| 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 is a Keylogger | |
| Trojan Dropped by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 are Pushbot, VBInject.IH, PWSteal.Lineage.SJ.dll, Kucirc, Sykipot Trojan, Net-Worm.Koobface!sd6, Trojan-PWS.Tanspy, Trojan-Spy.VB.jo, Virus.VBInject.GQ, Trojan.Agent.AFTZ, Virus.Obfuscator.YU, Gamarue.D | |
| Related spyware Spyware.Webdir, Backdoor.Win32.Bifrose.fqm, Packer.Malware.NSAnti.J, Redpill, MicroBillSys, Bin, Win32.Enistery, FatPickle Toolbar, RemoteAccess.Netbus, Rootkit.Agent.grg, Ydky9kv.exe, Personal PC Spy, TSPY_AGENT.WWCJ | |
| Windows Error caused by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 are – Error 0x80070070 – 0x50011, 0xf0816 CBS_E_DPX_JOB_STATE_SAVED job state for DPX has been saved, 0x000000FE, 0x0000007B, 0x0000010F, 0x80248002 WU_E_DS_INVALID The current and expected states of the data store do not match., 0x8024401C WU_E_PT_HTTP_STATUS_REQUEST_TIMEOUT Same as HTTP status 408 – the server timed out waiting for the request., 0x80248019 WU_E_DS_NEEDWINDOWSSERVICE A request to remove the Windows Update service or to unregister it with Automatic Updates was declined because it is a built-in service and/or Automatic Updates cannot fall back to another service., 0x00000109 | |
| 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 infects these windows .dll files sccsccp.dll, hbaapi.dll, jgaw400.dll, hpzvuw72.dll, netprof.dll, Accessibility.dll, NlsLexicons0045.dll, tiptsf.dll, dhcpcsvc6.dll, networkexplorer.dll, WMVENCOD.dll, setupdll.dll, wiascr.dll, webvw.dll |
18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 may have entered your pc through these software. If you have not installed them , then get rid of them Joboshare VOB to iPad Converter , Tumult HyperEdit 1.6 , Coyote Chase , MacPermitWizard 1.1.0 , Brothers In Arms Hour of Heroes 1.0.3 , Morph Age Express 4.1.3 , iPubsoft PDF to HTML Converter , Dialog Studio 2.0.2 , PDFSign 2.0 , Vorlagen 2.4 , Barrage 1.0 , OpenLink Lite ODBC Driver for Oracle 8i & 9i 6.00.0220 , FilmTag 1.2.0 , Nemo’s Secret: Vulcania 1.0.1.10 , avscore 0.1 |
|

Delete 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 From Windows XP|Vista|7|8|10
Research Report On 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58
| Name | 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 |
| Type | Trojan |
| Risk Impact | High |
| Description | The main objective of 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 is to gain remote access for the attackers and gather confidential information from the computer. |
| Possible Symptoms | Performance degradation of system, other malware attacks, cyber theft, etc. |
| Detection / Removal Tool | Download 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 Scanner to confirm the attack of 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 virus. |
Important Things To Know About 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58
18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 is a piece of malicious software which is reported by team of malware researchers. Cyber security professionals have warned the web surfers that the malware can be used by the threat actors to hijack user’s accounts on popular social networking websites. In addition to that, it also has the ability to log keystrokes on compromised machines, download rogue applications from its remote server and open ports on the machine for invading other destructive viruses. The Trojan has been identified for setting up email relays onto the affected systems. Besides, 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 is a vicious kind of malware which allows the criminal hackers to download and run malicious application on victim’s machine.
Moreover, it can also infect the home or business networks as well. Technically speaking, the name of this Trojan is based on fact that the malware uses various obfuscation technique which allows the developers of 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 to hide their real IP addresses by using the computer of victimized users for sending out spam emails. The technique which is used to spread the malware all across the world is a malvertising campaign. Cyber crooks deliver numerous spam emails on regular basis and those emails carry a file and encrypted with a PowerShell code and harmful macros. In this way, when the targeted users open such junk emails on their machine, then the dangerous threats like 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 immediately infiltrates the machine and started doing various illicit tasks.
Distribution Tendency Of 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 Malware
The junk emails distributed by this threat contains an image file or a document which appears as a legitimate alert from Microsoft Office suite. It instructs the system users to enable content completely see the message which is not displayed on computer screen. Although, this is a simple tactic used by the creators of 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 and other dangerous viruses who seek to lure targeted PC users into running a malicious code by gaining admin privileges. The scripts are loaded by the Windows and decrypted in the system’s memory in a manner which does not save the malicious file onto the disk. The main objective of this malware is to gain remote access for the attackers and gather confidential information from the computer. Therefore, you should take immediate action for 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 removal.
Steps to Remove 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58
Step 1>> How to Boot Windows in Safe Mode to isolate 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58
Step 2>> How to View Hidden Files created by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58
for Windows XP
- Exit all Program and Go to Desktop
- Select My Computer icon and Double Click to Open it
- Click on the Tools Menu and now select and Click on Folder Options.
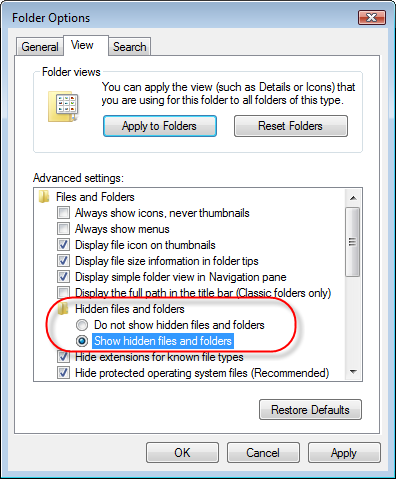
- Select on View Tab that appears in New Window.
- Check mark on the box next to Dispaly the Contents of System Folders
- Now Check the box in order to Show Hidden Files and Folders
- Now press on Apply and OK to close the Window.
- As soon as these steps are performed, you can view the files and folders that were created by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 and hidden till now.
for Windows Vista
- Minimize all Window and Go to Desktop
- Click on the Start Button which can be found in lower lef Corner having Windows Logo
- Click on the Control Panel on the Menu and Open it
- Control Panel can be opened in Classic View or Control Panel Home View.
- If you have Selected Classic View, follow this
- Double Click on the Folder icon to open it
- Now select the view tab
- Click on Option to Show Hidden Files or Folders
- If you have Selected Control Panel Home View, follow this
- Appearance and Personalization link is to be Clicked
- Select on Show Hidden Files or Folders
- Press Apply Option and then Click on OK.

This will Show all the Folders including those created by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58
Know how to view Hidden Folders on Windows 7, Win 8 and Windows 10
(Following the above steps are necessary to view all the files created by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 and that is known to exist on Compromised PC.)
- Open the Run Box by holding together the Start Key and R.

- Now Type and input appwiz.cpl and press on OK
- This will take you to the Control Panel, Now Search for Suspicious programs or any entries related to 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58. Unistall it once if you happen to find it. However be sure not to Uninstall any other program from the list.
- In the Search Field, Type msconfig and press on Enter, this will pop-up a Window

In the Startup Menu, Uncheck all the 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 related entries or which are Unknown as Manufacturer.
Step 3>> Open the Run Box by Pressing Start Key and R in Combination
- Copy + Paste the following Command as
- notepad %windir%/system32/Drivers/etc/hosts and press on OK
- This will Open a new file. If your system has been hacked by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58, certain IP’s will be displayed which can be found in the bottom of the screen.
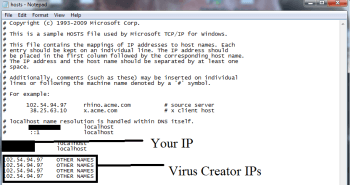
Look for the suspicious IP that is present in your Localhost
Step 4>> How to Terminate 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 Running Processes
- Go the Processes Tab by pressing on CTRL+SHIFT+ESC Keys Together.
- Look for the 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 Running Processes.
- Right Click on 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 and End the Process.

Step 5>> How to Remove 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 Related Registry Entries
- Open Registry by Typing Regedit in the Run box and Hit Enter Key
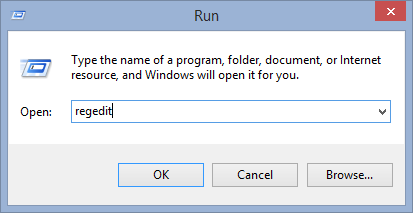
- This will open all the list of entries.
- Now Find and search the entries created by 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 and cautiously delete it.
- Alternatively, you can manually search for it in the list to delete 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58 Manually.
Unfortunately, if you are unable to remove 18HFyZfSZT8GXJJbUPTgPXZojoNEEjHE58, Scan your PC Now
Also submit question and let us know in case you are having some doubt. Our Experts will definitely respond with some positive suggestions for the same. Thanks!


