Depth-Analysis on Locky ransomware
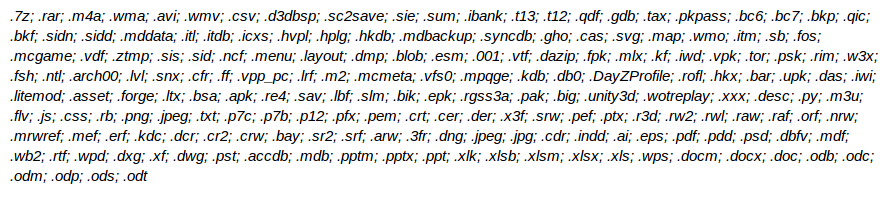
Ransomware viruses have become increasingly common in last few years. In the first two months of year 2016, PC users have come across thousands of new ransomware threats and the variants of previous ransomware infections. One of the most nasty threats Locky ransomware showed up in the beginning of year 2016. Since then, it has released its variants and constantly changing its distribution tactics in order to extort money from the affected computer users. It is not quite hard to detect the presence of this dangerous ransomware virus, because you’ll notice one of the weird extension added to your encrypted files, such as “.locky”, “.shit”, “.odin” and “.zepto”.
Locky ransomware : Latest Distribution Tactics
Most important, the Locky ransomware virus tends to follow the same approach for infecting a targeted system. It will be distributed using common delivery methods. In most of the cases, it infect user’s machine via spam email attachments. It spreads as a JS, HTA or WSF files which try to convince the users that they contain some vital files inside it. One of the most popular and malicious JavaScript is identified as MRI6219316107.js. This harmful JS is believed to be the most important one for the cyber hackers used to install “.locky file extension” virus on the computer.
Besides, the cyber security analysts have also revealed that the Locky ransomware relies on “.lnk” files that are transferred to the targeted machine with the help of nasty Nemucod. These LNK files represents the Windows shortcuts and it can be linked to an already installed application, such as Powershell. The malicious files carries the Powershell script which connects to the specific insecure websites by using a deceptive parameter. Moreover, the use of the parameter indicates that the con artists control these web portals, and these phishing domains can just compromised ones held under the control by cyber offenders. In the mid of 2016, the infamous botnet reported as Necurs started delivering the updated versions of Locky ransomware. After successfully invading the user’s computer, it will encrypt the files with following extensions:
How Does the Locky ransomware Virus Operate?
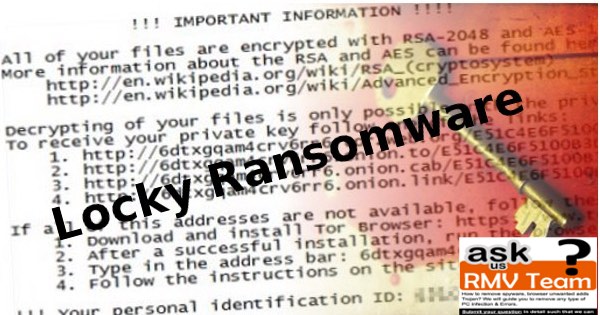
Furthermore, this ransomware encrypts the files stored on the infected machine by using AES encryption algorithm. Once it encodes the data, it will alter the affected files extensions to “.locky” which indicates that the file have been enciphered. Also, Locky ransomware will delete the Shadow Volume copies of the encoded files as well as the System Restore point, in order to make it impossible for the infected system users to use an alternate options to retrieve their vital files. Then after, it creates a ransom notification called “_Locky_recover_instructions.txt” and placed a copy of ransom note in every single folder which holds the enciphered data.
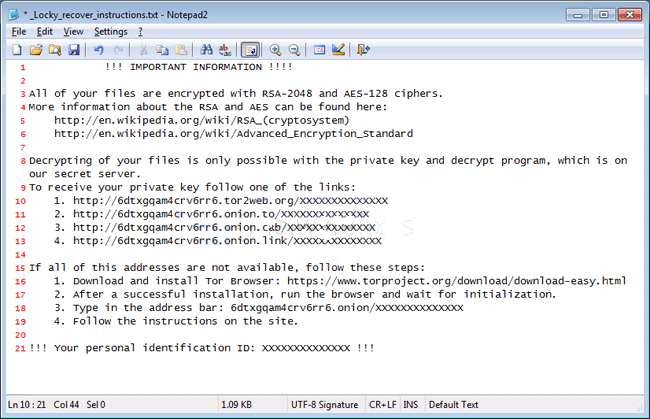
In addition to that, Locky ransomware changes the desktop background with “_Locky_recover_instructions.bmp” picture, which shows the same information provided on the ransom note. Although, the “.onion” links mentioned in both of the aforementioned files left by the malware that leads to the Locky payment web portal, which offers the Locky Decrypter for 0.5 BTC to 1.0 BTC, approximately equal to $545 to $1090 at the time of writing this security report. Unfortunately, it is currently impossible to decode the files encoded by “.locky file extension” ransomware virus without having the decryption key, which is stored onto the C&C (Command and Control) server operated by the malware developers. However, you should never pay the ransom fee demanded by the ransomware makers, instead eliminate Locky ransomware by using a powerful and credible anti-malware scanner. Hence, to recover your important files or data, you can use the backup copies after removing this ransomware completely from your system.
Locky ransomware Removal Info (Video Guide) – YouTube
Free Scan your Windows PC to detect Locky ransomware
Free Scan your Windows PC to detect Locky ransomware
A: How To Remove Locky ransomware From Your PC
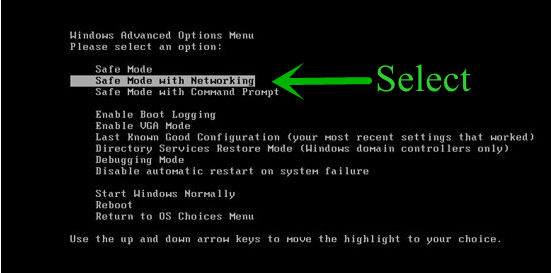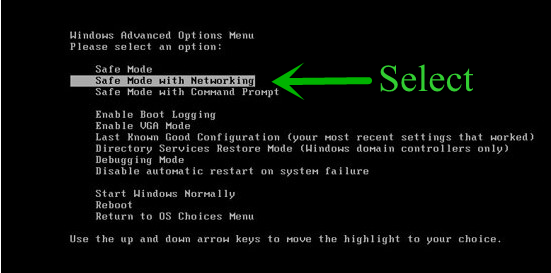
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.
- From the boot menu, select Safe Mode with Networking using the arrow keys.
Step: 2 How to Kill Locky ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the Locky ransomware related Process.
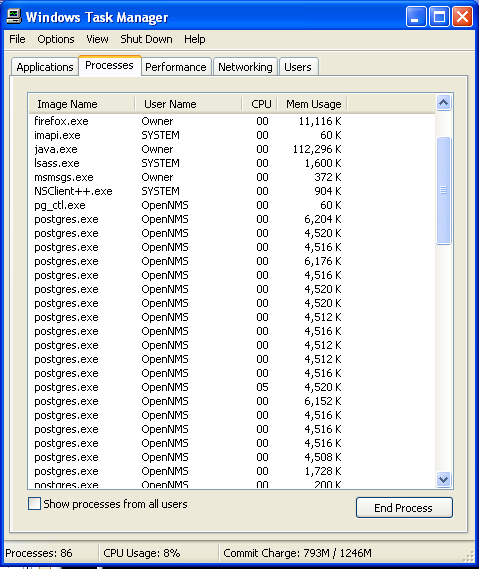
- Now click on on End Process button to close that task.
Step: 3 Uninstall Locky ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
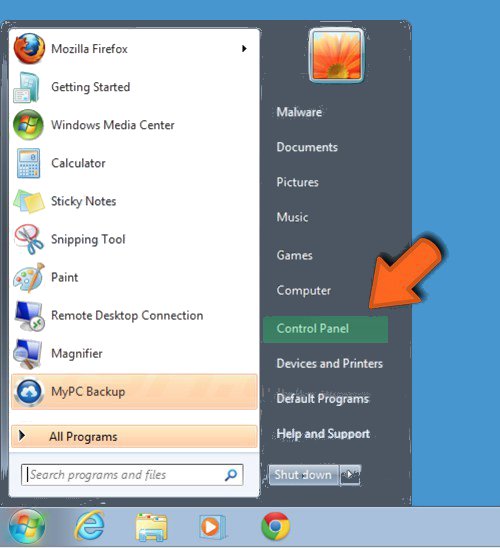
- Select Uninstall a Program option from Program category.
- Choose and remove all Locky ransomware related items from list.

B: How to Restore Locky ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing Locky ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
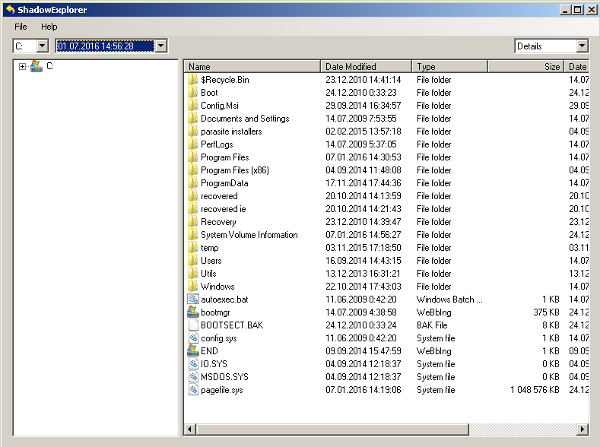
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing Locky ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
- Find System Tools and click System Restore
- Select Restore my computer to an earlier time and click Next.
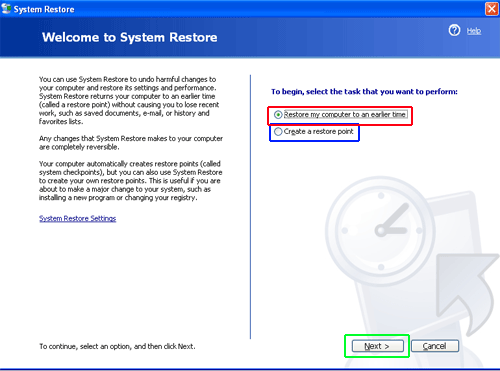
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by Locky ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.



