| CVE-2020-0674 is a Worm | |
| Trojan Dropped by CVE-2020-0674 are Autorun.ZG, Kexqoud, TROJ_PIDIEF.KFR, Trojan.Proxyser-R, Zlob.VideoAccess, Troj/Dorkbot-BL, Trojan.Tracur.B, I-Worm.Melting, Trojan.AgentBypass.B, Trojan.Win32.VB.alak, Frethog.AI, Trojan.Rbot-AWU, Spy.Bancos.C | |
| Related spyware Worm.Zhelatin.GG, NetSky, MySpaceIM Monitor Sniffer, ICQ Account Cracking, ShopAtHome.B, AceSpy, Antivirok.com, NetZip, SysKontroller, TSPY_DROISNAKE.A, SafeSurfing, NewsUpdexe, Adware.RelatedLinks, Faretoraci | |
| Windows Error caused by CVE-2020-0674 are – 0x80240003 WU_E_UNKNOWN_ID An ID cannot be found., 0x0000012C, 0x00000053, 0x0000009C, 0x000000BC, 0x8024200B WU_E_UH_INSTALLERFAILURE The installer failed to install (uninstall) one or more updates., 0x00000022, 0x8024801A WU_E_DS_INVALIDOPERATION A request was declined because the operation is not allowed., 0x00000040, 0x00000009 | |
| CVE-2020-0674 infects these windows .dll files vchnt5.dll, slextspk.dll, System.Data.Entity.Design.ni.dll, Microsoft.VisualC.dll, mll_hp.dll, wersvc.dll, mssrch.dll, photowiz.dll, netprofm.dll, dnsext.dll, d3dxof.dll, atmfd.dll |
CVE-2020-0674 may have entered your pc through these software. If you have not installed them , then get rid of them UK Yellow Pages 0.7 , ClipboardSharing 2.0.2 , IDImposer 9.0.7 , i$tock Contributor Application 1.1.6 , Dash Tray 1.0 , Growly Notes 2.0.5 , GlowPuzzle Freemium 1.9 , CashTrack 1.0.0.1 , Speed Profiler 1.8.1 , vCard ez-Football Coach 06A , MegaMensuration 1.3.1 , Pooch 1.8.3 , OS Halo Timer 1.5 , Living Weather HD 3.0.2 , AOL Communicator 1.0 , DesKalc 1.0b6 |
|

Remove CVE-2020-0674 Quickly From Windows
A Brief Idea About CVE-2020-0674
CVE-2020-0674 is a perilous trojan virus infection for the computer. It is created by the hackers. This misleading malware is silently inject into the computer and capable to do malicious activities inside the computer. It installed deeply inside the system. Once it get installed, it disable antivirus and firewall protection. This malware capable to makes the system more vulnerable. It steals important information of the users and make them victim. It brings more viruses by the backdoor system that creates more damages into the computer. In short it is a risky threat that hamper your security and privacy.
How CVE-2020-0674 Will Get Intrude Into Your System?
CVE-2020-0674 uses variety of methods to inject into the computer. It easily modify the Windows operating system without any permission of the user. Some of the general intrusive methods are – CVE-2020-0674 get downloaded into the system via bundled with free third party software or programs. The spam email or junk email attachments which provide the infection when user click on the attachments file to open it. The other penetrating methods are used as visiting the malicious websites like suspicious or unknown sites that you never visit before, porn websites, torrent and etc. Playing online games, downloading pirated or cracked software, network file sharing or media files can also invade CVE-2020-0674 into your system. Downloading the fake program or software updates can also deliver this virus inside the system. By clicking on the suspicious links or deceptive advertisements get redirect on the malicious site where more viruses get installed into the computer. By injecting the infections USB drives or the external media like CD, DVD, etc are also one of the most effective methods to deliver this trojan virus.
The Harmful Effects Of CVE-2020-0674
When CVE-2020-0674 get installed into your computer, it leads to the major modification. It mess up the system and destroy the whole PC. Some of the common effects that can be visualize are:
- CVE-2020-0674 silently injects into the computer without any user’s consent.
- It destroy the computer files, programs, software and etc.
- It disable the firewall and antivirus protection.
- CVE-2020-0674 brings other similar spyware, threats, and malware inside the system.
- Block the vital features such as registry editor, task manager, control panel and etc.
- Steal financial and personal data to send it to the hackers.
- Create the new registry keys to start itself automatically into the system.
- Develop the backdoor onto the computer and allow hackers to access remotely the computer.
Steps to Delete CVE-2020-0674
Step: 1 Restart your Windows PC in Safe Mode
Find the complete details on how to Reboot your PC in Safe Mode (if you are a novice, follow the above given instructions on how to boot up your PC in Safe mode irrespective of the Windows Version that is being used as Windows XP, 7, Win 8, 8.1 and Windows 10)
Step:2 Remove CVE-2020-0674 from Task Manager
Press CTRL+ALT+DEL simulataneously to open Task manager. Find CVE-2020-0674 Related processes or any other suspicious processes that are running on it. Now Select and delete CVE-2020-0674 virus from Task Manager at once.

Step:3 How to Delete CVE-2020-0674 Related Startup Items
Press Win + R together and Type “msconfig”.

Now press Enter Key or Select OK.
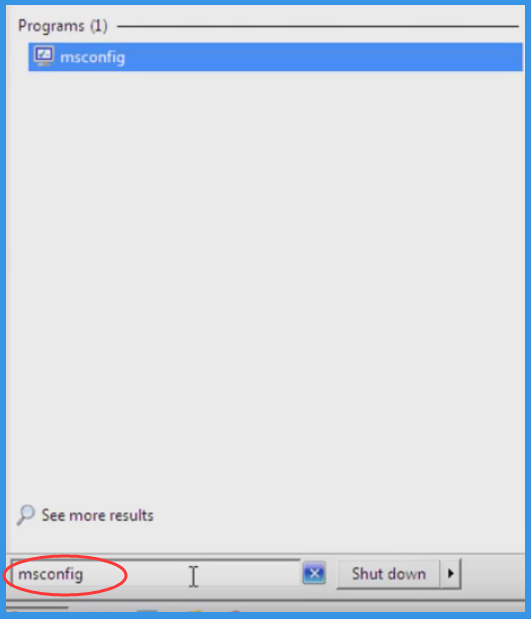
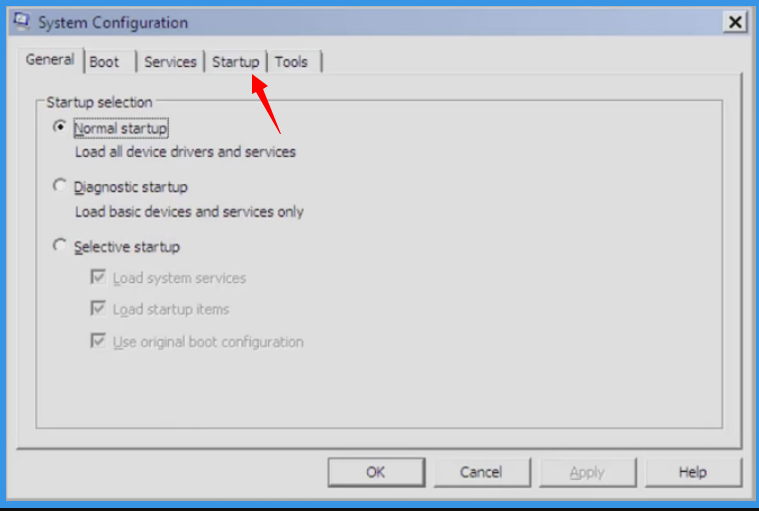
“Startup” option is to be selected on the Pop-up Window Tab
Now Search for CVE-2020-0674 Related applications on Startup Items
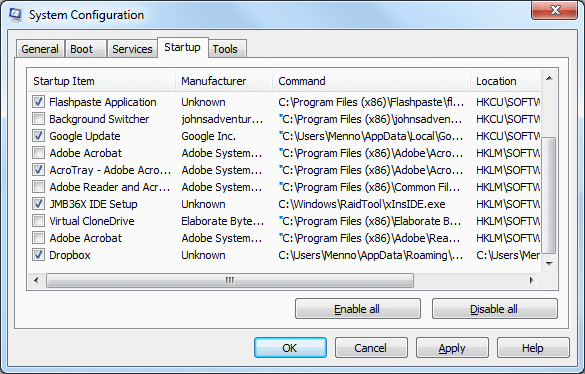
Now Uncheck all Unknown or Suspicious items from “System Configuration” related to CVE-2020-0674

Now Click and Select Restart to Start your Computer in Normal Mode
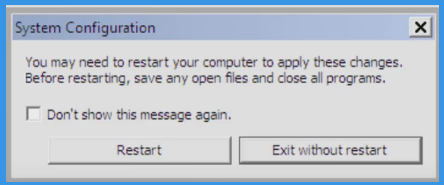
Step: 4 How to Delete CVE-2020-0674 from Windows Registry
- Press Win + R in combination to Open Run Box, Type regedit on the search box and press enter.
- This will Open the registry entries.
- Find CVE-2020-0674 related entries from the list and carefully delete it. However be careful and do not delete any other entries as this could severely damage the Windows Component.
Also, after completing the above steps, it is important to search for any folders and files that has been created by CVE-2020-0674 and if found must be deleted.
Step 5 How to View Hidden Files and Folders Created by CVE-2020-0674
- Click on the Start Menu
- Go to Control Panel, and Search for folder Options
- Click on view hidden files and folders Options, For your convenience, we have included complete process on how to unhide files on all Windows Version. This will delete all the files and folders associated with CVE-2020-0674 that was existing on your compromised system.
Still, if you are unable to get rid of CVE-2020-0674 using manual steps, you need to scan your PC to detect CVE-2020-0674.
Don’t forget to submit your questions or any other queries if you have and get complete solution from our Expert’s Panel. Good Luck!


