CryptoJacky Ransomware – What it has to offer?
Yet another file encoder virus, CryptoJacky Ransomware is discovered early in March 2017. It is specially crafted to target Spanish-speaking users and extort a huge ransom fee from them while keeping important files decryption key as hostage. May be in future, its improved variant may target English-speaking computer users too. Speaking of data encryption, CryptoJacky Ransomware has been released with an AES encryption engine that generates secured private key and public key before starting file encryption process. Following successful encryption, CryptoJacky virus stores private key only on the C&C server while public key is dropped onto victim’s desktop along with ransom note file. You should note that private key is used for data decryption whereas public key is used to identify victim’s computer and works as a unique ID.

During initial analysis security investigators found cryptoJacky-setup.exe file on the affected computer. This file is actually executable of CryptoJacky Ransomware. Additionally, aescrypt.exe process was also found, which represents encryption engine of the ransomware. Both process consume a whole lot of space onto system memory and make computer vulnerable as well. After encoding your files, the ransomware displays ransom note and demand 250 EUR as ransom in order to provide data decryption key (software/tool).
You will also be suggested to contact via [email protected] to get further assistance. However, security experts oppose paying off ransom because it is extremely risky. You might want to know the reason behind it. Right? First, the ransomware attackers only except payment via Bitcoin base wallet which is hosted through TOR network. TOR network community is always known for supporting cyber criminals around the globe. Moreover, you can not trust attackers. They may have also installed keyloggers to record your keystrokes that includes your online banking passwords, payment card numbers, registered email/mobile number, postal address without your proper knowledge. Later on, the information is used to hack into your various accounts secretly.
Is it possible to prevent CryptoJacky Ransomware attacks?
Of course, a curious computer user can avoid installation of CryptoJacky Ransomware easily. Please note that ransomware always arrive onto Windows-machine via spam emails attachments. Such emails may look so legitimate sent via infamous companies or suspicious source. When you double click attached files, your computer gets penetrated with CryptoJacky Ransomware. Even, Torrents sites and trojanized software are also involved in the distribution of this ransomware program. Though, you must not download/execute any suspicious file onto your computer. In some cases, this cryptomalware arrives onto computer by updating existing programs from unverified source. While surfing Internet may see fake software updates and security alerts, if you get scared and install updates without verifying the source, your computer gets compromised.
Hence, if you really want to safeguard your computer, you make use of efficient security software to scan your system on the regular basis. Next, before start data recovery process, you should remove from your computer. Kindly, follow the given instructions carefully:
A Tutorial Video For CryptoJacky Ransomware Removal Guide
Free Scan your Windows PC to detect CryptoJacky Ransomware
How To Remove CryptoJacky Ransomware Virus Manually
Step 1 : Restart your computer in safe with networking
- Restart your computer and keep pressing F8 key continuously.

- You will find the Advance Boot Option on your computer screen.

- Select Safe Mode With Networking Option by using arrow keys.
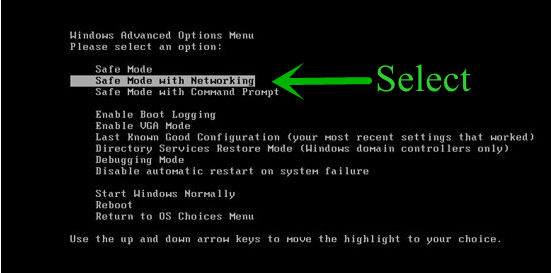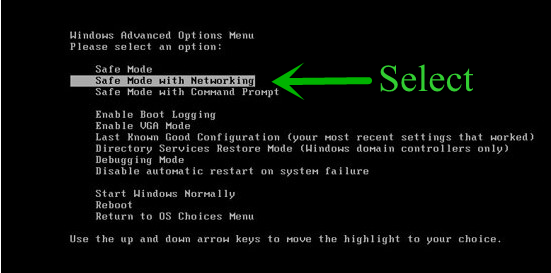
- Login your computer with Administrator account.
Step 2 : Step all CryptoJacky Ransomware related process
- Press the Windows+R buttons together to open Run Box.

- Type “taskmgr” and Click OK or Hit Enter button.

- Now go to the Process tab and find out CryptoJacky Ransomware related process.

- Click on End Process button to stop that running process.
Step 3 : Restore Your Windows PC To Factory Settings
System Restore Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
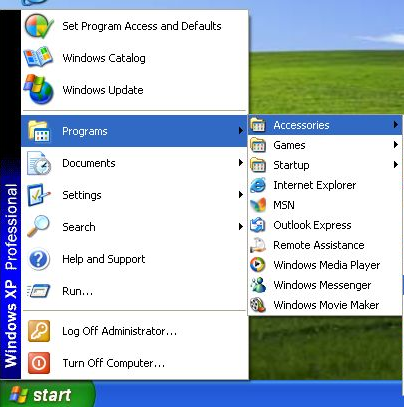
- Find System Tools and click System Restore.
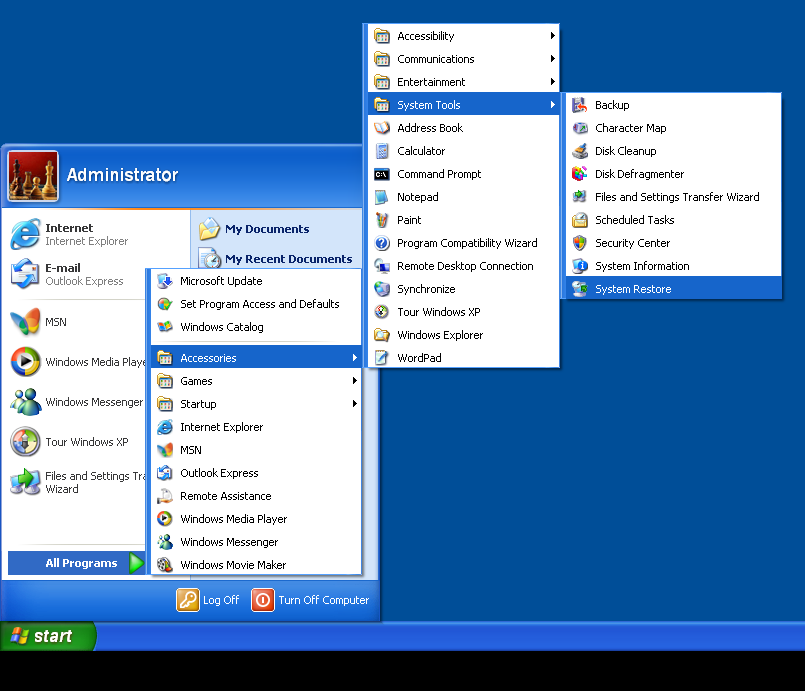
- Select Restore my computer to an earlier time and click Next.
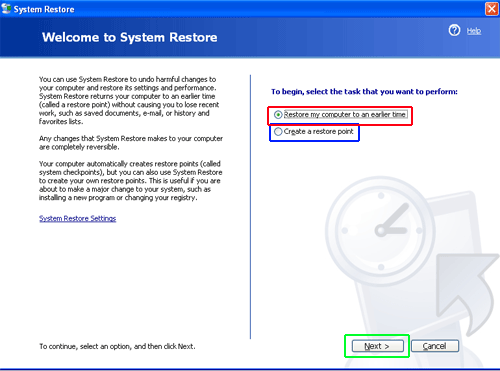
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results.
- From the System Restore window, click the Next button.
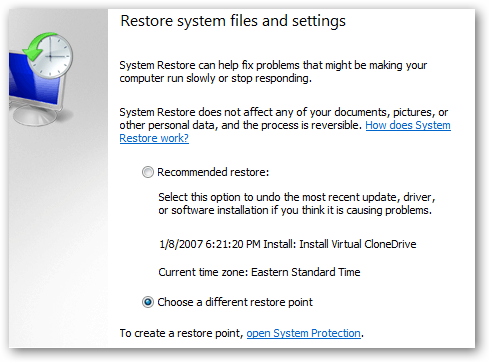
- Now select a restore points when your PC was not infected.
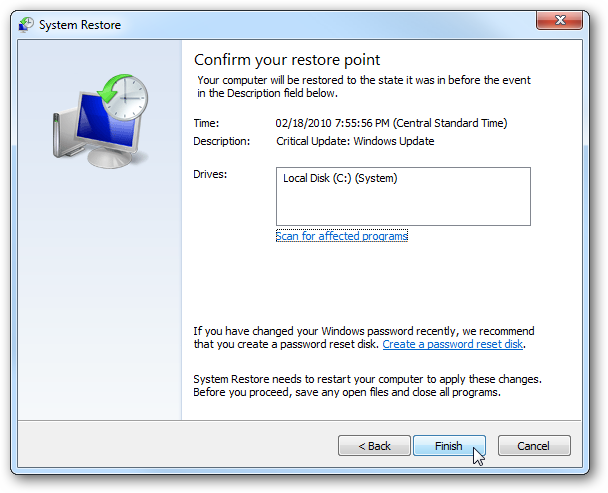
- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel.

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option.

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.
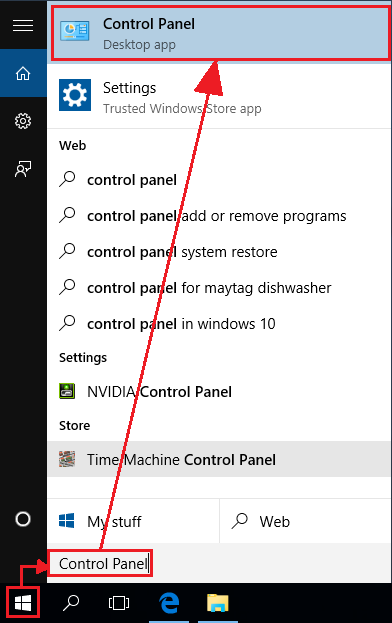
- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Hope these manual steps help you successfully remove the CryptoJacky Ransomware infection from your computer. If you have performed all the above manual steps and still can’t access your files or cannot remove this nasty ransomware infection from your computer then you should choose a powerful malware removal tool. You can easily remove this harmful virus from your computer by using third party tool. It is the best and the most easy way to get rid of this infection.
If you have any further question regarding this threat or its removal then you can directly ask your question from our experts. A panel of highly experienced and qualified tech support experts are waiting to help you.




