Technical Information on Jhash Ransomware
Jhash Ransomware is yet another creation of criminal hackers based on the leaked code of HiddenTear ransomware project and belongs to the family of crypto malware. It was reported by the security researchers on November 8th, 2017 for the very first time. The threat is especially programmed to target the system users located in Venezuela. Based on the limited defense capabilities of the computer users and ongoing economic crisis at Venezuela may be seen as an advantage to spread the malware and infect the targeted users. Talking about the distribution of this malware, the malicious payload of Jhash Ransomware may be arrived to user's spam email box as an attached macro-enabled file which pretends to be appeared from local banking institutions and service suppliers. However, opening the attached file leads to the invasion of this hazardous ransomware on your targeted system.
Furthermore, the computer users who have been affected with this malware might find that their valuable data like videos, pictures, spreadsheets, presentations, texts, eBooks, audio, and databases will be enciphered. Cyber security experts alert that it is quite impossible to decode the files encrypted by Jhash Ransomware at the time of writing this article. However, after successfully encoding the affected PC files, the malware appends the enciphered file name with '.locky' extension. The file extension used by this ransomware is in active use by many file-encoder viruses, but it was first used by the Locky ransomware for the first time in such vicious cyber attack. All the targeted data is encoded with the help of personalized AES-256 cipher and the decryption tool is encoded using RSA-2048 cipher just for an added layer of security. All type of communications made by Jhash Ransomware are relayed via Tor2Web services in order to remain anonymous for the security researchers.
Consequences Related with Jhash Ransomware
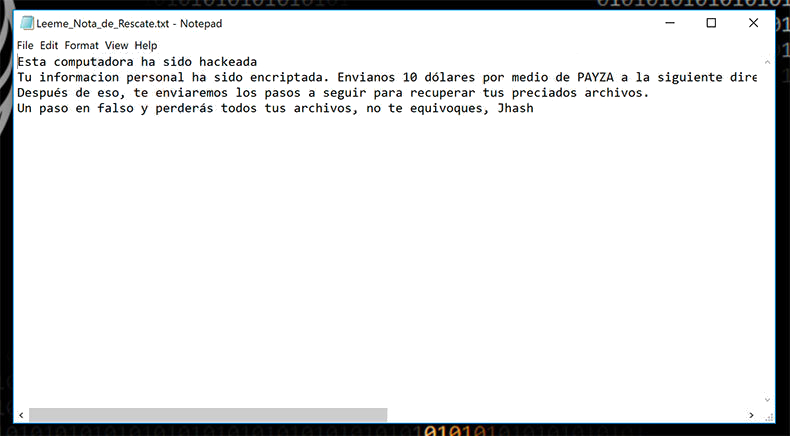
Once it encrypts the file stored on affected computer, it displays a ransom notification identified as 'Leeme.txt' in a Spanish language and in English it means 'Readme.txt'. The computer users affected with Jhash Ransomware may find this ransom note onto their system's desktop. According to the cyber security analysts, the team of cyber extortionists behind this malware have been abused the Payza payment platform which has good reputation in Venezuela. Meanwhile, it is strongly recommended by the security researchers to avoid paying ransom money asked by the operators behind this ransomware. In this kind of situation, you should delete Jhash Ransomware completely from your machine by using a credible anti-malware scanner and use backup copies for data restoration.
Free Scan your Windows PC to detect Jhash Ransomware
Free Scan your Windows PC to detect Jhash Ransomware
A: How To Remove Jhash Ransomware From Your PC
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
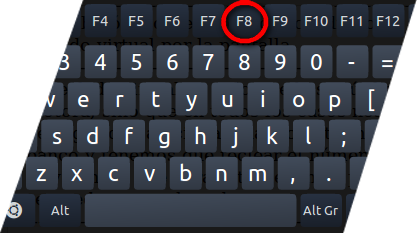
- Press and hold down the F8 key during the restart process.
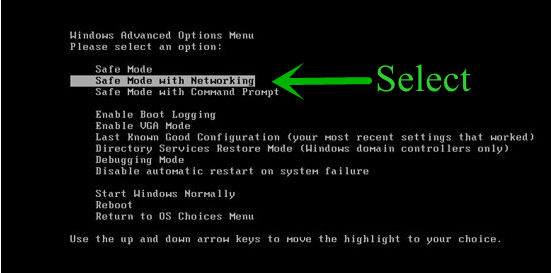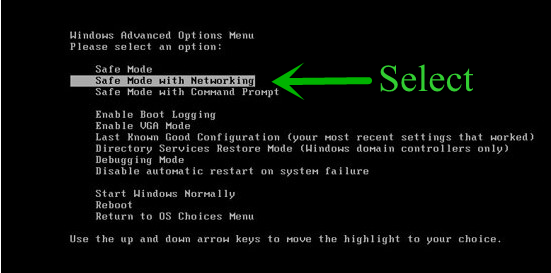
- From the boot menu, select Safe Mode with Networking using the arrow keys.
Step: 2 How to Kill Jhash Ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the Jhash Ransomware related Process.
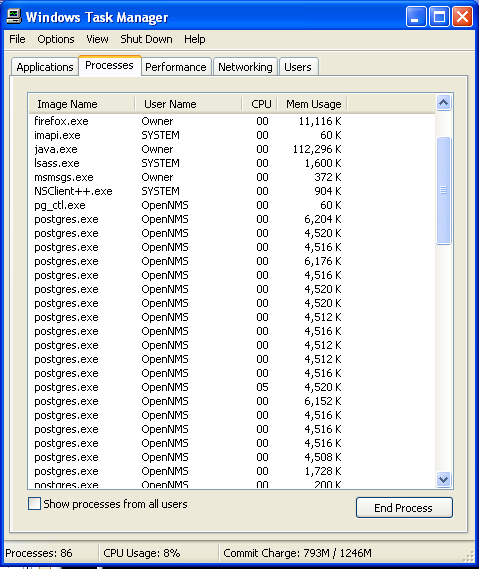
- Now click on on End Process button to close that task.
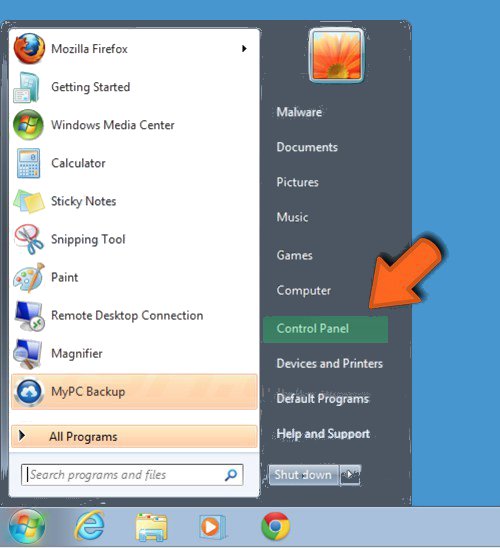
Step: 3 Uninstall Jhash Ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
- Select Uninstall a Program option from Program category.
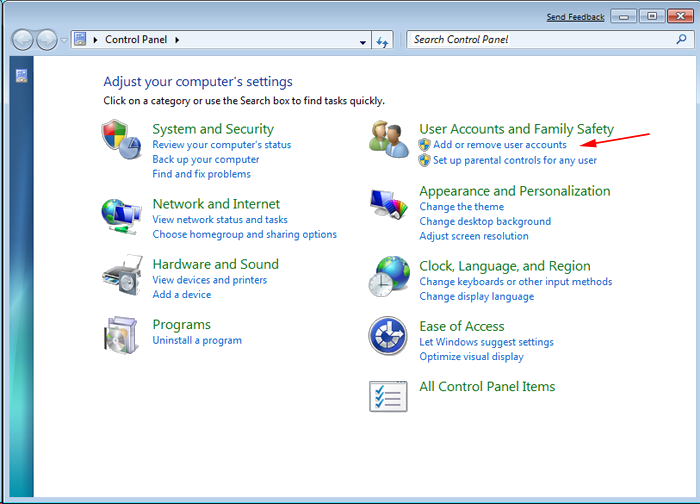
- Choose and remove all Jhash Ransomware related items from list.

B: How to Restore Jhash Ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing Jhash Ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
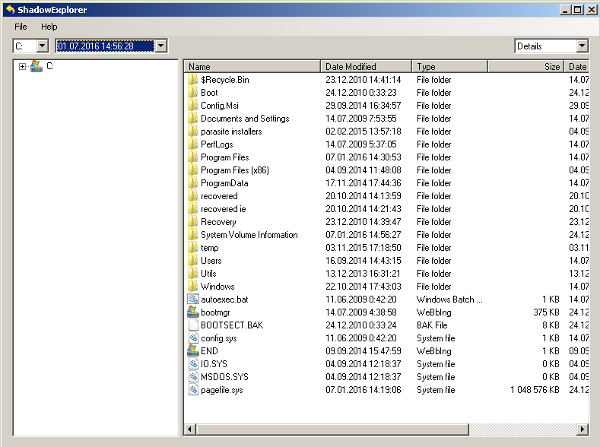
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing Jhash Ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
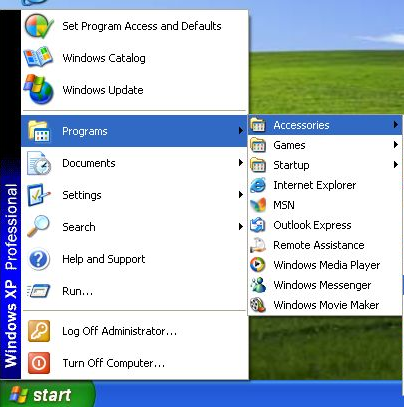
- Find System Tools and click System Restore
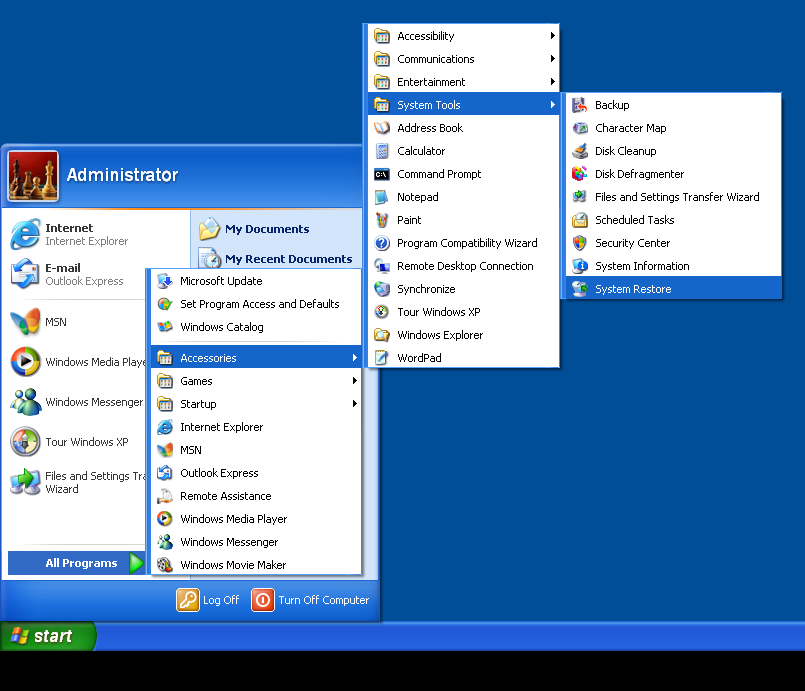
- Select Restore my computer to an earlier time and click Next.
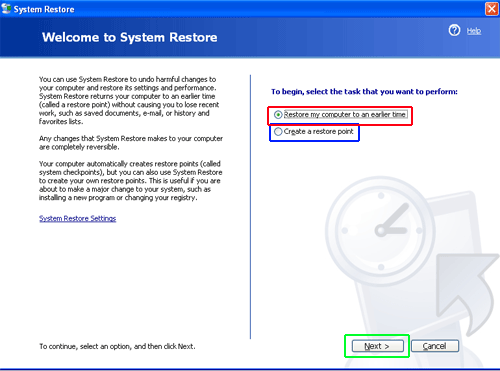
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by Jhash Ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.



