
Why should you beware of ‘[email protected]’ Ransomware?
Apparently, ‘[email protected]’ Ransomware is a cryptomalware, derived from the infamous ransomware known as Bandarchor which had a great impact over the Internet few years back. After encrypting victim’s files using AES cipher – a military grade encryption cipher, it drops ‘HOW TO DECRYPT.txt’ on the desktop and forces victims to send email with the subject line – “1 am willing to pay for the decode files” on [email protected] containing an encrypted file. Unlike other ransomware, it provides telegram @Decryptservice and alternative email [email protected] to encourage contacting the malicious developers. Ransom amount is hidden, it depends developers that how much ransom they want you to pay off. However, security experts advise against paying ransom to them, cause if your do so, they will be high possibility that your online banking system credentials will be exposed.
Therefore, once such credentials went in the hackers hands, they will hack into bank accounts and one day you will notice that your bank balance is zero, your whole life’s savings are gone. If you see files like ‘SUN.png.id-[8 random characters][email protected]’ on your system, means your system has been compromised with the ransomwarrer. Before it gets to late, it is essential to gather necessary information about ‘[email protected]’ Ransomware and get rid of it immediately.
Highlights of ‘[email protected]’ Ransomware
- Malicious developers mostly send spam emails to PC users loaded with malicious files having double extensions with phishing text message that may convince you into clicking on the malicious attachment. The attached file is especially designed to install ‘[email protected]’ Ransomware on your system without any consent.
- ‘[email protected]’ Ransomware can encrypt files having one of these extensions : .r3d, .rwl, .rx2, .p12, .sbs, .sldasm, .wps, .sldprt, .odc, .odb, .old, .nbd, .nx1, .nrw, .orf, .ppt, .mov, .mpeg, .csv, .mdb, .cer, .arj, .ods, .mkv, .avi, .odt, .pdf, .docx, .gzip, .m2v, .cpt, .raw, .cdr, .cdx, .1cd, .3gp, .7z, .rar, .db3, .zip, .xlsx, .xls, .rtf, .doc, .jpeg, .jpg, .psd, .zip, .ert, .bak, .xml, .cf, .mdf, .fil, .spr, .accdb, .abf, .a3d, .asm, .fbx, .fbw, .fbk, .fdb, .fbf, .max, .m3d, .dbf, .ldf, .keystore, .iv2i, .gbk, .gho, .sn1, .sna, .spf, .sr2, .srf, .srw, .tis, .tbl, .x3f, .ods, .pef, .pptm, .txt, .pst, .ptx, .pz3, .mp3, .odp, .qic, .wps.
Ransom Note of ‘[email protected]’ Ransomware features following texts:
‘Attention!
Your files are encrypted with AES 256 algorithm!
Decoding is not possible without our decoder and universal key! In order to start the process of decoding the files, you need to contact us on the below contacts, with the subject: “1 am willing to pay for the decode my files” , attaching an example of an encrypted file
– Primary email: [email protected]
_ Secondary email: [email protected]
– Telegram: @Decryptservice
we encourage you to contact us for all three contacts!
– Very important: we recommend to write email us with Gmail or Yahoo address, otherwise your email may not reach us ,check the spam folder, probably our response email is in it!
Do not try to decrypt files by third-party decipherers, otherwise you will spoil files!’
In order to avoid such ransomware infection in future, security experts advise victims to keep a reliable antivirus software installed and updated on the their system and home-computers as well. It will protect systems against latest and old threats at real-time.
As of now, before proceeding file restoring technique, we suggest you to remove ‘[email protected]’ Ransomware from your system immediately. Follow the instruction.
Free Scan your Windows PC to detect ‘[email protected]’ Ransomware
Free Scan your Windows PC to detect ‘[email protected]’ Ransomware
A: How To Remove ‘[email protected]’ Ransomware From Your PC
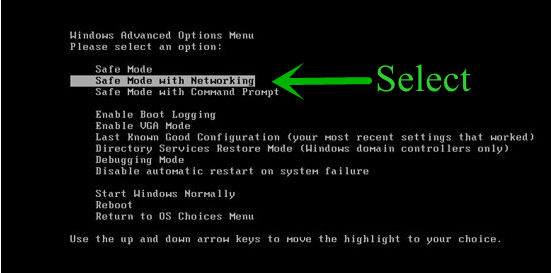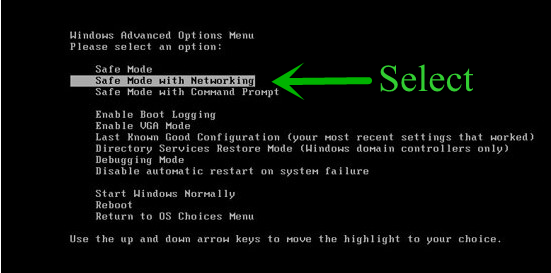
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.
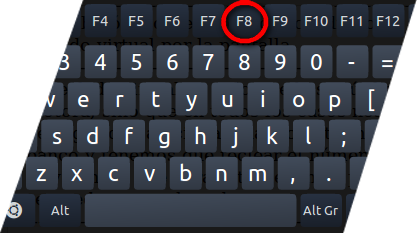
- From the boot menu, select Safe Mode with Networking using the arrow keys.
Step: 2 How to Kill ‘[email protected]’ Ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the ‘[email protected]’ Ransomware related Process.
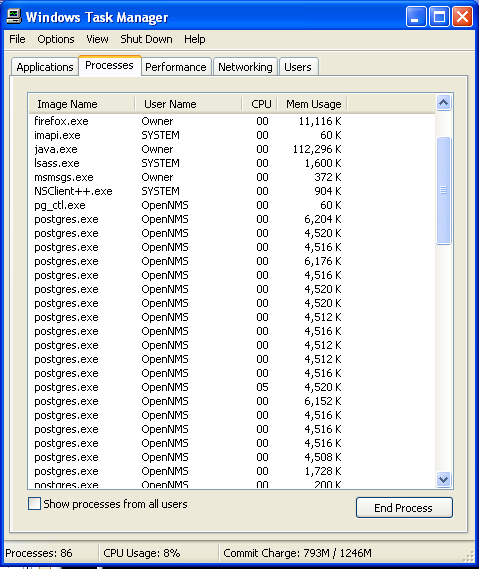
- Now click on on End Process button to close that task.
Step: 3 Uninstall ‘[email protected]’ Ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
- Select Uninstall a Program option from Program category.
- Choose and remove all ‘[email protected]’ Ransomware related items from list.

B: How to Restore ‘[email protected]’ Ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing ‘[email protected]’ Ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
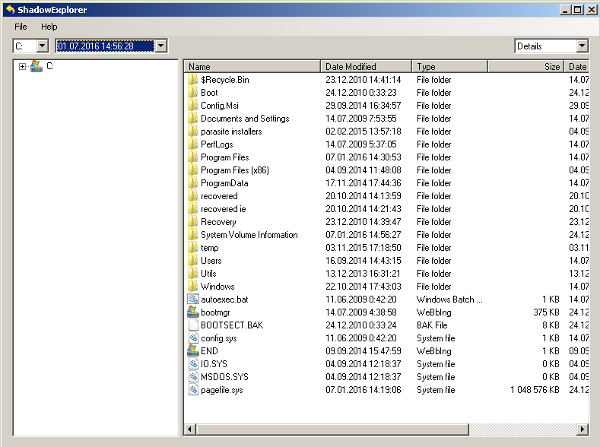
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing ‘[email protected]’ Ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
- Find System Tools and click System Restore
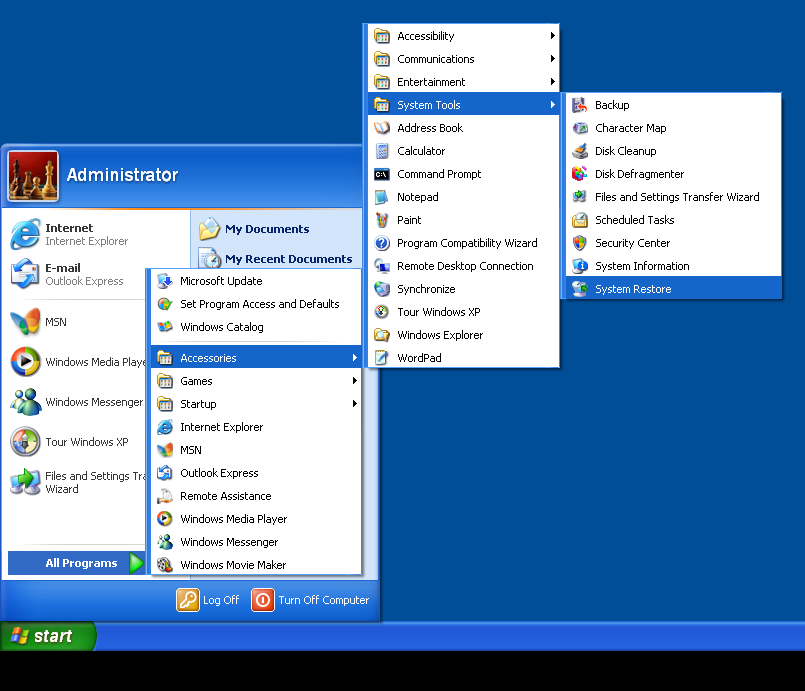
- Select Restore my computer to an earlier time and click Next.
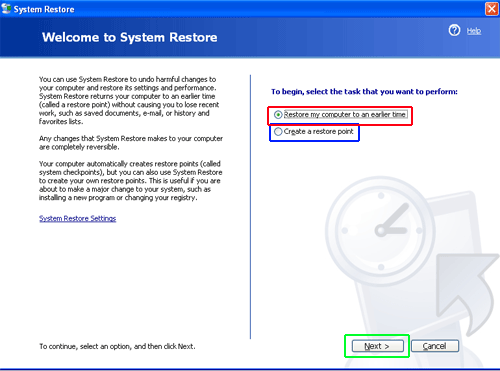
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by ‘[email protected]’ Ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.



