
Actually Necurs botnet is known as distributor of malware like Locky especially. And now it is again used as business, going for nearly a month. According to system security researcher’s report Necurs botnet has returned with feature of emit massive number of email containing an upgraded version of the powerful Locky ransomware along with the Dridex banking Trojan that is capable to steal user financial credentials.
The Proofpoint describes that Necure botnet has been used by cyber scammers as channel for delivering ransomware. On Monday criminals start pushing multimillion email message campaigns. On May 31 from the day it went dark, this activity has been considered as its first life Proofpoint from Necure botnet.
Proofpoint Wrote in analysis of Necure botnet that has been posted on Thursday that Analysing of sending IPs associated with this campaign suggest that the Necurs spam cannon is functional again and, unfortunately, we expect both Dridex and Locky email campaigns to begin again in earnest.
Necure botnet has been considered as one of the most largest bonets with 6.1 million bots are currently in use and may cause losses of dollar in million which is tired with ransomware and Dridex banking trojan. As we know that Locky rasnomware is popular for 17,000 dollar payday that has been encrypted and held for ransom data maintained in February by the Hollywood Presbyterain Medical Center in California. Dridex has been found to ensnare tens of millions of dollars from victimized pc users based in the United Kingdom as well as United States.
According to Proofpoint, Necurs, Locky and Dridex had sharpen as an effective crime formula which are snaring between hundred thousand dollar and 2 hundred thousand dollar per day in criminal activity. On 1 June the activity around it has been sharply dropped off.
Vice president of Threat Operations Center, Kevin Epstein at Proofpoint said “We have no idea why Necurs stopped, but we theorize it may have had somethings to do with a glitch in the command and control function of botnet.
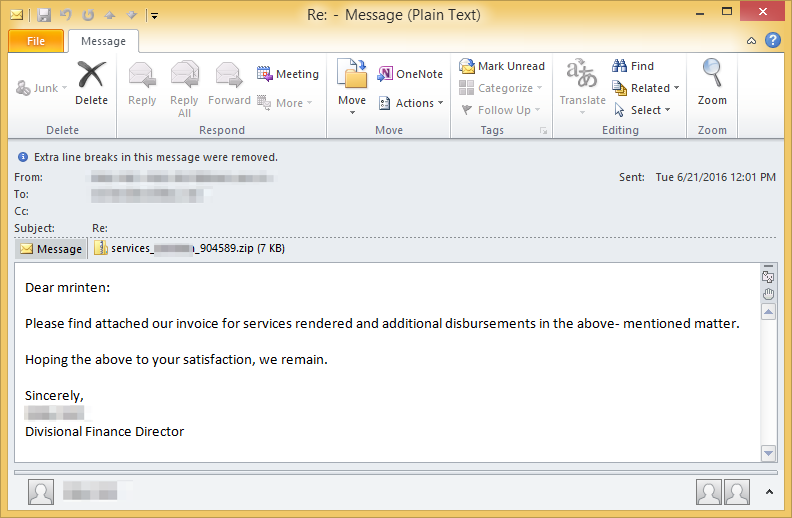
Researcher at AppRiver, Deloitte’s Cyber Risk Services and MalwareTech has also spotted Necurs. Deloitte’s Cyber Risk Services has noted that email messages that are delivered to users are written as follow :
Dear (random name): Please find attached our invoice for services rendered and additional disbursements in the above-mentioned matter. Hoping the above to your satisfaction, we remain. Sincerely, (random name and title).
The locky campaigns like zip attachments contain JavaScript code – said Proofpoint. Researcher added in their note that to Locky ransomware the new components include new anti-analysis tricks which includes detecting if it is running within a sandbox test environment versus a live infection. This done through use of complicated mathematical analysis ensuring the time taken for the ransomware to execute API calls. Proofpoint also wrote : “The malware compares the number of CPU cycles that it takes to execute certain Windows APIs. As you would expect, it takes more cycles in a VM environment to execute most Windows functions,”
Said by Proofpoint researchers “The Necurs outage last week is our most obvious evidence to date of its use in the massive Locky and Dridex campaigns that we have been tracking this year. While this is not the first apparent Necurs outage we have seen, available data suggest that it involved a significant and ongoing failure of the C&C infrastructure behind the botnet,”
Second perplex techniques include to which Epstein called as “tap dance within memory” for cross-module execution of the Locky payload. Vice president of Threat Operations Center says Proofpoint is already tracking an escalation of Locky campaigns since Necurs came back online. He also estimated that Necurs is pushing out 80 to 100 million email messages per day.
