Gandcrab Ransomware Targets MySQL Servers
Gandcrab Ransomware has been spotted once again but this time it was a part of campaign targeting MySQL Servers on Windows over internet. As reported it has been found that Gandcrab virus is targeting Windows server by injecting malicious DLL files to attack SQL database. Such DLL files are capable to invoke and increase payload on server manifolds. The attack is activated after Windows executable file is downloaded on United States based Windows PC.
Since most of the MYSQL database servers are password protected by system admin so hackers are targeting servers that are misconfigured or which are not password protected. However this attack has been tracked only using remote server which was based as a directory running on open server. What more, it was observed that malicious payload was increased many times after the malicious DLL file was downloaded as Windows executable files.
Gandcrab Ransomware Is Capable To Steal User’s Data
As many as 500 or more downloads were indicated as samples but file samples named as 3306-2.exe, 3306-3.exe and 3306-4.exe were reported to be somewhat identical to honeypot download 3306-1.exe. over 800 downloads were reported in period of 5 days and up to 2300 downloads were reported within 7 days confirmed injection of GandCrab Ransomware as open directory. Actually such attacks are not very common and is very rare and has been carried out to target and steal data from SQL servers by injecting crypto mining malware such as GandCrab Ransomware.
The Campaigns of Gandcrab Ransomware

GandCrab Ransomware is not a newly discovered ransomware. Yes, you heard right, it holds about 40% share of ransomware market that spreads using several form of attack including exploit kit, social media campaign, MS office documents, hacked domain, pirated software, contaminated devices and many more. Undobtedly, it uses several campaign but the latest campaign of this ransomware targets MySQL server on Windows PC.
Such a ransomware attck starts on user’s machine by injecting the malicious dynamic link library file to database server. It actually uses the command of SQL database and then after invoke DLL file to get the payload of ransomware hosted of attacker’s server. After infecting files, it immediately initiate the file encryption procedure.
Infection Mechanism of Gandcrab Ransomware
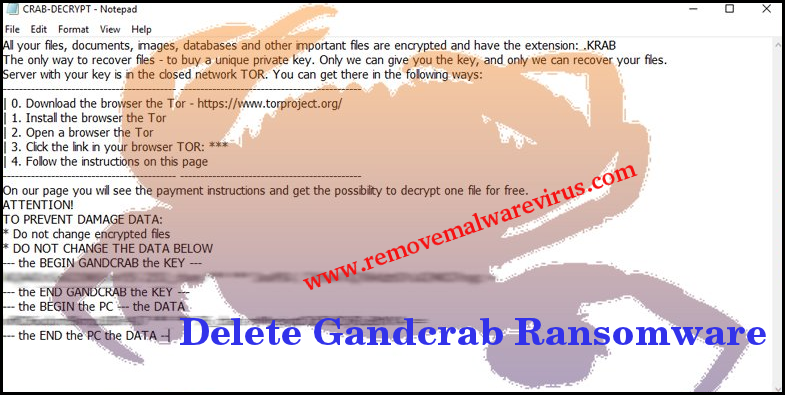
GandCrab Ransomware comes in several version but all version uses AES 256 and RSA 2048 algorithm to lock user’s data and file. It uses unique file extension to rename the targeted files but some of it’s detected file extension are .crab, .gdcb, .lock, .krab and much more. After locking files, it drops a ransom note and asks victim for ransom payment. But you should never believe on ransom note because it is not trustworthy at all. To get back your all valuable files, first of all you must get rid of GandCrab Ransomware from your contaminated machine.
About Author : Richard Herry
Hey, I am Richard Herry and the goal of my life is to inform user’s about the all latest malware, virus as well as security alert and provide an appropriate solution through which they can make their PC malware free. So, I have created my own site named removemalwarevirus.com where System user will know an easy and appropriate solution to get rid of malware. This site is dedicated to cover all topic related to malware and includes an easy instruction so that it can be handled by any novice users without any hesitation.
