provide any guarantees that the encoded files will be returned. Instead, security analysts recommend you to remove this ransomware immediately.
How Does Jhon Woddy Ransomware Attack Targeted PCs?
This ransomware basically paves its way onto the targeted users' machine through spam emails. Cyber offenders have developed deceptive ways to persuade the PC users with counterfeited tax refund, invoices, and messages. The hackers often alert the users in order to review the attachments immediately by making up a bogus story about severe possible outcomes for a delay. Although, it is just a psychological pressure not to leave extra time for the victims to look for an alternative options. Also, Jhon Woddy Ransomware infection might have taken place as a result visiting hacked or a corrupted web portals. It happens usually to be a torrent sharing websites.
Most Important: Fortunately, if you are a victim of Jhon Woddy Ransomware virus, then you can ignore it all and type M3VZ>5BwGGVH into the password box in order to get all your important files back to the normal that are encrypted by this ransomware. After that, you need to eliminate this infection and any other malicious component that it added to your machine immediately. One of the best removal method recommend by the RMV security analysts is an anti-malware shield that will eradicate the Jhon Woddy Ransomware automatically.
Free Scan your Windows PC to detect Jhon Woddy Ransomware
Free Scan your Windows PC to detect Jhon Woddy Ransomware
A: How To Remove Jhon Woddy Ransomware From Your PC
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
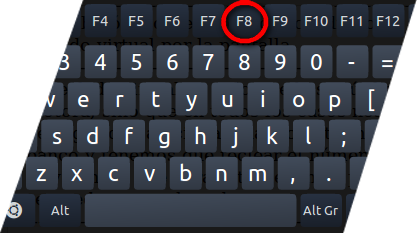
- Press and hold down the F8 key during the restart process.
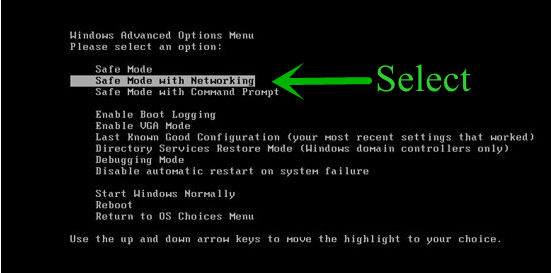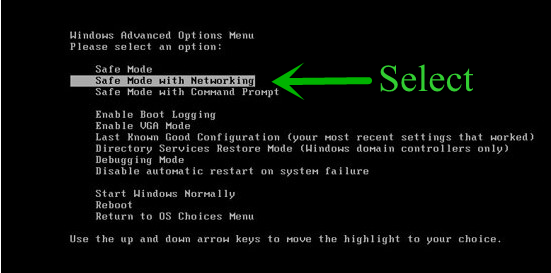
- From the boot menu, select Safe Mode with Networking using the arrow keys.
Step: 2 How to Kill Jhon Woddy Ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the Jhon Woddy Ransomware related Process.
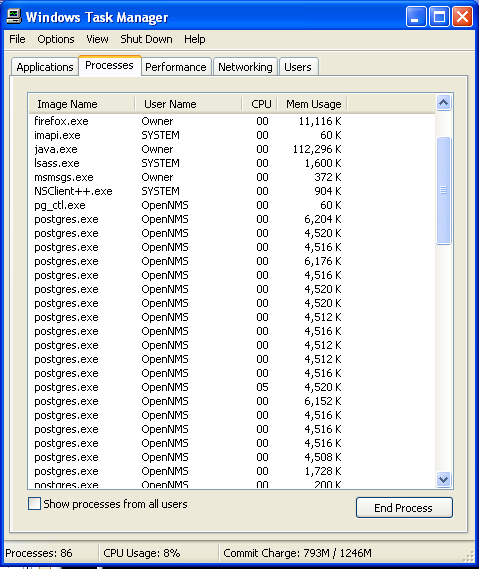
- Now click on on End Process button to close that task.
Step: 3 Uninstall Jhon Woddy Ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
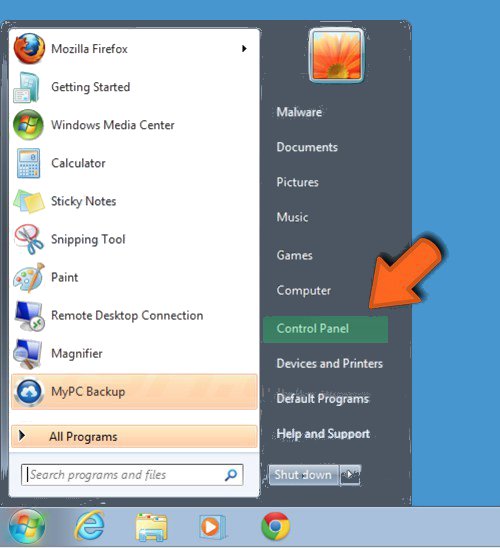
- Select Uninstall a Program option from Program category.
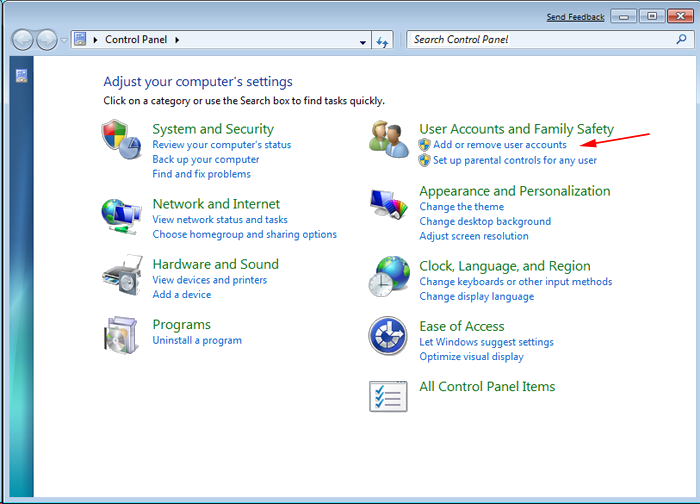
- Choose and remove all Jhon Woddy Ransomware related items from list.

B: How to Restore Jhon Woddy Ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing Jhon Woddy Ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
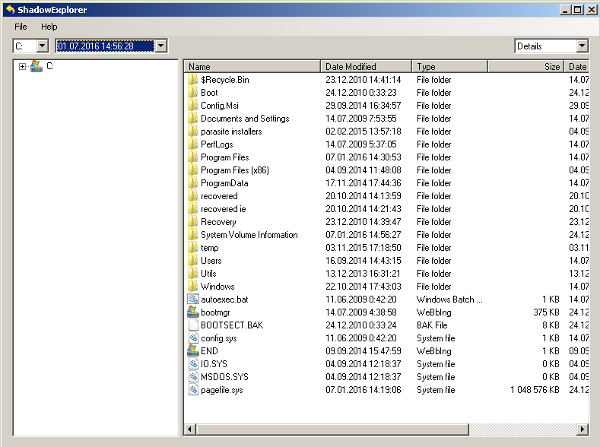
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing Jhon Woddy Ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
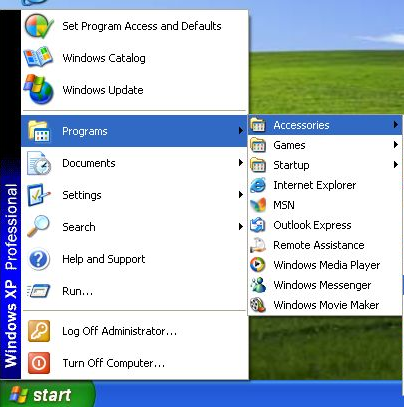
- Find System Tools and click System Restore
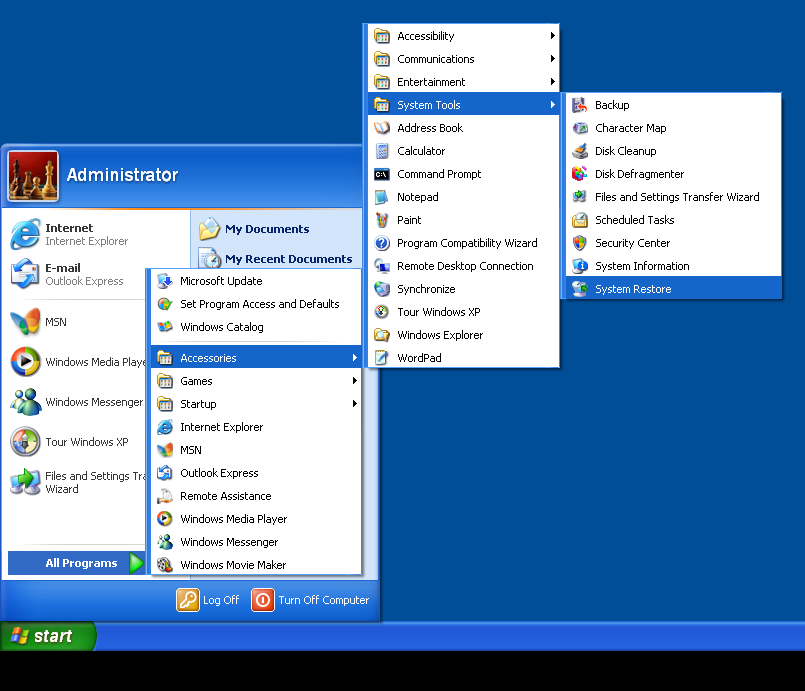
- Select Restore my computer to an earlier time and click Next.
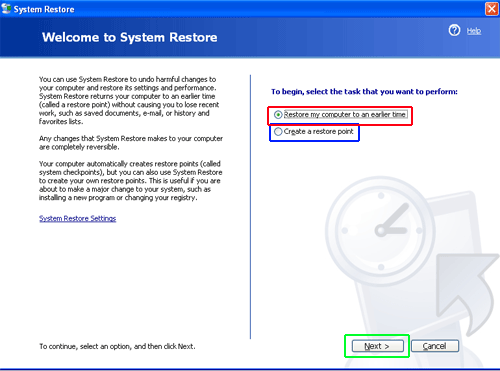
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by Jhon Woddy Ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.



