| Warning, many anti-virus scanner have detected Recovery Ransomware as threat to your computer | ||
| Recovery Ransomware is flagged by these Anti Virus Scanner | ||
| Anti Virus Software | Version | Detection |
| WhiteArmor | 2018.4.9251 | Non-specific |
| Cylance | 6.2.623225 | Trj.Win64.Recovery Ransomware.AB |
| AegisLab | 8.359827 | Variant of Win32/Trojan.Recovery Ransomware.C |
| ZDB Zeus | 8.0.233 | Backdoor.Aimbot, SchutzTool |
| Suggestion: Uninstall Recovery Ransomware Completely – Free Download | ||
Recovery Ransomware may have entered your pc through these software. If you have not installed them , then get rid of them Tunesify Lite 1.2.3 , App Switch 1.0.0 , The Hive X 1.0 , Flexify 2 2.7.7 , My Taptu 1.0 , Maze 2.4 , ClickLock! (PPC) 1.1 , iPGStats 1.0 , Rastafied 1.2.1 , Glance , iDemocracy 3.0 , Outlinely 1.0.4 , Math Practice 3.4.0 , Sword Forger Aggregator 2.1.0 , Candy Catch – Halloween 1.1.7 , BchunkerFE 0.4.1 , IOXperts USB WebCam Driver |
|

Recovery Ransomware : New Ransomware From its Family
These days, Recovery Ransomware is one of the most harmful and notorious ransomware infection ranks top most in System infections. As per the depth analysis by researchers, they revealed that it is the latest variant of its Ransomware family that is primary aimed to target domestic users but it does not mean that it cannot affect other users. The developers of this ransomware has been designed it in such a way that it can compromise almost all System executing on Windows based Operating System including Windows Server, Vista, XP, ME, NT, 7, 8/8.1 and the most recent version Windows 10.
Transmission Preferences of Recovery Ransomware
The developers of Recovery Ransomware uses several tricky channels to compromise machine but mainly it is delivers to Systems via compromised Remote Desktop connections and the spam emails that suggested users that they should read the notice from government or legitimate companies. Besides this, it can also enters inside the System when System users loaded software setup files on their PCs, download any freeware packages from untrusted sources, use any infected devices, upgrade OS via third-party or redirected link and many more. The distribution channels of this ransomware always varies but mainly distributed via Internet. Therefore, users should be cautious while doing any online work.
Behavior of Recovery Ransomware
- Proliferates inside the PC silently.
- Perform deep scan of targeted PC.
- Recovery Ransomware locks users stored files by adding file extension.
- Asks victim to pay ransom demanded fee.
- Slows down overall System working speed.
- Throws several fake alerts or notifications.
- Recovery Ransomware modifies entire System settings completely.
- Disables firewall settings and security measures etc.
Free Scan your Windows PC to detect Recovery Ransomware
A: How To Remove Recovery Ransomware From Your PC
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.
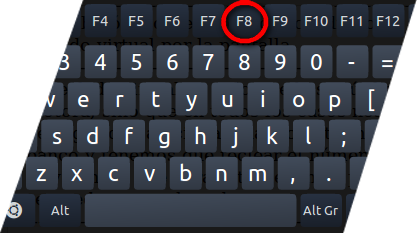
- From the boot menu, select Safe Mode with Networking using the arrow keys.
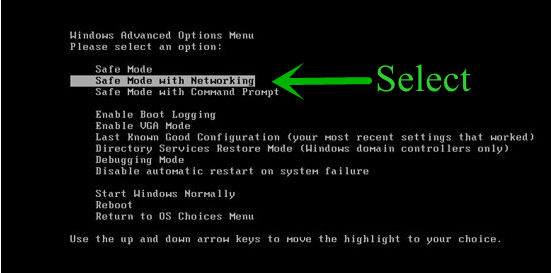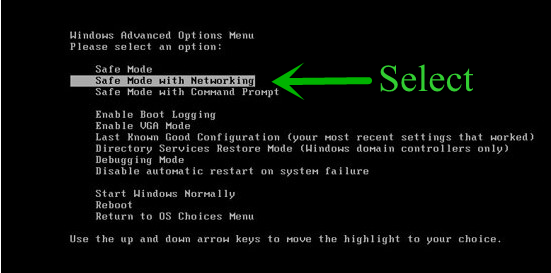
Step: 2 How to Kill Recovery Ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the Recovery Ransomware related Process.
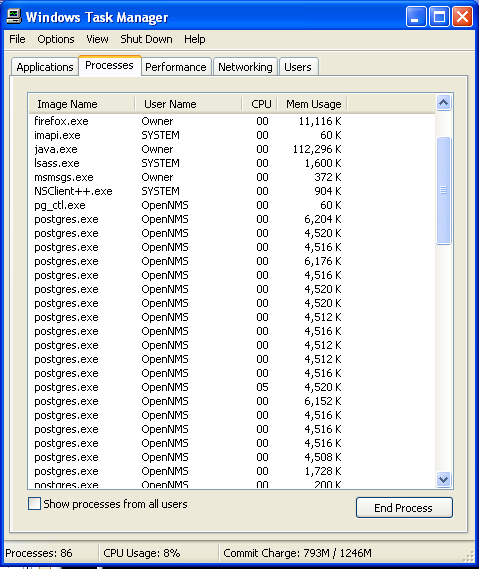
- Now click on on End Process button to close that task.
Step: 3 Uninstall Recovery Ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
- Select Uninstall a Program option from Program category.
- Choose and remove all Recovery Ransomware related items from list.

B: How to Restore Recovery Ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing Recovery Ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
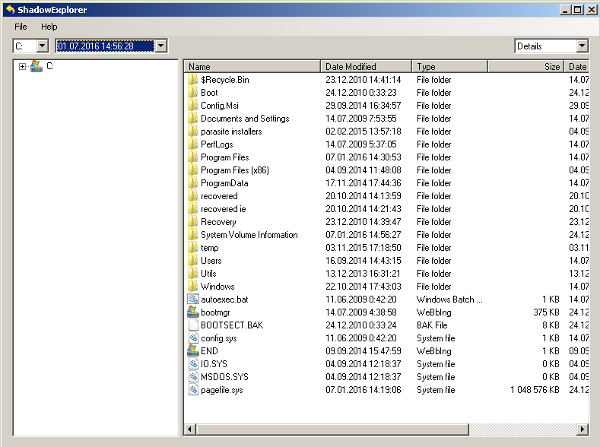
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing Recovery Ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
- Find System Tools and click System Restore
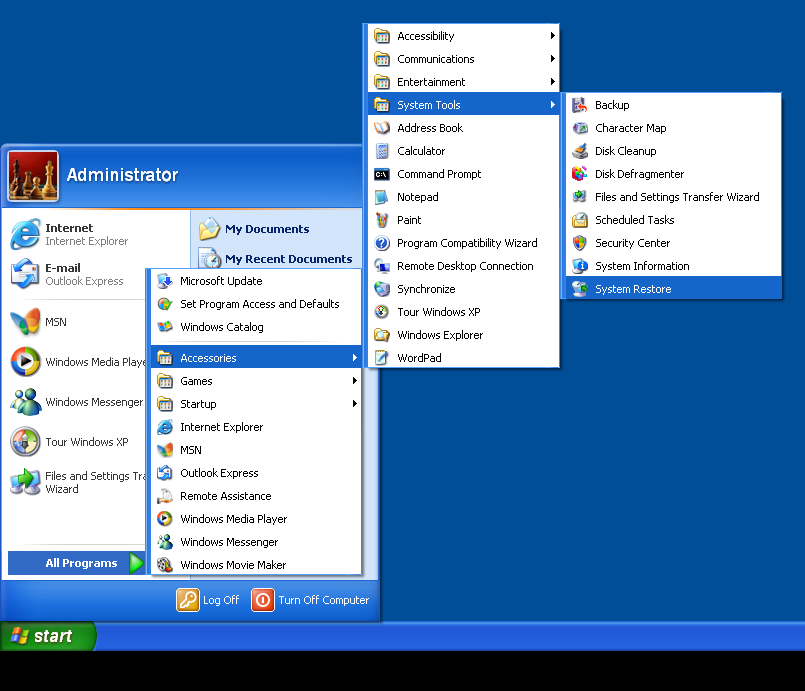
- Select Restore my computer to an earlier time and click Next.
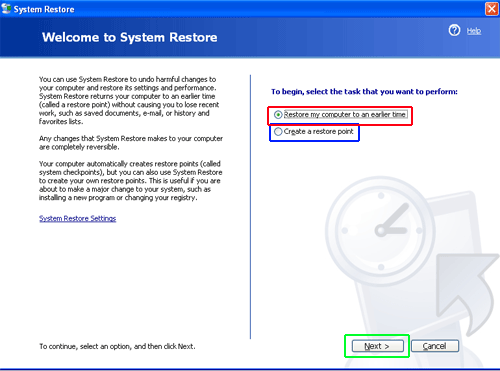
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by Recovery Ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.

