| CVE-2018-8453 is a Backdoor | |
| Trojan Dropped by CVE-2018-8453 are Trojan.Reveton.N, Win32.Svich, Infostealer.Opsiness, DelfInject.gen!BA, Usblog, Intruder, Trojan-Downloader.Agent-OL, I-Worm.Lacrow, Rootkitdrv.gen!A, Vundo.FAY | |
| Related spyware Backdoor.Win32.Bifrose.fqm, Modem Spy, Trojan.Win32.CP4000, WebMail Spy, Email-Worm.Zhelatin.is, Qakbot, Otherhomepage.com, Stealth Website Logger, Backdoor.Turkojan!ct, RegiFast, Backdoor.Prorat.h, VirusSchlacht | |
| Windows Error caused by CVE-2018-8453 are – 0x000000B9, Error 0xC1900202 – 0x20008, 0x8024400A WU_E_PT_SOAPCLIENT_PARSE Same as SOAPCLIENT_PARSE_ERROR – SOAP client failed to parse the response from the server. , 0x0000006E, 0x000000A5, 0x8024001D WU_E_INVALID_UPDATE An update contains invalid metadata., 0x0000004C, 0x00000092, 0x80248007 WU_E_DS_NODATA The information requested is not in the data store. | |
| CVE-2018-8453 infects these windows .dll files Microsoft.ApplicationId.RuleWizard.dll, isign32.dll, RW330Ext.dll, lsasrv.dll, mscorjit.dll, NlsData0414.dll, mqrtdep.dll, d3d10_1.dll, Microsoft.Build.Engine.dll, dsauth.dll, RDPENCDD.dll, eapphost.dll, cscobj.dll, System.AddIn.dll |
CVE-2018-8453 may have entered your pc through these software. If you have not installed them , then get rid of them LetterMess 1.0 , AmpliTube 1.0 , Trenches: Generals 1.0 , Custom Login Message 1.0 , SilverFast (Canon) 8.0.1r37 , CommandoMaker 1.0 , iBridgeCards 31.1 , Defaulter 1.1.5 , gTuner 1.0.9 , WiFi Scanner , A Better Finder Rename , Kangas Sound Editor , BinJugglerCM X 1.3.1 , 4Easysoft TS to WMA Converter , LGV Theory Test Lite 5.0 , Dream Aquarium 1.0 , iCustomize 2.1 , Coolmuster Data Recovery for iTunes , Tattoo X 1.2 |
|

Now Remove CVE-2018-8453 Quickly From Your Computer
An Introduction To CVE-2018-8453
CVE-2018-8453 is a nasty computer infection which causes more than enough vulnerability to your system. It has several unwanted activities which ruin your PC. It is treated by the hackers to solve their worst motives. This is capable to provide you data loss. Mainly the trojan infection causes the major problem inside your machine. It consume lots of CPU power and degrades working speed. This article provides you a deep knowledge about the CVE-2018-8453 and also help you a lot to get rid of this virus.
How Will CVE-2018-8453 Penetrate Into Your System?
This is a very important question. Yes. You must have the need to understand why your system is getting vulnerability. CVE-2018-8453 penetrate silently without your information. It invades via spam email attachments, peer to peer network file transfer, freeware downloads, clicking on suspicious link, visiting low quality websites etc.
What Are The Common Symptoms Of CVE-2018-8453
- CVE-2018-8453 slowdown your computer.
- It creates lots of vulnerabilities and make PC sluggish.
- The computer may get crash.
- Annoying advertisements will start to display.
- Pop-up message will also display.
- The fake internet traffic will increase.
- The browser homepage modifies without any input.
- Unwanted messages will start to display.
- The antivirus and firewall protection will get display.
- You email starts to send spam mail.
- Meaningless icons will display on your desktop.
- Unfamiliar error messages will show.
- You will be unable to access control panel.
- There is no perfection in working of PC but you will assume that it is working properly.
Why Is CVE-2018-8453 Harmful?
CVE-2018-8453 has different kinds of activities which provide a troublesome period for you. You PC will get dump in this case. It invites hackers to monitor your every work online and also on system. When you saved your important information, it is hacked by them and you will lose your data. They generate lots of profit by this and you may face a big trouble. It also create the background entry for the other viruses such as threats, spyware, ransomware and so on. This is also one of the major way to create vulnerabilities into your computer. So, it is much better that you must remove CVE-2018-8453 quickly from your computer.
Preventive Actions From CVE-2018-8453
CVE-2018-8453 can be remove further by installing the antivirus and you should regularly update it for complete removal process. Always turn on your firewall protection. Use strong password every where.
How to Remove CVE-2018-8453 from Compromised PC (Manual Steps)
(This guide is intended to help users in following Step by Step instructions in making Windows Safe)
The first step which need to be followed is to Restart Windows PC in Safe Mode
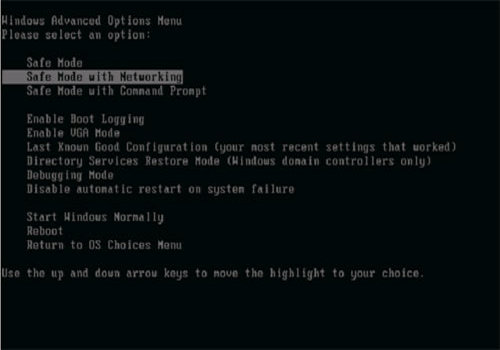
Reboot in Safe Mode (For Windows XP | Vista | Win7)
- Restart Computer
- Tap on F8 continuously when the PC starts booting and select the option to enter Safe Mode with Networking.
For Windows 8/8.1
- Press on the Start Button and then Choose Control Panel from the menu option
- Users need to opt for System and Security, to select Administrative Tools and then System Configuration.

3. Next, Click on the Safe Boot option and then choose OK, this will open a pop-up window, next Select Restart Option.
For Windows 10
- Start Menu is to be selected to Open it
- Press the power button icon which is present in the right corner, this will display power options menu.
- Keeping the SHIFT Key pressed on the keyboard, select the restart option. This will reboot Win 10
- Now you need to select the Troubleshoot icon, followed by advanced option in the startup Settings. Click on Restart. This will give the option to reboot, now select Enter Safe Mode with Networking.
Step 2. Uninstall CVE-2018-8453 from Task Manager on Windows
How to End the Running Process related to CVE-2018-8453 using Task Manager
- Firstly, Open Task Manager by Pressing Ctrl+Shift+Esc in Combination
- Next, Click on processes to Find CVE-2018-8453
- Now Click and select End Process to terminate CVE-2018-8453.

Step3: How to Uninstall CVE-2018-8453 from Control Panel on Windows
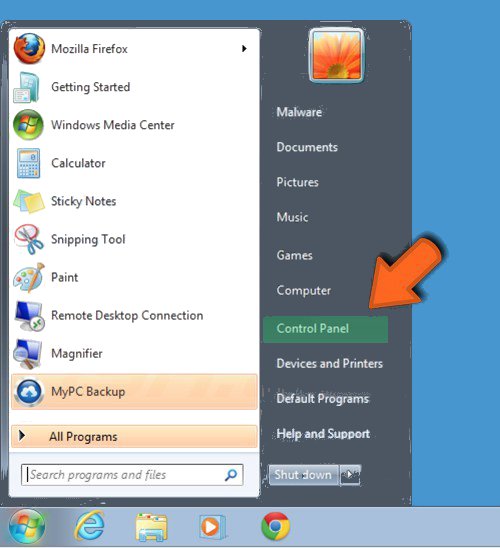
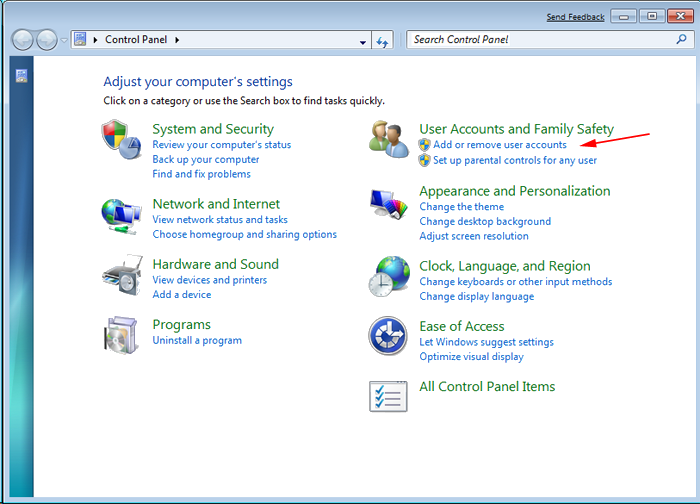
for Win XP| Vista and Win 7 Users
- Click and Select on Start Menu
- Now Control Panel is to be selected from the list
- Next Click on Uninstall Program
- Users need to Choose suspicious program related to CVE-2018-8453 and right clicking on it.
- Finally, Select Uninstall option.

For Win 8
- Click and Select “Charms bar”
- Now Select Settings Option
- Next Click on Control Panel
- Select on Uninstall a Program Option and right click on program associated to CVE-2018-8453 and finally uninstall it.

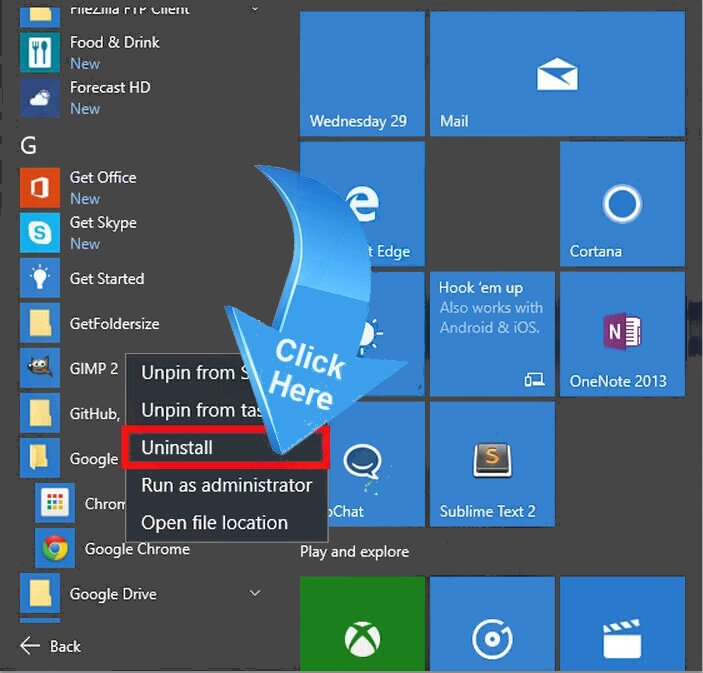
For Windows 10
- The first Step is to Click and Select on Start Menu
- Now Click on All Apps
- Choose CVE-2018-8453 and other suspicious program from the complete list
- Now right Click on to select CVE-2018-8453 and finally Uninstall it from Windows 10

Step: 4 How to Delete CVE-2018-8453 Created Files from Registry
- Open Registry by Typing Regedit in the Windows Search Field and then press on Enter.
- This will open the registry entries. Now users need to press CTRL + F together and type CVE-2018-8453 to find the entries.
- Once located, delete all CVE-2018-8453 named entries. If you are unable to find it, you need to look up for it on the directories manually. Be careful and delete only CVE-2018-8453 entries, else it can damage your Windows Computer severely.
HKEY_CURRENT_USER—-Software—–Random Directory.
HKEY_CURRENT_USER—-Software—Microsoft—-Windows—CurrentVersion—Run– Random
HKEY_CURRENT_USER—-Software—Microsoft—Internet Explorer—-Main—- Random
Still having any problem in getting rid of CVE-2018-8453, or have any doubt regarding this, feel free to ask our experts.