Tizer78224 Ransomware : Threat’s Analysis
| Name | Tizer78224 Ransomware |
| Type | Ransomware |
| Risk Impact | High |
| Description | Tizer78224 Ransomware uses modified file-encryption algorithm in order to make the victim’s files inaccessible and demands ransom money from them. |
| Possible Symptoms | Performance degradation of system, other malware attacks, cyber theft, etc. |
| Detection / Removal Tool | Download Tizer78224 Ransomware Scanner to confirm the attack of Tizer78224 Ransomware virus. |
Research Report on Tizer78224 Ransomware
Tizer78224 Ransomware is a new file-encrypting virus which was reported on May 13th, 2018 by the security professionals. Based on the initial research report, the malware is propagated through spam email campaigns, macro-enabled malicious DOCX files and the intrusive links that leads system users to malware-laden web pages. This ransomware is identified as a new variant of previously detected RSAUtil Ransomware virus which was spotted over the Internet back in April 2017. Right after the previous version made its entry on the family of crypto-malware, the hackers update the core of this ransomware and the anti-virus programs detected the new update as ‘.Vendetta File Extension Ransomware‘ threat. Now, racketeers have updated the threat again and this time it is known as Tizer78224 Ransomware.

The name of this file-encoder virus is based on the email address ‘[email protected]’ that the hackers used to provide the victimized users for contact purpose. Through this email address, cyber criminals behind this ransomware provide complete details about the encryption procedure along with ransom payment details if the victim’s of Tizer78224 Ransomware uses this email to contact the threat actors. In addition to that, the malware also provide Bitcoin wallet address to the affected system users in order to transfer the asked ransom money in exchange for the decryption key needed for file restoration. This new strain of file-encrypting threat uses a different set of Command and Control server to connect the hackers to compromised machine remotely.
How Does Tizer78224 Ransomware Work?
The threat uses modified file-encryption algorithm in order to make the victim’s files inaccessible and demands ransom money from them. System files encoded by Tizer78224 Ransomware receives a string which follows ‘.[ransom_email].ID.’ model. Besides, the threat developers provide two additional email address identified as ‘[email protected]’ and ‘[email protected]’ to the compromised system users in order to contact the malware operators. What’s more, there are also various clones of this cyber threat that were reported to use different email addresses like:
After encoding the targeted system files, the Tizer78224 Ransomware displays a ransom note in the form of ‘How_return_files.txt’ file which urges affected users to contact the virus developers and ask them for decoding the infected data. However, you should not trust the team of cyber criminals behind this ransomware, because the main objectives of these threat actors to gain as much ransom money as possible without providing a right decryption key. Therefore, the restoration of enciphered files is not guaranteed even if you make the ransom payment. Hence, delete Tizer78224 Ransomware from system ASAP and try alternative method for file recovery.
Free Scan your Windows PC to detect Tizer78224 Ransomware
How To Remove Tizer78224 Ransomware Virus Manually
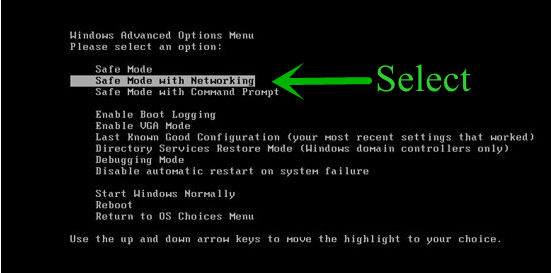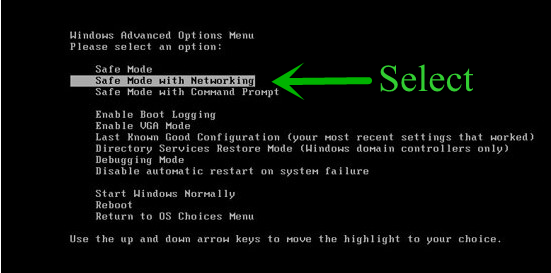
Step 1 : Restart your computer in safe with networking
- Restart your computer and keep pressing F8 key continuously.

- You will find the Advance Boot Option on your computer screen.

- Select Safe Mode With Networking Option by using arrow keys.
- Login your computer with Administrator account.
Step 2 : Step all Tizer78224 Ransomware related process
- Press the Windows+R buttons together to open Run Box.

- Type “taskmgr” and Click OK or Hit Enter button.

- Now go to the Process tab and find out Tizer78224 Ransomware related process.

- Click on End Process button to stop that running process.
Step 3 : Restore Your Windows PC To Factory Settings
System Restore Windows XP
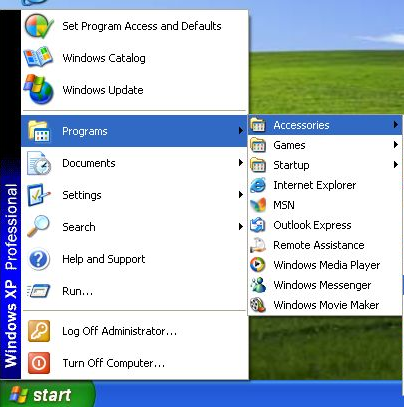
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
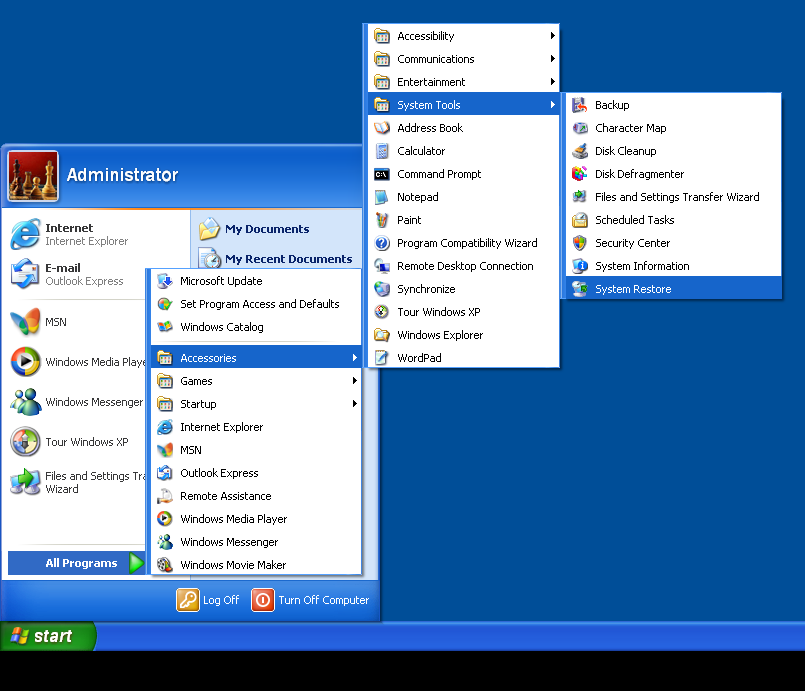
- Find System Tools and click System Restore.
- Select Restore my computer to an earlier time and click Next.
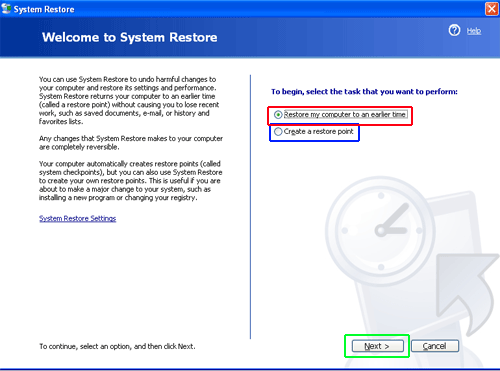
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results.
- From the System Restore window, click the Next button.
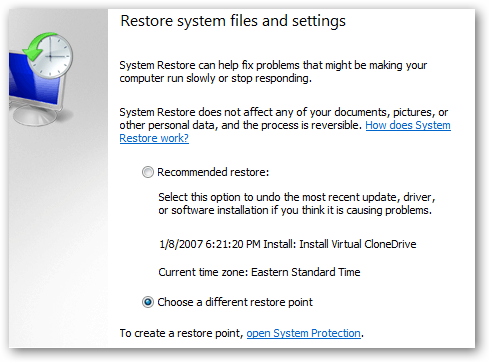
- Now select a restore points when your PC was not infected.
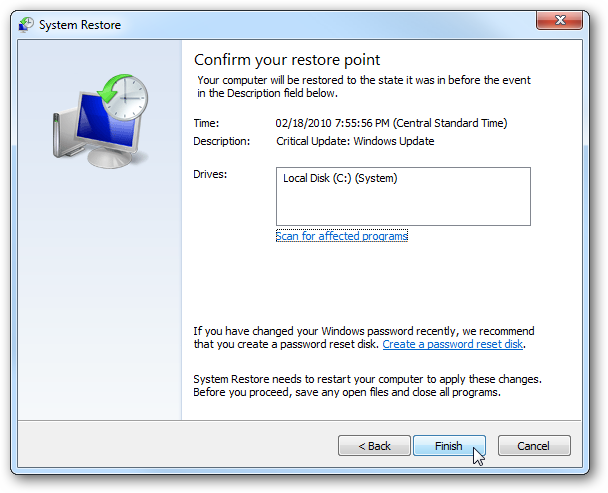
- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel.

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option.

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.
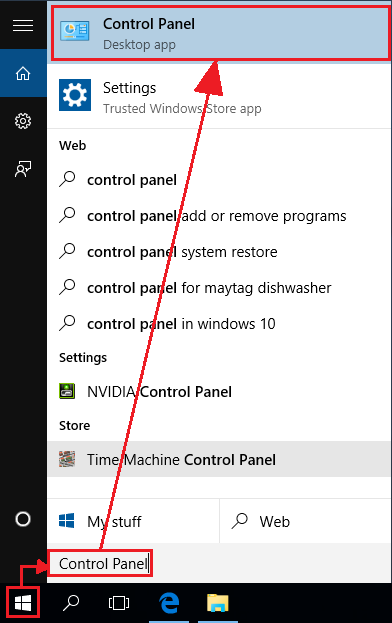
- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Hope these manual steps help you successfully remove the Tizer78224 Ransomware infection from your computer. If you have performed all the above manual steps and still can’t access your files or cannot remove this nasty ransomware infection from your computer then you should choose a powerful malware removal tool. You can easily remove this harmful virus from your computer by using third party tool. It is the best and the most easy way to get rid of this infection.
If you have any further question regarding this threat or its removal then you can directly ask your question from our experts. A panel of highly experienced and qualified tech support experts are waiting to help you.




