Get More Knowledge on AAC Ransomware
AAC Ransomware is one of the most hazardous file-encoder virus which is capable of encrypting the files stored on affected machines and appends their name with '.aac' file extension. According to the latest investigation report, this ransomware is reported as a mid-tier crypto-virus which is distributed by the criminal hackers with the help of malicious spam email campaigns among the Windows operating system users. Therefore, the computer users are are highly advised to refrain opening the files attached on spam emails or clicking on the links embedded onto it, because the criminal hackers behind the creation of AAC Ransomware launched a massive campaign of spam emails in the last week of August, 2017.
AAC Ransomware : Working Algorithms
In case, if AAC Ransomware successfully invades your computer system, it will run numerous processes with random names and then make a report based on your PC information like device name, IP address, memory banks, keyboard layout and active user account name. After that, these information will be delivered to the “Command and Control” server operated by the criminal hackers with the help of POST request. It is especially programmed by the threat actors in order to encode the standard file types associated with famous programs like Windows Media Player, MySQL, Microsoft Office and Amazon Kindle by using strong AES cryptographic algorithm.
Besides, AAC Ransomware may delete the Shadow Volume copies and file structure of the data encoded by it to make the recovery procedure using Windows native restoration technique quite impossible. The ransom note displayed by this malware can be found easily onto the system's desktop with the name of “Learn how to recover your files.txt” and instructs victimized users to contact the developers via “[email protected]” email address. However, refrain contacting the cyber criminals, instead eliminate AAC Ransomware as quickly as possible.
How To Protect Yourself From AAC Ransomware Attack?
One of the easiest trick to avoid infecting your machine with this ransomware virus is to immediately disable the macro functionality into your Word processor. It is strongly recommended by the security researchers that you run Macros from familiar or trusted sources and never try to ignore UAC prompts whenever they appear as you open which seems to be a .txt file. However, if it manages to invade the security system of your machine, you should take an immediate action for the complete removal of AAC Ransomware and try to recovery your computer files using backup copies.
Free Scan your Windows PC to detect AAC Ransomware
Free Scan your Windows PC to detect AAC Ransomware
A: How To Remove AAC Ransomware From Your PC
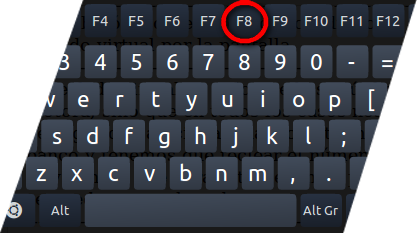
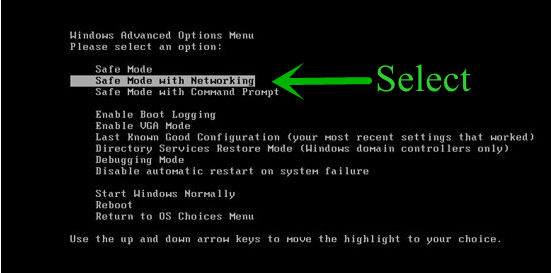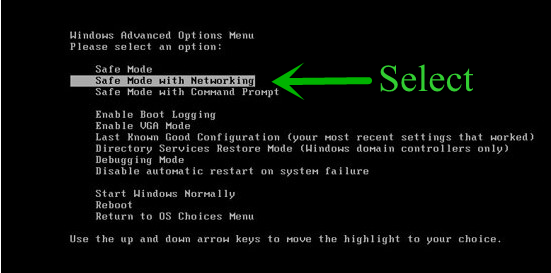
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.
- From the boot menu, select Safe Mode with Networking using the arrow keys.
Step: 2 How to Kill AAC Ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the AAC Ransomware related Process.
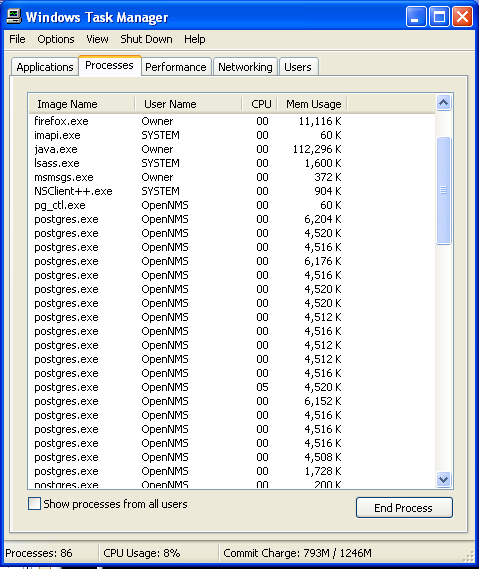
- Now click on on End Process button to close that task.
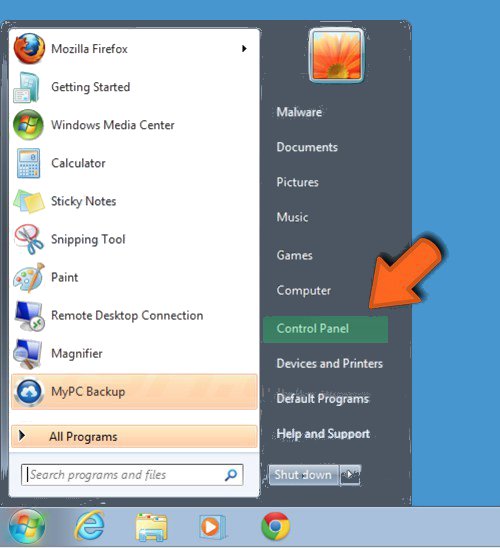
Step: 3 Uninstall AAC Ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
- Select Uninstall a Program option from Program category.
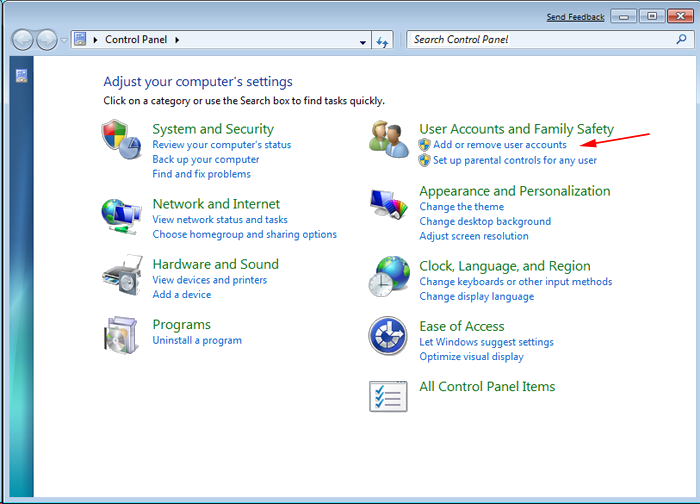
- Choose and remove all AAC Ransomware related items from list.

B: How to Restore AAC Ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing AAC Ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
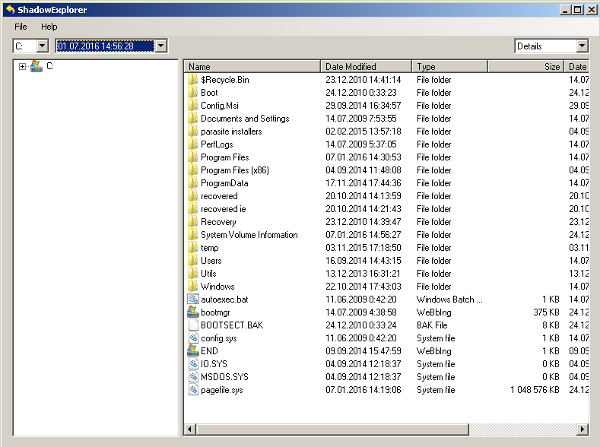
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing AAC Ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
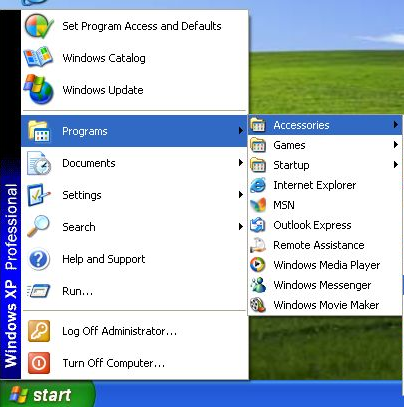
- Find System Tools and click System Restore
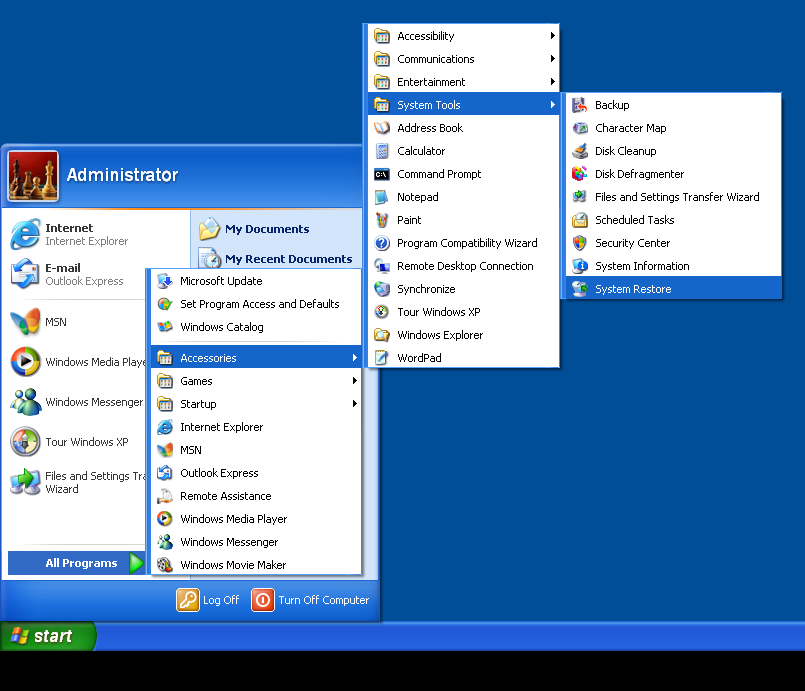
- Select Restore my computer to an earlier time and click Next.
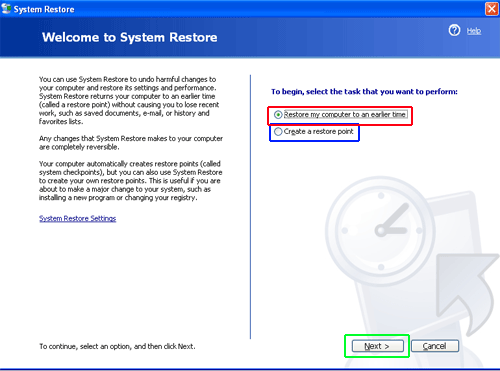
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by AAC Ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.



