| Warning, many anti-virus scanner have detected [email protected] virus as threat to your computer | ||
| [email protected] virus is flagged by these Anti Virus Scanner | ||
| Anti Virus Software | Version | Detection |
| VBA32 | 2018.4.1527 | General |
| F-Prot | 7.1.801314 | [email protected] virus.AB |
| AVG | 4.241821 | Variant of Win32/[email protected] virus.B |
| Trustwave | 8.3.317 | PCSecureSystem, Spyware.GuardMon |
| Suggestion: Uninstall [email protected] virus Completely – Free Download | ||
[email protected] virus may have entered your pc through these software. If you have not installed them , then get rid of them Analytic Rarefaction 2.0 , Calculator 3.0 , EtherFast Router Driver 1.39.2 , TabMate 1.7.5 , Mail Badger 0.4 , Lingr 4.10 , CameraSafe 1.0 , iRefurb 1.0 , MpcPgmMaker 1.2.2 , Village Idiot 1.9 , OpenPlay SDK 2.2r2 |
|
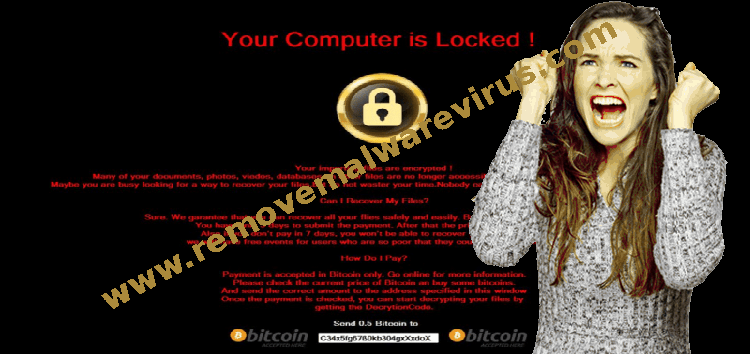
Detailed Report On [email protected] virus
[email protected] virus is a file encrypting malware that has been based upon an open source Ransomware. It is capable of encrypting various file formats which can make those files unusable unless they are decrypted using a private decryption key. The ransomware has been found to be using strong encryption key and immediately stores the decryption key on remote servers. [email protected] virus has been identified to deceive users by means of spam mails and software bundles to spread itself. The spam mails are specially crafted to catch receiver’s attention as they carry details such as product information, invoice, purchase order, banking update and such with names of reputed firms. The contents give an impression of legitimacy and asks users to click on links provided within the text to obtain more information. These links are used to inject scripts that allows the payload to download itself and start the encryption process. [email protected] virus can also use software bundles to hide itself as legitimate archive files in .rar or .zip format. The files then get executed during installation process along with other applications. The ransomware has been designed to scan the system and identify important files that need to be encrypted. It can also make changes to operating system’s registry that allows it to launch itself at system’s reboot. It has been identified to make changes to Run and RunOnce registry keys. The ransomware drops its payload in various sub directories of the system and hence can be difficult to detect manually.
[email protected] virus soon starts its encryption process after identifying important files within the system. It has been found to be using AES-128 and RSA-2048 encryption algorithm to encrypt files and immediately sends the decryption key to remote servers. The files that get encrypted can be identified with long strings that contain random letters and characters and end with an extension. It drops a ransom message in a file that displays the content regarding the attack. [email protected] virus informs users that their files can only be recovered using a special software and unique decryption key that can be obtained by contacting them to negotiate a deal regarding the ransom amount. To gain trust of affected users [email protected] virus asks them to attach three encrypted files that will be decrypted. If not contacted within seven days the unique decryption key will be deleted from remote server. However users should not contact them and instead can follow these steps to remove the ransomware from their PC.
Remove [email protected] virus From Your PC
Step 1: Remove [email protected] virus in Safe Mode with Command Prompt
- First of all disconnect your PC with network connection.
- Click restart button and keep pressing F8 key regularly while system restart.

- You will see “Windows Advanced Options Menu” on your computer screen.
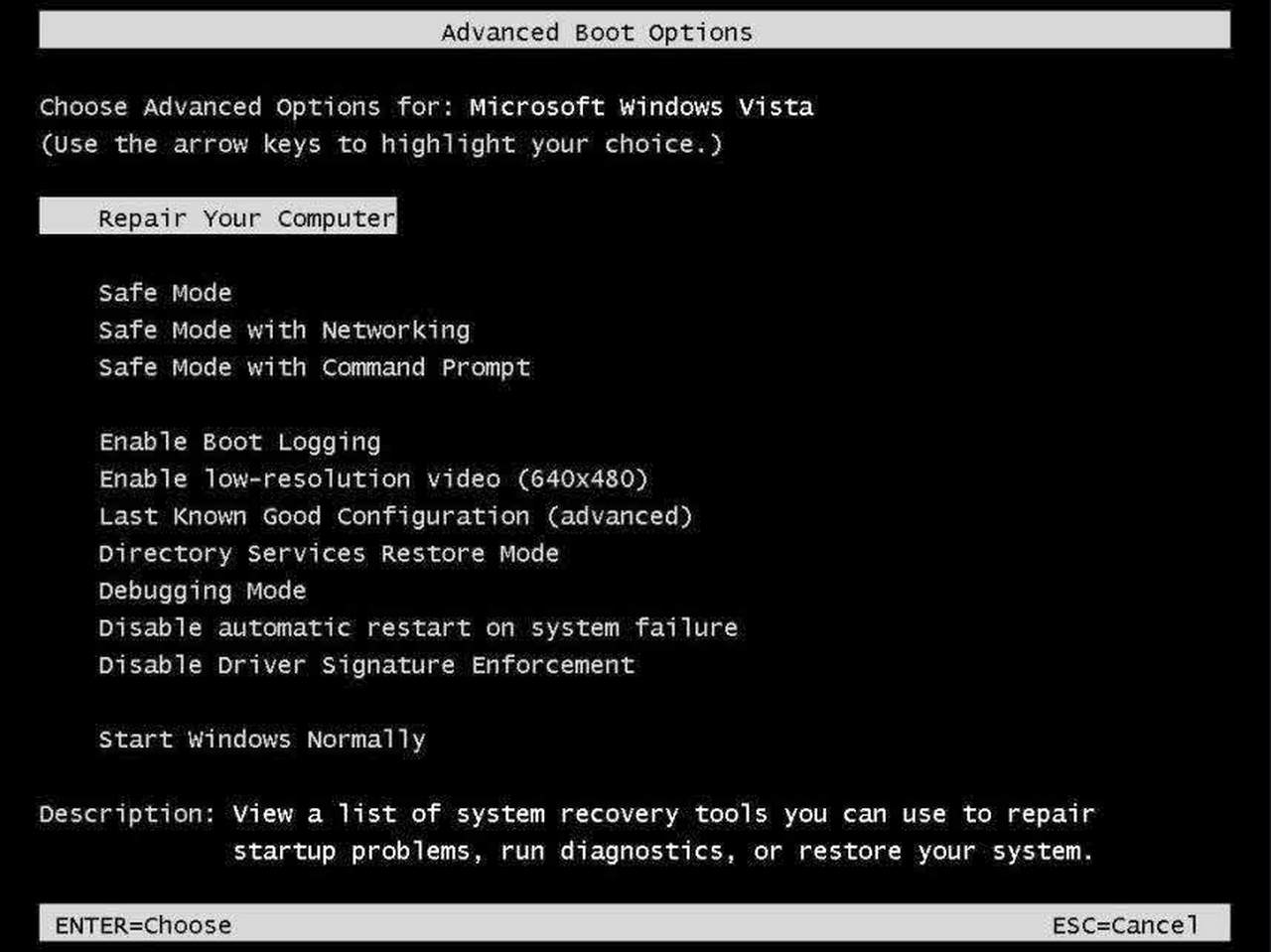
- Select “Safe Mode with Command Prompt” and press Enter key.
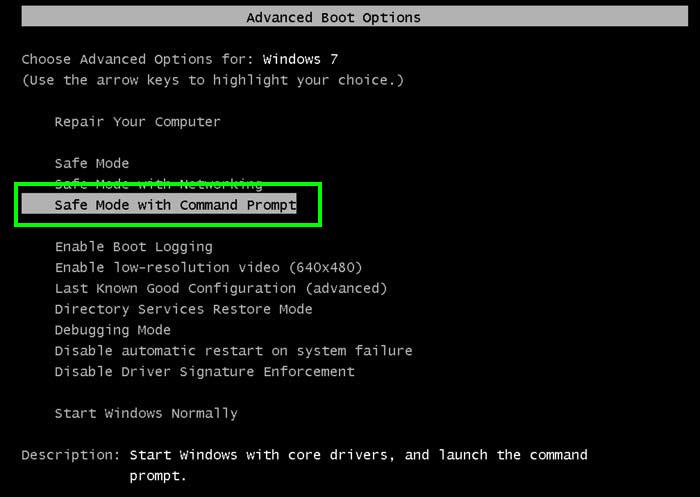
- You must login your computer with Administrator account for full privilege.
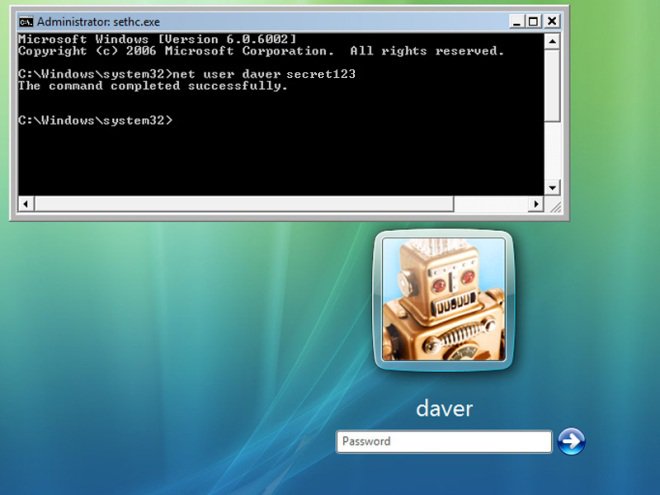
- Once the Command Prompt appears then type rstrui.exe and press Enter
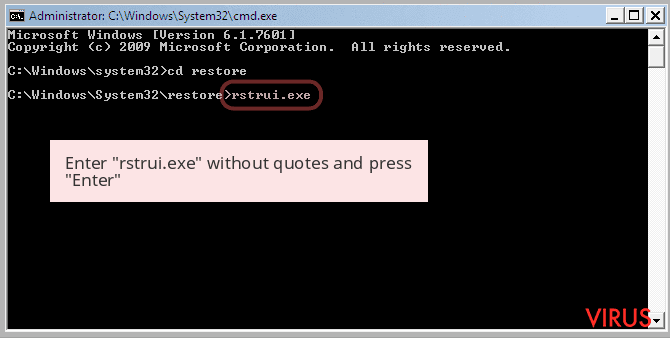
- Now follow the prompts on your screen to complete system restore.
Step 2: Remove [email protected] virus using MSConfig in Safe Mode:
- Power off your computer and restart again.
- While booting press the “F8 key” continuously to open “Windows Advanced Options Menu”.

- Use the arrow keys to select “Safe Mode” option and press Enter key.

- Once system get started go to Start menu. Type “msconfig” in the search box and launch the application.
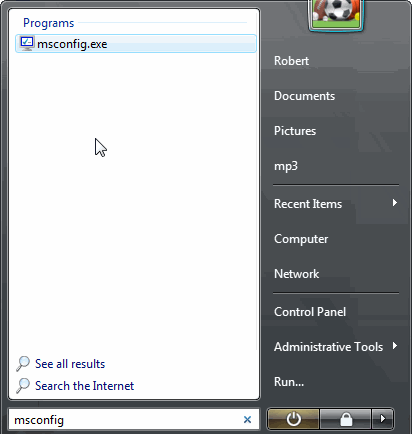
- Go to the Startup tab and look for files from %AppData% or %Temp% folders using rundll32.exe. See an example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N1
- Disable all the malicious entries and save the changes.
- Now restart your computer normally.
Step 3 : Kill Malicious Process Related To [email protected] virus
- Press Alt+Ctrl+Del buttons together.

- It will open the Task manager on your screen.
- Go to Process Tab and find [email protected] virus related process.
- Click the End Process Now button to stop the running process.
Step 4 : Remove [email protected] virus Virus From Registry Entry
- Press “Windows + R” key together to open Run Box.

- Type “regedit” and click OK button.

- Find and remove [email protected] virus related entries.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Runonce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
Now hopefully you have completely removed the [email protected] virus virus from your computer. If you are still get ransom message from the threat or unable to access your files, then it means that virus still remain into your computer. In such situation you don’t have any other option except removing this virus using any powerful malware removal tool.
Whereas if you have any backup of your infected or encrypted files, then you can also reinstall your Windows OS. This will erase all your files and data as along with the [email protected] virus infection. You will get a completely empty computer system with no files. Now you can use your backup to get your files. If you don’t have any backup then using malware removal tool is a better option for you.
If you have any query or question regarding your computer, then you can easily ask your problem to our experts. Go to the Ask Any Question page and get the answer for your query directly from out experts.


