| Warning, many anti-virus scanner have detected Ijikpvj ransomware as threat to your computer | ||
| Ijikpvj ransomware is flagged by these Anti Virus Scanner | ||
| Anti Virus Software | Version | Detection |
| TrendMicro-HouseCall | 2018.0.9817 | Common |
| Ikarus | 5.4.824307 | Trj.Win32.Ijikpvj ransomware.CC |
| Ad-Aware | 4.144543 | Variant of Win32/Trojan.Ijikpvj ransomware.C |
| ZeroCERT | 7.0.101 | Yazzle Cowabanga, Dpevflbg Toolbar |
| Suggestion: Uninstall Ijikpvj ransomware Completely – Free Download | ||
Ijikpvj ransomware may have entered your pc through these software. If you have not installed them , then get rid of them Newegg for iPad 1.0.3 , Kill Monty 1.1 , Easy Mortgage 1.0 , DataVault Password Manager 5.3.47 , A Better Finder Rename 9 24 , SmartBook 1.0.2 , The Search for Amelia Earhart 1.0M , Squares2 1.0.1 , Postage $aver 8.12.3 , Mystery Trackers: Silent Hollow CE 1.0 , Splice 1.0 , JEME 1.3.0 , USB Overdrive 3.1 |
|

Detailed Report On Ijikpvj ransomware
Ijikpvj ransomware is a file encrypting malware that has been based upon an open source Ransomware. It is capable of encrypting various file formats which can make those files unusable unless they are decrypted using a private decryption key. The ransomware has been found to be using strong encryption key and immediately stores the decryption key on remote servers. Ijikpvj ransomware has been identified to deceive users by means of spam mails and software bundles to spread itself. The spam mails are specially crafted to catch receiver’s attention as they carry details such as product information, invoice, purchase order, banking update and such with names of reputed firms. The contents give an impression of legitimacy and asks users to click on links provided within the text to obtain more information. These links are used to inject scripts that allows the payload to download itself and start the encryption process. Ijikpvj ransomware can also use software bundles to hide itself as legitimate archive files in .rar or .zip format. The files then get executed during installation process along with other applications. The ransomware has been designed to scan the system and identify important files that need to be encrypted. It can also make changes to operating system’s registry that allows it to launch itself at system’s reboot. It has been identified to make changes to Run and RunOnce registry keys. The ransomware drops its payload in various sub directories of the system and hence can be difficult to detect manually.
Ijikpvj ransomware soon starts its encryption process after identifying important files within the system. It has been found to be using AES-128 and RSA-2048 encryption algorithm to encrypt files and immediately sends the decryption key to remote servers. The files that get encrypted can be identified with long strings that contain random letters and characters and end with an extension. It drops a ransom message in a file that displays the content regarding the attack. Ijikpvj ransomware informs users that their files can only be recovered using a special software and unique decryption key that can be obtained by contacting them to negotiate a deal regarding the ransom amount. To gain trust of affected users Ijikpvj ransomware asks them to attach three encrypted files that will be decrypted. If not contacted within seven days the unique decryption key will be deleted from remote server. However users should not contact them and instead can follow these steps to remove the ransomware from their PC.
Free Scan your Windows PC to detect Ijikpvj ransomware
A: How To Remove Ijikpvj ransomware From Your PC
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.
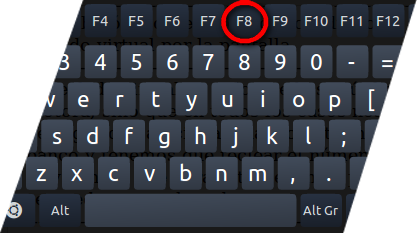
- From the boot menu, select Safe Mode with Networking using the arrow keys.
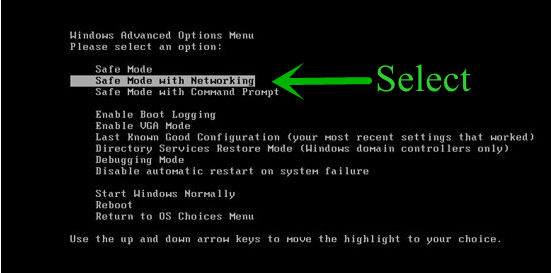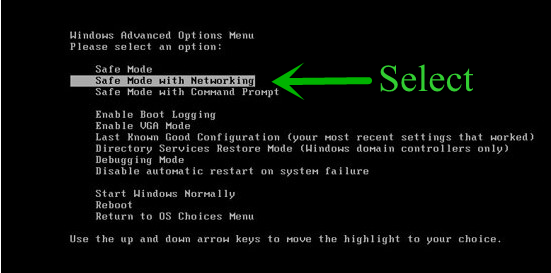
Step: 2 How to Kill Ijikpvj ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the Ijikpvj ransomware related Process.
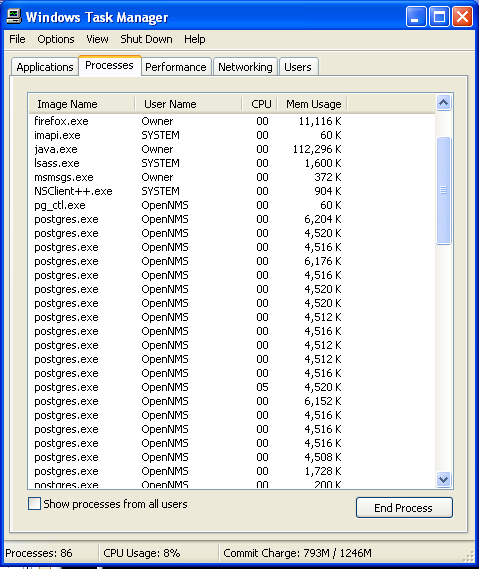
- Now click on on End Process button to close that task.
Step: 3 Uninstall Ijikpvj ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
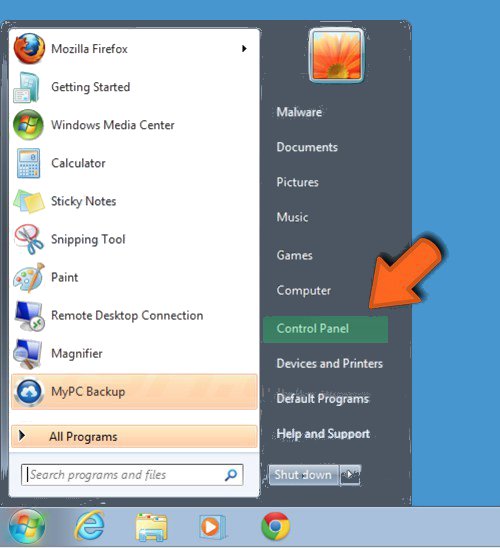
- Select Uninstall a Program option from Program category.
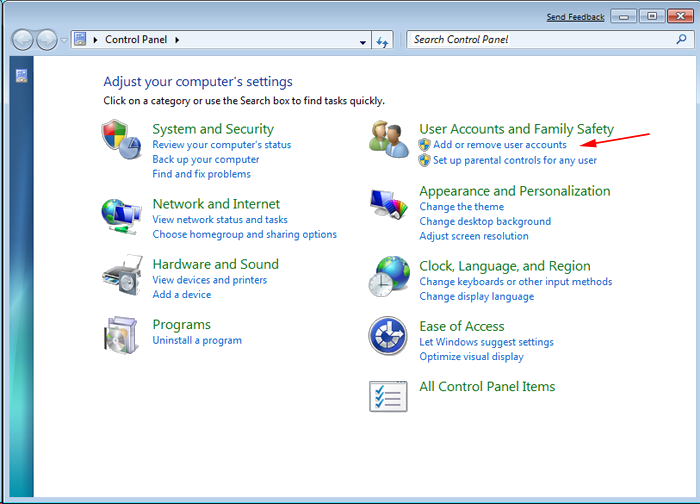
- Choose and remove all Ijikpvj ransomware related items from list.

B: How to Restore Ijikpvj ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing Ijikpvj ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
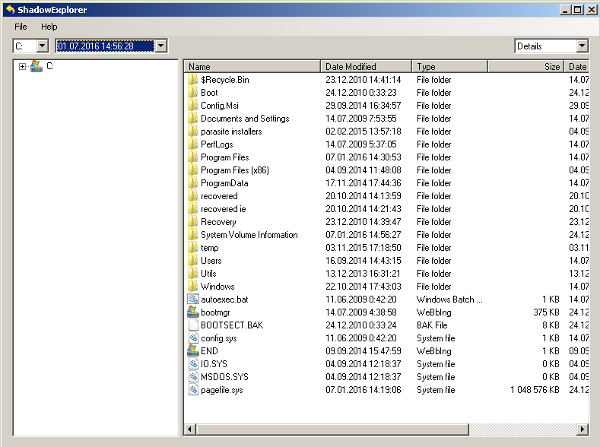
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing Ijikpvj ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
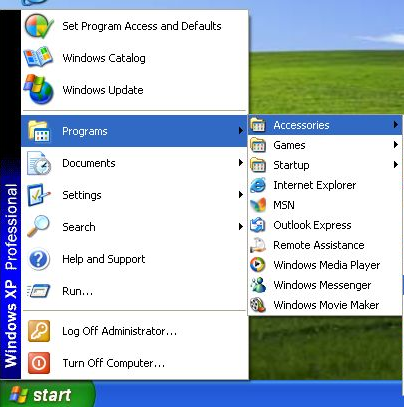
- Find System Tools and click System Restore
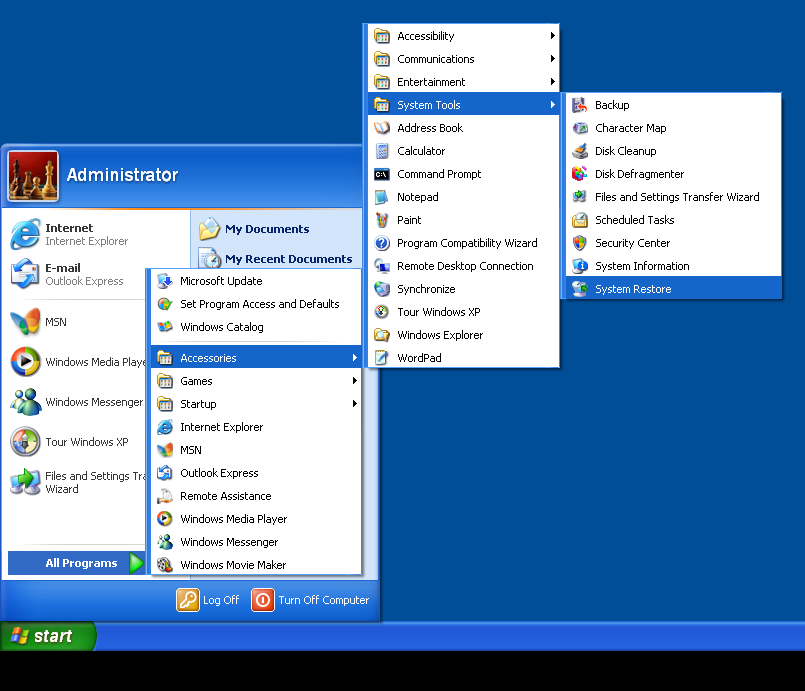
- Select Restore my computer to an earlier time and click Next.
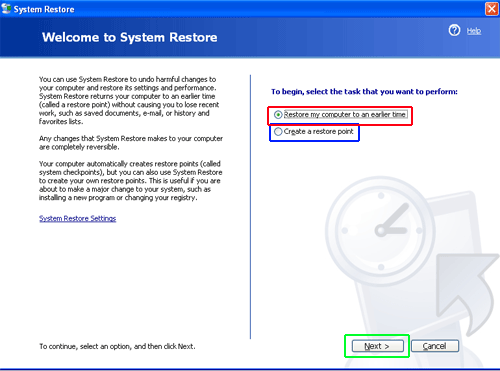
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by Ijikpvj ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.

