A new strain of file-encoder virus named ‘GandCrab Ransomware’ has been reported by the cyber security experts on the last week of January, 2018. Instead of using typical ransomware distribution technique, this time the hackers behind the malware using a pair of malicious exploit kits i.e. GrandSoft and RIG EK in order to infect user’s machine unknowingly. In most of the cases, threat actors uses this type of deceptive technique to spread Trojan downloaders, Cryptocurrency miners, RATs and other destructive Trojan viruses that are opposed to hazardous ransomware threats.

According to the malware researchers, it is more interestingly that the ransomware viruses were spotted delivering through exploit kits. Although, other interesting fact about GandCrab Ransomware is that the exploit kits that were used to proliferate this ransomware named RIG and GrandSoft EK are recognizably different in nature. However, it is still not clear that same group of threat actors is behind the both distribution campaigns and experimenting the propagation of GandCrab Ransomware with two different distribution channels.
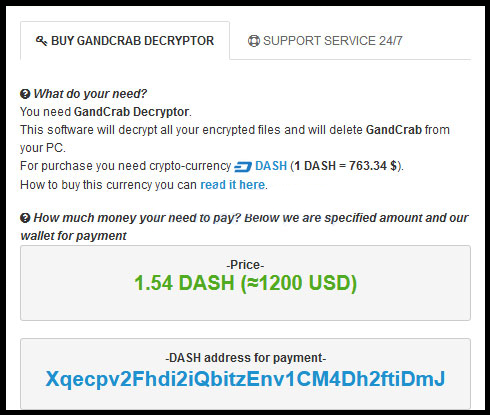
After the successful invasion of GandCrab Ransomware on victim’s machine, the malware displays a ransom notification and allows the victimized computer users to decrypt one file for free which works as a proof of legitimacy. It appends the encoded file name by adding a weird extension ‘GDCB’ onto every enciphered file name. Furthermore, the operators of this ransomware demands ransom money from the affected users and instructs them to pay through Dash cryptocurrency. The threat asks for 1.5 Dash which is approximately equal to 755 USD based on current exchange rate.
Technically speaking, the malicious server of GandCrab Ransomware is hosted on ‘.bit’ domain which is served through cryptocurrency Namecoin infrastructure. The well-prepared and obfuscated malvertising campaign is pushing RIG exploit kit to spread this newly developed file-encrypting virus all across the world. Although, the same process have been used by the cyber extortionists in order to propagate Ramnit Trojan. The involvement of the second exploit kit i.e. GrandSoft is more surprising because this exploit kit was thought to have all but suddenly disappeared.
Related Article: New Alma Locker Ransomware being distributed via RIG Exploit Kit
Once the malicious payload of GandCrab Ransomware gets executed onto the targeted machine, the threat also gathers important information about the infected device, such as system name, installed operating system and its version, user name, pre-installed anti-virus program, computer language and active drives. It also checks the keyboard layout to identify whether it is Russian in nature or not, it if finds the same, then the malware avoid encoding the files saved on such machines. Moreover, the collected information may be delivered to a command and control server. GandCrab Ransomware uses RSA ciphers to encrypt system’ files and generate public and private keys. According to the experts, decryption of affected files might be possible by pulling the keys from memory.
