
[email protected] File Extension Ransomware : Threat's Profile
| Name | [email protected] File Extension Ransomware |
| Version of | InsaneCrypt Ransomware |
| Category | Ransomware |
| Affected Computers | Windows 32 & 64 |
| Risk Level | High |
| Infection Length | Varies |
| Extension | [email protected] |
| Ransom Note | key.txt |
| Description | [email protected] File Extension Ransomware is a newly detected ransomware that aims to lock files and asks victim to pay ransom demanded fee in BTCs to get ransom fee back. |
| Symptoms | Uses strong algorithm to makes your files inaccessible, added [email protected] File Extension to lock file and delivers a ransom note to extort money from victims. |
| File Decryptable | Yes |
| Removal Recommendations | Download Windows scanner to detect and delete [email protected] File Extension Ransomware. |
All Crucial Facts Related To [email protected] File Extension Ransomware
These days, a new ransomware infection has been reported by the group of malware researchers that infect wide range of unsuspecting user's System. According to the security analysts, it is a new version of InsaneCrypt Ransomware that uses [email protected] file extension to lock the affected files. Similar to other ransomware variant, it uses massive spammed email campaigns to trick novice users into opening it as an attachment or clicking on it as email. Spam email often pretends itself as a legitimate one to trick user but it is not at all. Besides, spam campaigns, it victimized Windows PC via suspicious ads, gambling site, torrent files, infected devices, P2P file sharing sources and much more.
File Encryption Procedure of [email protected] File Extension Ransomware
The primary objective of [email protected] File Extension Ransomware is to lock all files that stored on Windows System such as images, audio as well as video files, PDFs, documents, databases etc. Once [email protected] File Extension Ransomware infected Windows System, first of all it automatically connect itself to remote host and download it's payload. After that immediately start it's file encryption algorithm to make files unreadable or inaccessible. Once locking files complete, it drops a ransom note on desktop screen entitled as key.txt contains following message :
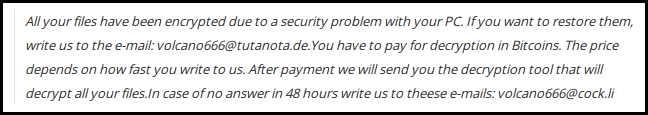
Don't Trust on Ransom Message of [email protected] File Extension Ransomware
The Ransom note file contains information about the file encryption and instructions on how to pay ransom fee in exchange for decryption in BitCoin. The developers of [email protected] File Extension Ransomware delivers 48 hours of deadline to pay ransom demanded fee. But you should not trust on the message or text of [email protected] File Extension Ransomware message because ransom note is just only a tricky thing used by the creators of ransomware to earn illicit profits from victims. Affected users can easily restore or recover their valuable data using backup copy. But to keep all crucial data as well as PC safe for long time, it is very necessary to delete [email protected] File Extension Ransomware from infected machine.
Free Scan your Windows PC to detect [email protected] File Extension Ransomware
How To Remove [email protected] File Extension Ransomware Virus Manually
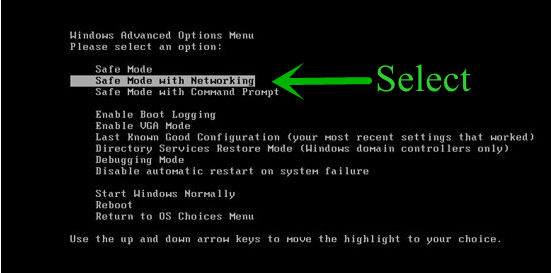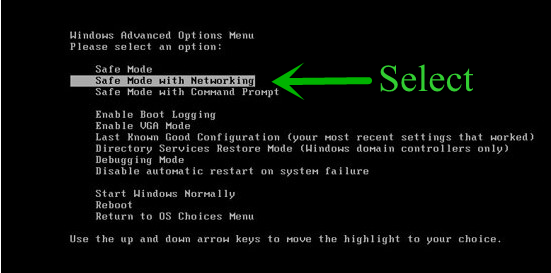
Step 1 : Restart your computer in safe with networking
- Restart your computer and keep pressing F8 key continuously.

- You will find the Advance Boot Option on your computer screen.

- Select Safe Mode With Networking Option by using arrow keys.
- Login your computer with Administrator account.
Step 2 : Step all [email protected] File Extension Ransomware related process
- Press the Windows+R buttons together to open Run Box.

- Type “taskmgr” and Click OK or Hit Enter button.

- Now go to the Process tab and find out [email protected] File Extension Ransomware related process.

- Click on End Process button to stop that running process.
Step 3 : Restore Your Windows PC To Factory Settings
System Restore Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
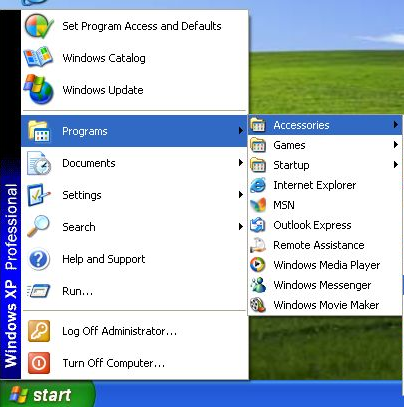
- Find System Tools and click System Restore.
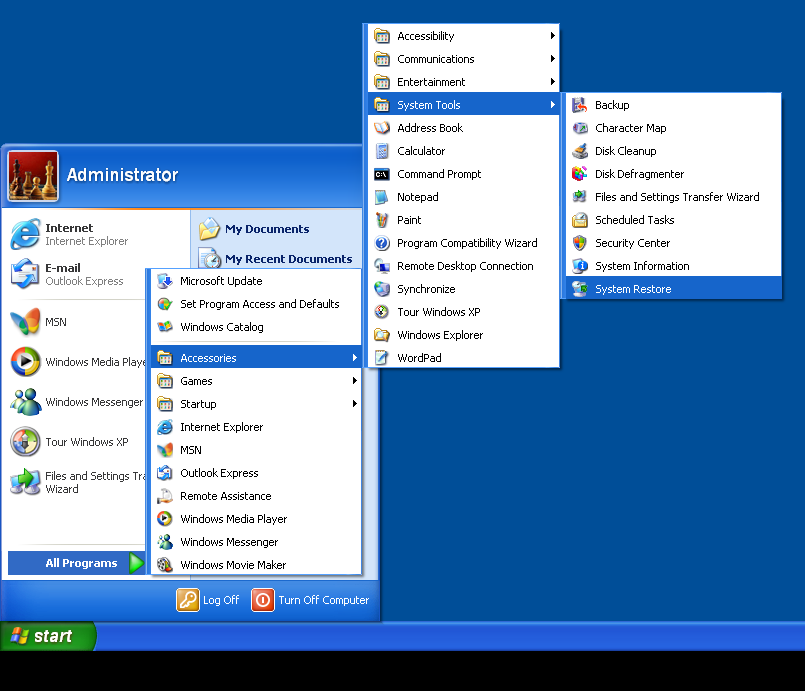
- Select Restore my computer to an earlier time and click Next.
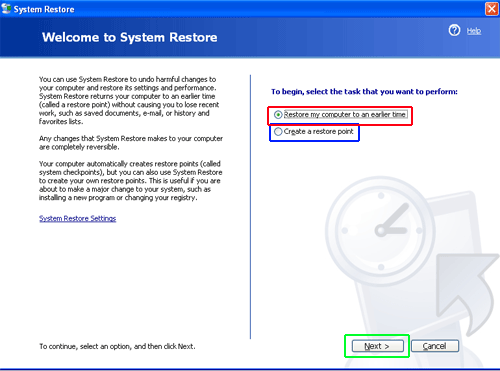
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results.
- From the System Restore window, click the Next button.
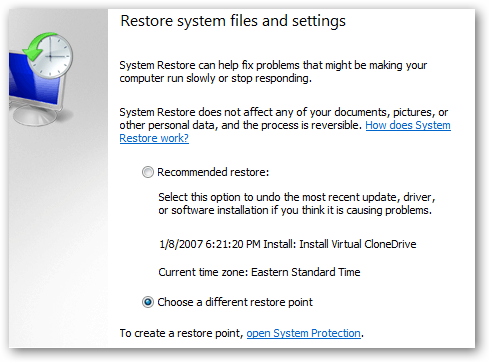
- Now select a restore points when your PC was not infected.
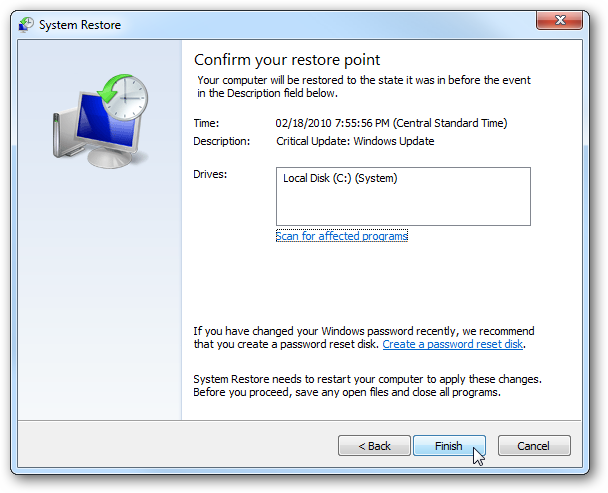
- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel.

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option.

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.
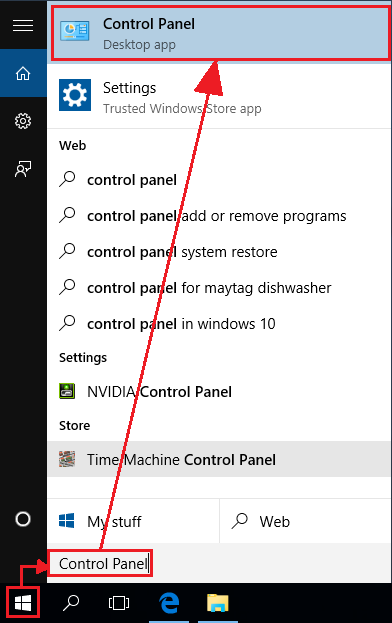
- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Hope these manual steps help you successfully remove the [email protected] File Extension Ransomware infection from your computer. If you have performed all the above manual steps and still can’t access your files or cannot remove this nasty ransomware infection from your computer then you should choose a powerful malware removal tool. You can easily remove this harmful virus from your computer by using third party tool. It is the best and the most easy way to get rid of this infection.
If you have any further question regarding this threat or its removal then you can directly ask your question from our experts. A panel of highly experienced and qualified tech support experts are waiting to help you.




