AutoEncryptor Ransomware – Needful Information
AutoEncryptor Ransomware is apparently created for either fun or scaring computer users by demanding 10,000 BTC as ransom which is currently equivalent to 11,769,800 USD. Till now $25,000 USD was the highest paid ransom amount on the planet earth. Such big ransom payment has never been paid before. However, you should note that AutoEncryptor Ransomware works as a file encoder virus and primarily targets English-speaking users around the the globe. But recent report reveals that it is targeting computer users who belong to Czech Republic and Slovakia users. It is true that the ransomware prevents users from decoding files by generating private key secured with a 256-bit AES cipher. This cipher is a military grade cipher so that once your files are encoded you won’t be able to recover them unless security experts don’t release a a free decryptor software or you use Data recovery software.
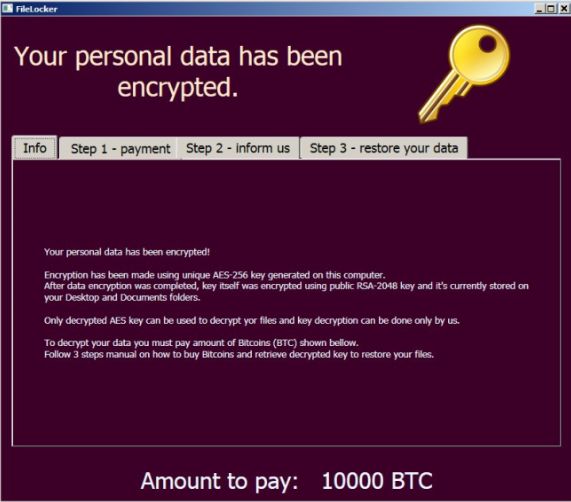
What is more worse, following successful data encryption, AutoEncryptor Ransomware immediately use another key generated in the process and secure the key with RSA-2048 algorithm. When you try to access or read your encoded files, all you get in response is error message like ‘Unable to open file’ or ‘File is not recognizes by Windows Explorer’ or ‘File is corrupted’. Futhermore, AutoEncryptor Ransomware make use of an unique table called FileLocker to show ransom note. The ransom note contains phishing text and suggest user to pay 10,000 BTC as ransom. Even, if a user want to get back files through purchasing the key, the ransom amount is extremely high. It will surely change your mind. Generally speaking, cyber punks are never trustworthy, even if you pay the ransom they will not deliver the data decryption key (aka Private key or Decryption key).
How to get back files without paying off ransom?
- Using Free Decryptor Tool – till date there was no free decryptor software released by AV vendors. So that we suggest you to keep search on Google as ‘Free Decryptor for AutoEncryptor Ransomware’.
- Using Data Recovery software – It might help you to recover your files in case Shadow volume copies are not permanently deleted by the AutoEncryptor Ransomware.
- Through System Restore – if you have created system restore point before then you can use it for restoring your computer to an earlier date when it was not compromised with the ransomware. Detailed information regarding the data recovery is provided in data recovery section below.
As of now, it is essential to note that licensed version Antivirus always provide real time protection to your computer. Even, operate operating system block infiltration of malware. Such virus invade computer via spam emails that contains malicious attachment (actually payload or exploit kit). So, do not double click spam emails attachments at all. Follow the provided instruction to uninstall AutoEncryptor Ransomware and get back your files:
Free Scan your Windows PC to detect AutoEncryptor Ransomware
Remove AutoEncryptor Ransomware From Your PC
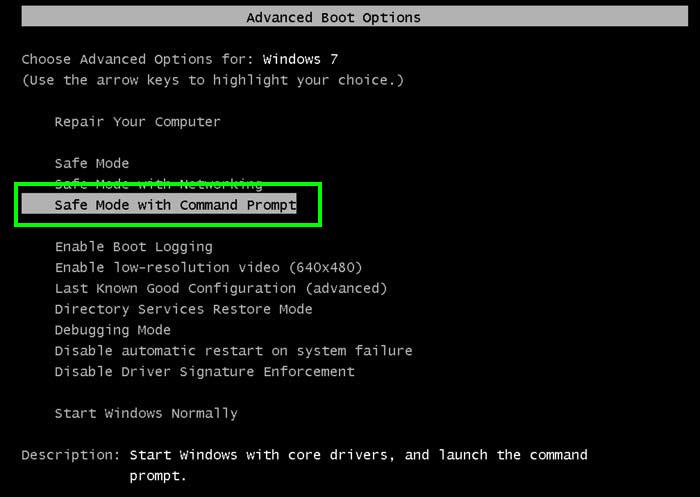
Step 1: Remove AutoEncryptor Ransomware in Safe Mode with Command Prompt
- First of all disconnect your PC with network connection.
- Click restart button and keep pressing F8 key regularly while system restart.

- You will see “Windows Advanced Options Menu” on your computer screen.
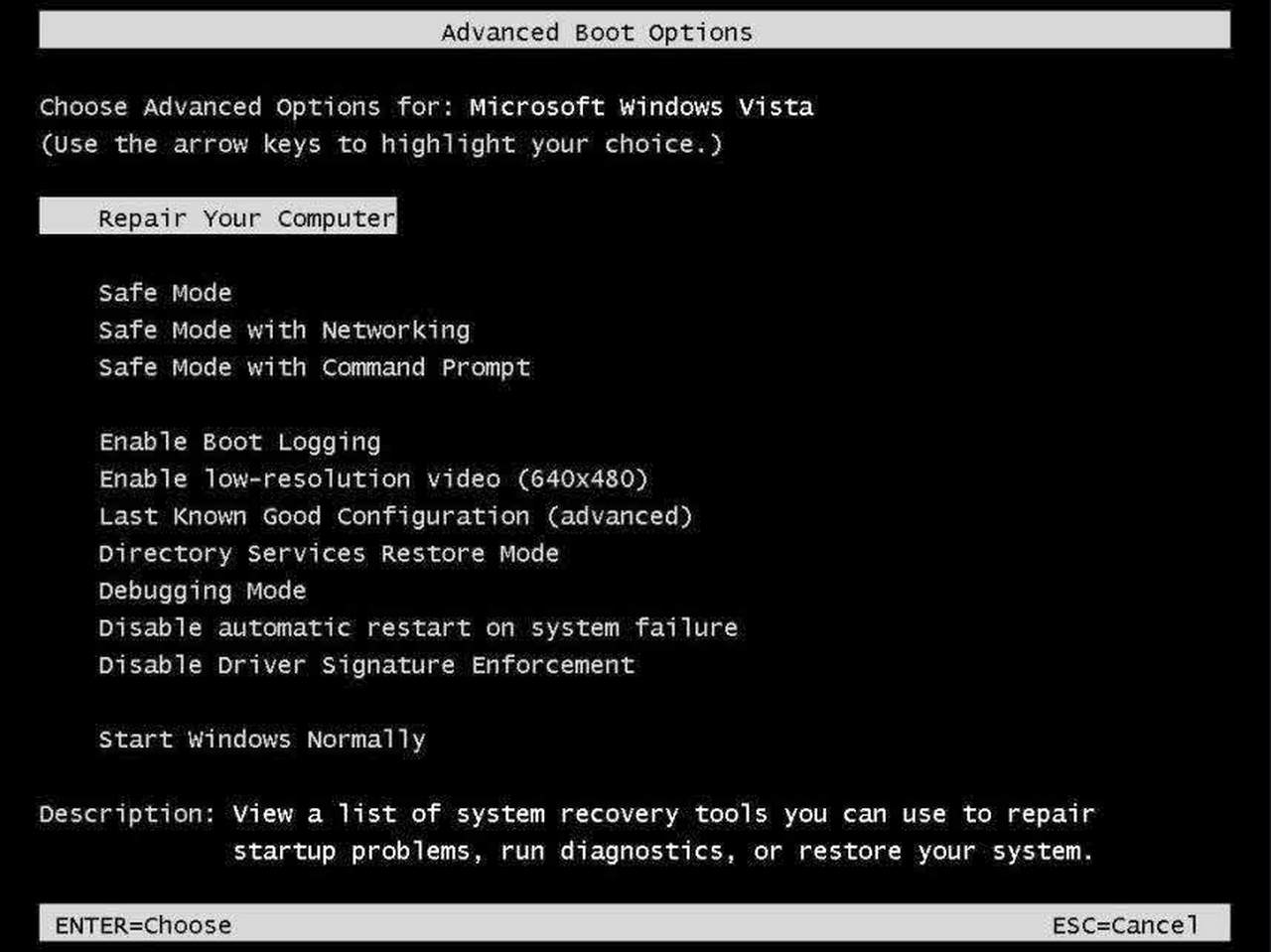
- Select “Safe Mode with Command Prompt” and press Enter key.
- You must login your computer with Administrator account for full privilege.
- Once the Command Prompt appears then type rstrui.exe and press Enter
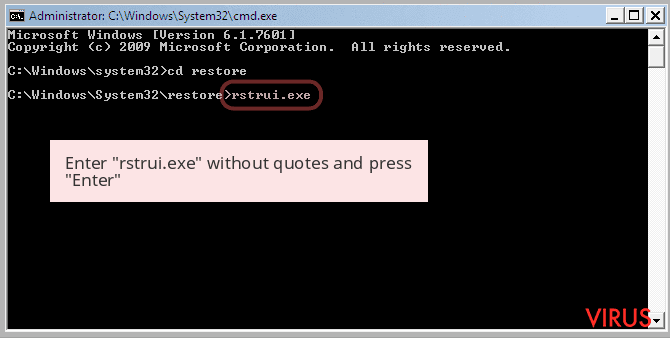
- Now follow the prompts on your screen to complete system restore.
Step 2: Remove AutoEncryptor Ransomware using MSConfig in Safe Mode:
- Power off your computer and restart again.
- While booting press the “F8 key” continuously to open “Windows Advanced Options Menu”.

- Use the arrow keys to select “Safe Mode” option and press Enter key.

- Once system get started go to Start menu. Type “msconfig” in the search box and launch the application.
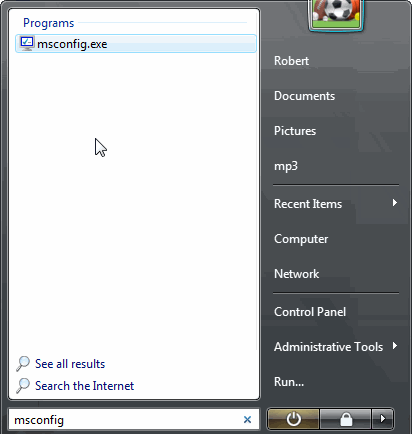
- Go to the Startup tab and look for files from %AppData% or %Temp% folders using rundll32.exe. See an example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N1
- Disable all the malicious entries and save the changes.
- Now restart your computer normally.
Step 3 : Kill Malicious Process Related To AutoEncryptor Ransomware
- Press Alt+Ctrl+Del buttons together.

- It will open the Task manager on your screen.
- Go to Process Tab and find AutoEncryptor Ransomware related process.
- Click the End Process Now button to stop the running process.
Step 4 : Remove AutoEncryptor Ransomware Virus From Registry Entry
- Press “Windows + R” key together to open Run Box.

- Type “regedit” and click OK button.

- Find and remove AutoEncryptor Ransomware related entries.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Runonce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
Now hopefully you have completely removed the AutoEncryptor Ransomware virus from your computer. If you are still get ransom message from the threat or unable to access your files, then it means that virus still remain into your computer. In such situation you don’t have any other option except removing this virus using any powerful malware removal tool.
Whereas if you have any backup of your infected or encrypted files, then you can also reinstall your Windows OS. This will erase all your files and data as along with the AutoEncryptor Ransomware infection. You will get a completely empty computer system with no files. Now you can use your backup to get your files. If you don’t have any backup then using malware removal tool is a better option for you.
If you have any query or question regarding your computer, then you can easily ask your problem to our experts. Go to the Ask Any Question page and get the answer for your query directly from out experts.




