| 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 is a Backdoor | |
| Trojan Dropped by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 are IRC-Worm.Wun, I-Worm.Nimrod, Mal/FakeAV-PY, Tiny Trojan Loader, Trojan-Downloader.Agent-OL, Email.Brontok.q, Trojan.Warserhost.A, Email.VB.fp, MonitoringTool:Win32/AutoKeylogger, Trojan.Multis, Herpes, Win32/spy.delf.oxi, RingZero Trojan | |
| Related spyware TDL4 Rootkit, WebHancer.A, GURL Watcher, Rogue.Virus Response Lab 2009, DoctorVaccine, SniperSpy, Mdelk.exe, Rogue.ProAntispy, SafeStrip, VirusSchlacht, InternetAlert, LympexPCSpy | |
| Windows Error caused by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 are – 0x00000119, 0x000000F9, 0xf0814 CBS_E_INVALID_CONFIG_VALUE invalid setting configuration value, 0x8024800F WU_E_DS_STOREFILELOCKED The data store could not be initialized because it was locked by another process., 0x8024D007 WU_E_SETUP_REGISTRATION_FAILED Windows Update Agent could not be updated because regsvr32.exe returned an error., 0x00000018, 0x00000039, 0x00000053 | |
| 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 infects these windows .dll files rescinst.dll, tsddd.dll, FXSMON.dll, odexl32.dll, GdiPlus.dll, hhsetup.dll, PTRes.dll, Microsoft.PowerShell.Commands.Management.ni.dll, dpnathlp.dll, eventcls.dll |
1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 may have entered your pc through these software. If you have not installed them , then get rid of them LightTable 1.0.2 , EvoCam 4.2.4 , WaterRace Updater 1.0.3 , Grackle Probe X 1.4 , Ripcord 1.0b15c10 , Cor.kz Wine Info 1.0 , Baby Health Journal 1.0.2 , Subtitles theEditor 1.14 , EasyCatalog CS5 5.0.3 , SimpleDigitalLocomotive 0.74 , Mrs. Owl’s Learning Tree 3.1 , NetAppraiser X 4.0 , SplashCase 1.1 , Shortcat 0.7.3 , Animals Coloring Book 1.0 |
|

(Updated Guide!) 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 Removal From Affected PCs
Facts Worth Knowing About 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1
1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 is a dangerous Trojan which is currently used by the criminal hackers for various illicit purposes. You may find various features which is available in reliable remote desktop management tools in this malicious Trojan virus. In most of the cases, the malware infects the targeted user’s system manually by employing a deceptive social engineering tactic. Some of the bogus tools like hacking programs, fake account on popular social networking websites, and unreliable computer security alerts may be used by the team of criminal hackers in order to convince system users into running the client application of 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 threat.
In order to perform various harmful actions and gain remote access to the compromised systems, the hackers behind this malware uses a command and control server operated by them to perform illicit tasks onto the affected machines. According to cyber security analysts, 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 virus is available onto the Dark Web for free and also stated to include various supports.
Malicious Properties Of 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 Malware
Based on the recent research report published by the team of security investigators, this Trojan is equipped with keylogger feature which allows 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 to capture keystrokes on the victim’s system and may display the screen-locker message as well. In addition to that, microphone and camera can also be turned on due to the fact that your system is remotely accessed by the racketeers to perform such illicit tasks. As a result, the victims of this malware can be under surveillance without their consent.
Cyber criminals responsible for such vicious attacks can use their malicious creations to hide their Internet traffic, steal confidential data like credit card details, login credentials, personal information and family photos for bad purposes. After the attack of 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 virus, infected computer users may notice the unavailability of Windows closing and crucial files on their disks. One may also notice the various unfamiliar tasks running onto the Windows Task Manager. Therefore, it is strongly recommended to take immediate action for the removal of 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 from the machine using a powerful anti-malware shield.
Steps to Remove 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1
Step 1>> How to Boot Windows in Safe Mode to isolate 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1
Step 2>> How to View Hidden Files created by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1
for Windows XP
- Exit all Program and Go to Desktop
- Select My Computer icon and Double Click to Open it
- Click on the Tools Menu and now select and Click on Folder Options.
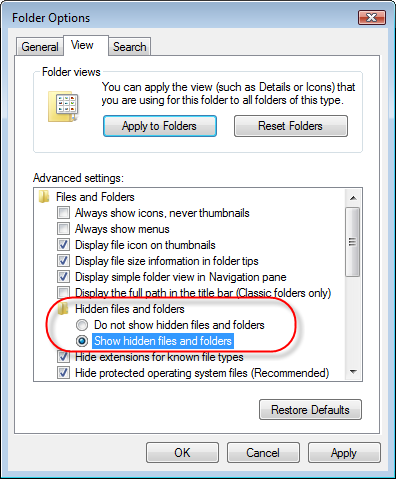
- Select on View Tab that appears in New Window.
- Check mark on the box next to Dispaly the Contents of System Folders
- Now Check the box in order to Show Hidden Files and Folders
- Now press on Apply and OK to close the Window.
- As soon as these steps are performed, you can view the files and folders that were created by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 and hidden till now.
for Windows Vista
- Minimize all Window and Go to Desktop
- Click on the Start Button which can be found in lower lef Corner having Windows Logo
- Click on the Control Panel on the Menu and Open it
- Control Panel can be opened in Classic View or Control Panel Home View.
- If you have Selected Classic View, follow this
- Double Click on the Folder icon to open it
- Now select the view tab
- Click on Option to Show Hidden Files or Folders
- If you have Selected Control Panel Home View, follow this
- Appearance and Personalization link is to be Clicked
- Select on Show Hidden Files or Folders
- Press Apply Option and then Click on OK.

This will Show all the Folders including those created by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1
Know how to view Hidden Folders on Windows 7, Win 8 and Windows 10
(Following the above steps are necessary to view all the files created by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 and that is known to exist on Compromised PC.)
- Open the Run Box by holding together the Start Key and R.

- Now Type and input appwiz.cpl and press on OK
- This will take you to the Control Panel, Now Search for Suspicious programs or any entries related to 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1. Unistall it once if you happen to find it. However be sure not to Uninstall any other program from the list.
- In the Search Field, Type msconfig and press on Enter, this will pop-up a Window

In the Startup Menu, Uncheck all the 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 related entries or which are Unknown as Manufacturer.
Step 3>> Open the Run Box by Pressing Start Key and R in Combination
- Copy + Paste the following Command as
- notepad %windir%/system32/Drivers/etc/hosts and press on OK
- This will Open a new file. If your system has been hacked by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1, certain IP’s will be displayed which can be found in the bottom of the screen.
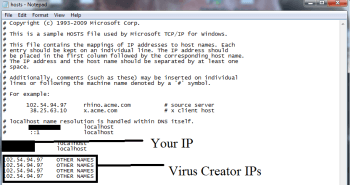
Look for the suspicious IP that is present in your Localhost
Step 4>> How to Terminate 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 Running Processes
- Go the Processes Tab by pressing on CTRL+SHIFT+ESC Keys Together.
- Look for the 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 Running Processes.
- Right Click on 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 and End the Process.

Step 5>> How to Remove 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 Related Registry Entries
- Open Registry by Typing Regedit in the Run box and Hit Enter Key
- This will open all the list of entries.
- Now Find and search the entries created by 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 and cautiously delete it.
- Alternatively, you can manually search for it in the list to delete 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1 Manually.
Unfortunately, if you are unable to remove 1GSp8Kmjo54VvH1fRzgF2jcxL9cwPtzvH1, Scan your PC Now
Also submit question and let us know in case you are having some doubt. Our Experts will definitely respond with some positive suggestions for the same. Thanks!


