| Warning, many anti-virus scanner have detected [email protected] Ransomware as threat to your computer | ||
| [email protected] Ransomware is flagged by these Anti Virus Scanner | ||
| Anti Virus Software | Version | Detection |
| Symantec Mobile Insight | 2018.0.1129 | General |
| Comodo | 6.0.649844 | [email protected] Ransomware.CB |
| Avast-Mobile | 3.435337 | Variant of Win64/[email protected] Ransomware.B |
| Trustwave | 4.5.425 | Backdoor.Win32.IRCNite.c, Look2Me Adware |
| Suggestion: Uninstall [email protected] Ransomware Completely – Free Download | ||
[email protected] Ransomware may have entered your pc through these software. If you have not installed them , then get rid of them KeyBoardLauncherX 5.1.1 , Avogadro2 0.7.2 , FlySwatter 1.0.3 , TalaPhoto 2.8.8 , Postage $aver 8.10.5 , Photomatix Pro 5.0.4 , Miro 6.0 , Ainsoft MOV Video Converter , LogTen Pro 6.5.1 , Permissions Reset 1.0 , Sticky Password 8.0 , Token 1.3.1 |
|

[email protected] Ransomware : Know About It’s Detailed Information
[email protected] Ransomware is another member of its famous Ransomware family that uses the source code of original one. The original ransomware is really one of the oldest ransomware that comes with several variant and infect wide range of Windows PC. This ransomware has a list with about 126 file extensions to lock users files. The System files locked with its file extension is a clear evidence that Systems are contaminated with [email protected] Ransomware. It is crafted and designed by security analysts in such a way that it can infect almost all System executing on Windows Operating System.
Dispersal Methods Of [email protected] Ransomware
[email protected] Ransomware is determined as one of the most notorious ransomware infection which is very intrusive and invasive in nature. The developers of this ransomware uses lots of deceptive and tricky methods to compromise windows machine but mainly it is dispersed through corrupted MS Word files and spam emails. System users usually invited to load the fake invoice. Once System user load any fake invoice or download any corrupt attachment then their PC easily get victimized by this ransomware. Besides spam campaigns, it also compromises users PC via infected devices, P2P file sharing sources, corrupt documents, pirated software, drive-by-downloads, bundling method and many more.
Behavior Of [email protected] Ransomware
Once [email protected] Ransomware gets installed in users PC successfully, a background procedure may appear in Windows Task Manager and displays an updated service. First of all, it disables firewall settings and stop the function of security measure so that affected users cannot easily detect and delete [email protected] Ransomware from their PC. After that it immediately initiate the file encryption procedure. It encodes users almost all stored file types such as audio or video clips, images, documents, databases, PDFs, presentations, eBooks and many more. The affected users files may easily be identified because it adds file extension.
After performing the successful file encryption procedure, it displays a ransom message as a command line window. The ransom note includes information about [email protected] Ransomware attack and asks victims to make contact with its developer in order to get the unique decryption key and decrypt files. But team of security analysts are strictly warned victims to not believe on ransom message because it is just only a tricky thing created by hackers to trick users and earn online money from them. Instead of paying ransom demanded fee, affected System users must take an immediate [email protected] Ransomware removal guide to delete them.
Free Scan your Windows PC to detect [email protected] Ransomware
A: How To Remove [email protected] Ransomware From Your PC
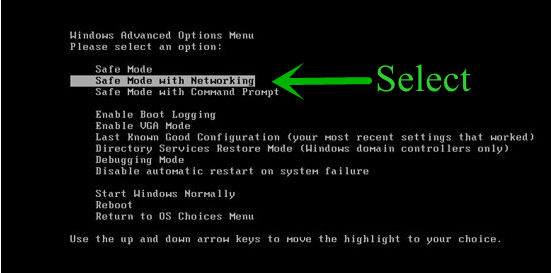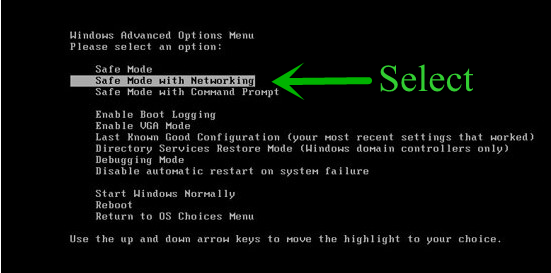
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.
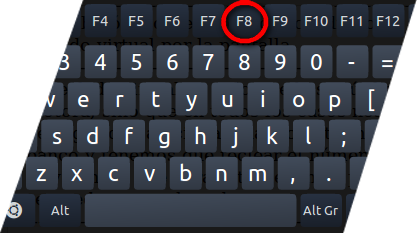
- From the boot menu, select Safe Mode with Networking using the arrow keys.
Step: 2 How to Kill [email protected] Ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the [email protected] Ransomware related Process.
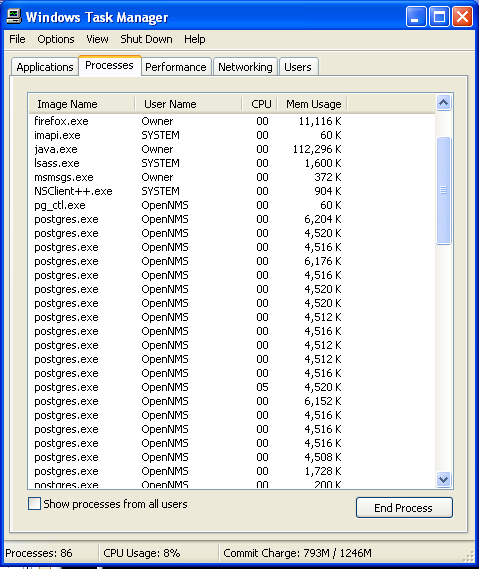
- Now click on on End Process button to close that task.
Step: 3 Uninstall [email protected] Ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
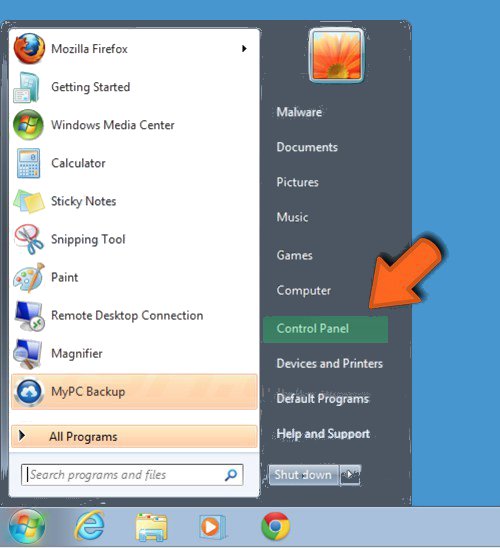
- Select Uninstall a Program option from Program category.
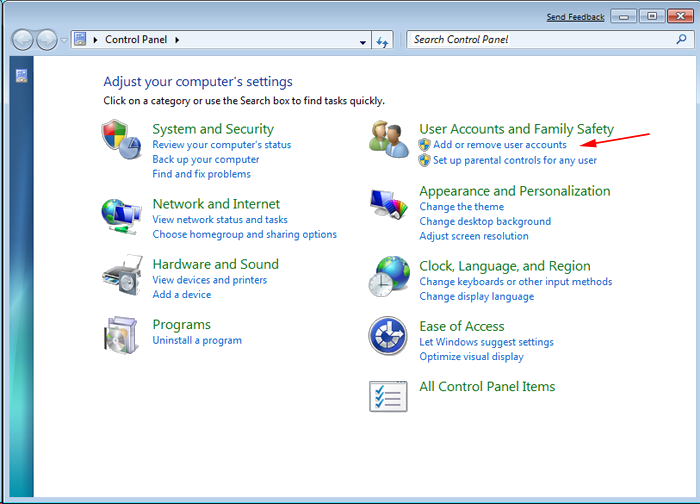
- Choose and remove all [email protected] Ransomware related items from list.

B: How to Restore [email protected] Ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing [email protected] Ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
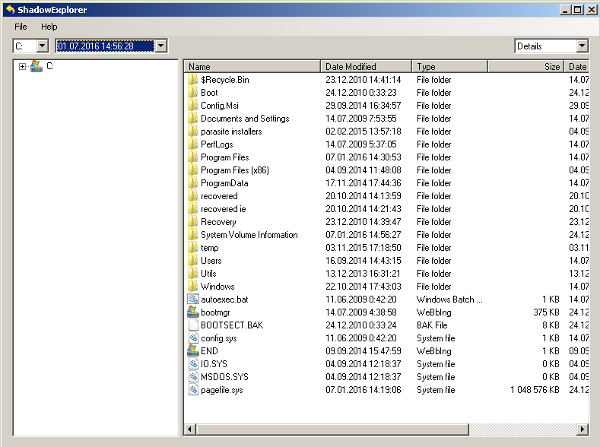
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing [email protected] Ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
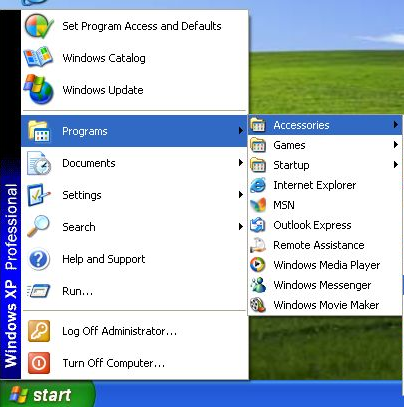
- Find System Tools and click System Restore
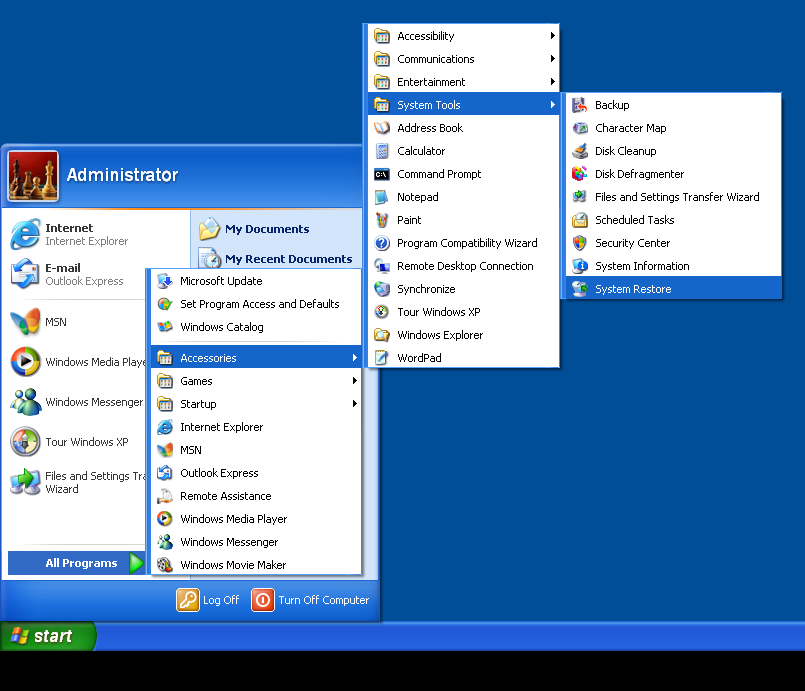
- Select Restore my computer to an earlier time and click Next.
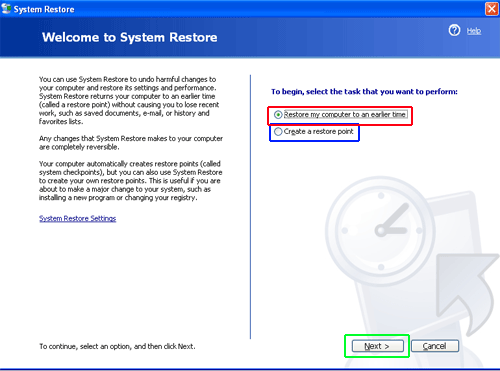
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by [email protected] Ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.

