| Drive-by exploit Blackmail Scam is a Worm | |
| Trojan Dropped by Drive-by exploit Blackmail Scam are P2P-Worm.Win32.Franvir, Trojan.Spy.Bafi.G, Spammer.Tedroo.J, Trojan.Zeroaccess.C, Trojan.Vundo, W64.Xpiro, Trojan.Win32.Jorik.Fraud.un, W32/Rimecud.gen.db, Troj_Renos.ACO, Trojan.Bladabindi, Trojan.Alureon.FR, Remat, Trojan.MalLoader.A, Mumuboy Trojan | |
| Related spyware Spyware.SpyMyPC!rem, SideBySide, Edfqvrw Toolbar, PerformanceOptimizer, MessengerBlocker, MySuperSpy, RealAV, Sesui, SpamTool.Agent.bt | |
| Windows Error caused by Drive-by exploit Blackmail Scam are – 0x000000C4, 0x0000002E, Error 0x80240020, 0x0000006E, 0x8024502D WU_E_PT_SAME_REDIR_ID Windows Update Agent failed to download a redirector cabinet file with a new redirectorId value from the server during the recovery., 0x00000049, 0x80248006 WU_E_DS_BADVERSION The current and expected versions of the data store do not match., 0x80246008 WU_E_DM_FAILTOCONNECTTOBITS A download manager operation failed because the download manager was unable to connect the Background Intelligent Transfer Service (BITS)., 0x000000AC, 0x000000D1 | |
| Drive-by exploit Blackmail Scam infects these windows .dll files System.Data.DataSetExtensions.ni.dll, diagER.dll, brci14a.dll, winipsec.dll, evntagnt.dll, System.Workflow.ComponentModel.dll, vds_ps.dll, webservices.dll, MFPlay.dll, imkrapi.dll, kbdsyr1.dll, drmv2clt.dll |
Drive-by exploit Blackmail Scam may have entered your pc through these software. If you have not installed them , then get rid of them LZ100 1.0 , JEFview 1.2 , MenuEverywhere 2.0 , FileMorph 1.1.0 , PongSaver 2.1.1 , Scratch 1.4 , Pet Store Panic 1.0.0 , CrashReport Killer 1.2 , Marble Blast Mobile 1.1 , Copper Plates Desktop Picture |
|

Effective Solution To Uninstall Drive-by exploit Blackmail Scam From PC
Horrible Things That You Must Know About Drive-by exploit Blackmail Scam
Drive-by exploit Blackmail Scam Horse is a dreadful computer malware which is defined as trojan virus. Your computer gets loaded with vicious materials and is not an easy thing to demolish at once. Upon getting onto the system, this notorious virus kills all the running system applications here and then let other virus and malware make their approaches to infect all the parts of the targeted computer system. Your computer will remain infected for long time and if not removed it will screw over last. A trojan virus is renowned for its harmful impact on the PC. It can be brought up by an executable file or documents of freeware, attachments in spam email, fake connections in porn sites and updated news and so on.
In addition, Drive-by exploit Blackmail Scam Horse will bring in more and more harmful viruses into your computer. What is more worse is that it implies that you cannot escape from the attack of this threat unless you delete it from your PC. A trojan virus once settles down inside the targeted computer, establishes connection with the remote server from where it downloads its malicious files and commands for further actions. It is completely a pervert item and will camouflage the entire computer system. Being a trojan virus, it hides itself in the depth of the compromised computer such that anti-virus program does not detect it easily.
Soon enough it starts its malicious activities. Each time you start your PC, all the malign files get activated automatically. In this way, it does not require any permission from you to run its commands. Once the commands of Drive-by exploit Blackmail Scam Horse are executed, they will damage the entire computer system. There will be lot of changes done by trojan virus into your computer system. Registry entries are changed, DNS and configuration settings too are altered. Also, some important and crucial system files are also corrupted that results in improper running of the computer system.
All the installed anti-virus program or security program will be blocked so that Drive-by exploit Blackmail Scam Horse can easily invade the computer system. Disabling anti-virus program makes your PC way too vulnerable and more prone to virus corruption. It is designed to collect sensitive information and data from the compromised PC and transfer it to cyber crooks. These collected information are then used for either illegal purposes or sold to third party for revenue. However, the only thing needed here is the removal of Drive-by exploit Blackmail Scam.
Manual Drive-by exploit Blackmail Scam Removal Guide
Step 1: How to Start your PC in Safe Mode with Networking to Get Rid of Drive-by exploit Blackmail Scam
(For Win 7 | XP | Vista Users)
- first of all PC is to be rebooted in Safe Mode with Networking
- Select on Start Button and Click on Shutdown | Restart option and select OK
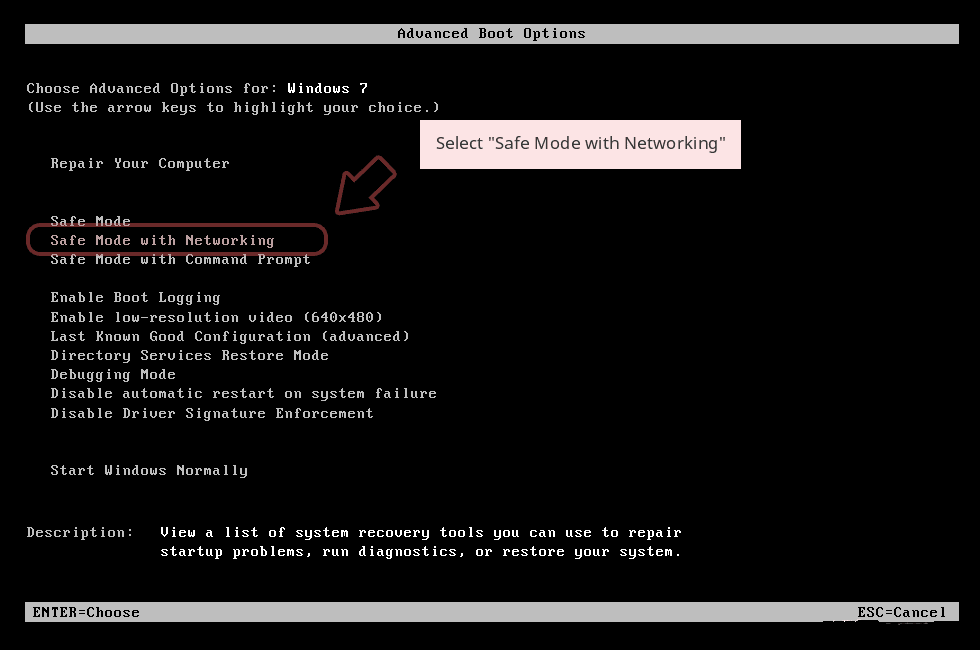
- when the PC restarts, keep tapping on F8 until you don’t get Advanced Boot Options.
- Safe Mode with Networking Option is to be selected from the list.
(For Win 8 | 8.1 | Win 10 Users)
- Click on Power Button near Windows Login Screen
- Keep Shift Button on the keyboard pressed and select Restart Option
- Now Select on Enable Safe Mode with Networking Option

In case Drive-by exploit Blackmail Scam, is not letting your PC to Start in Safe Mode, then following Step is to followed
Step 2: Remove Drive-by exploit Blackmail Scam Using System Restore Process
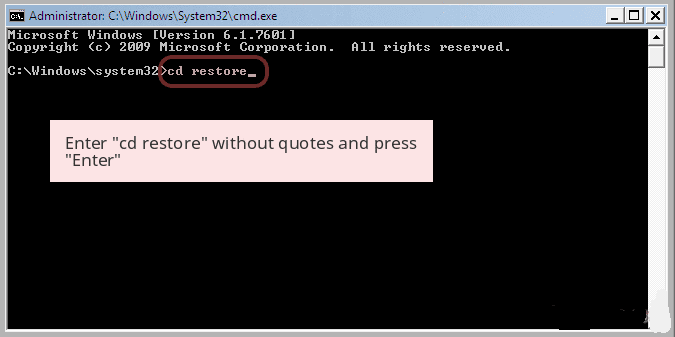
- PC need to be rebooted to Safe Mode with Command Prompt
- As soon as Command Prompt Window appear on the screen, select on cd restore and press on Enter option
Type rstrui.exe and Click on Enter again.

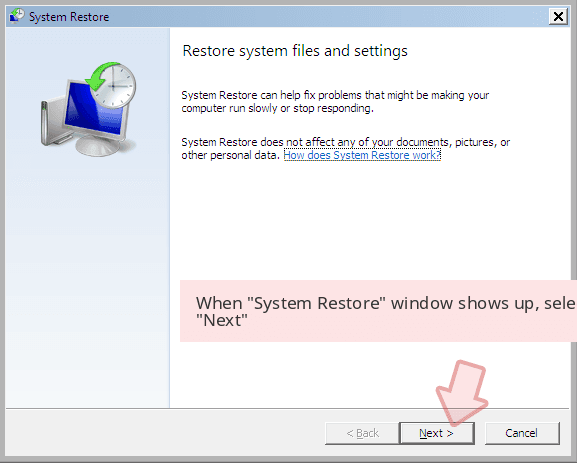
Now users need to Click on Next option and Choose restore point that was the last time Windows was working fine prior to Drive-by exploit Blackmail Scam infection. Once done, Click on Next button.
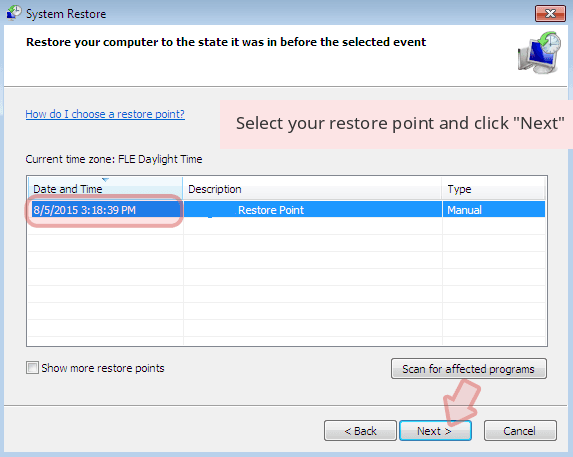
Select Yes to Restore your System and get rid of Drive-by exploit Blackmail Scam infection.

However, if the above steps does not work to remove Drive-by exploit Blackmail Scam, follow the below mentioned steps
Step:3 Unhide All Hidden Files and Folders to Delete Drive-by exploit Blackmail Scam
How to View Drive-by exploit Blackmail Scam Hidden Folders on Windows XP
- In order to show the hidden files and folders, you need to follow the given instructions:-
- Close all the Windows or minimize the opened application to go to desktop.
- Open “My Computer” by double-clicking on its icon.
- Click on Tools menu and select Folder options.
- Click on the View tab from the new Window.
- Check the Display contents of the system folders options.
- In the Hidden files and folders section, you need to put a check mark on Show hidden files and folders option.
- Click on Apply and then OK button. Now, close the Window.
- Now, you can see all the Drive-by exploit Blackmail Scam related hidden files and folders on the system.

How to Access Drive-by exploit Blackmail Scam Hidden folders on Windows Vista
- Minimize or close all opened tabs and go to Desktop.
- Go to the lower left of your screen, you will see Windows logo there, click on Start button.
- Go to Control Panel menu and click on it.
- After Control Panel got opened, there will two options, either “Classic View” or “Control Panel Home View”.
- Do the following when you are in “Classic View”.
- Double click on the icon and open Folder Options.
- Choose View tab.
- Again move to step 5.
- Do the following if you are “Control Panel Home View”.
- Hit button on Appearance and Personalization link.
- Chose Show Hidden Files or Folders.
- Under the Hidden File or Folder section, click on the button which is right next to the Show Hidden Files or Folders.
- Click on Apply button and then hit OK. Now, close the window.
- Now, to show you all hidden files or folders created by Drive-by exploit Blackmail Scam, you have successfully considered Windows Vista.

How to Unhide Drive-by exploit Blackmail Scam Created Folders on Windows 7
1. Go to the desktop and tap on the small rectangle which is located in the lower-right part of the system screen.
2. Now, just open the “Start” menu by clicking on the Windows start button which is located in the lower-left side of the PC screen that carries the windows logo.
3. Then after, look for the “Control Panel” menu option in the right-most row and open it.
4. When the Control Panel menu opens, then look for the “Folder Options” link.
5. Tap over the “View tab”.
6. Under the “Advanced Settings” category, double click on the “Hidden Files or Folders” associated with Drive-by exploit Blackmail Scam.
7. Next, just select the check-box in order to Show hidden files, folders, or drives.
8. After this, click on “Apply” >> “OK” and then close the menu.
9. Now, the Windows 7 should be configured to show you all hidden files, folders or drives.

Steps to Unhide Drive-by exploit Blackmail Scam related Files and Folders on Windows 8
- First of all, power on your Windows PC and click on start logo button that is found in left side of the system screen.
- Now, move to program lists and select control panel app.
- When Control panel is open completely, click on more settings option.
- After, you will see a Control panel Window and then you choose “Appearance and Personalization” tab.
- In Advance settings dialogue box, you need to tick mark on Show hidden files and folders and clear the check box for Hide protected system files.
- Click on Apply and Ok button. This apply option helps you to detect and eradicate all types of Drive-by exploit Blackmail Scam related suspicious files.
- Finally, navigate your mouse cursor on close option to exit this panel.
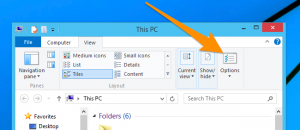
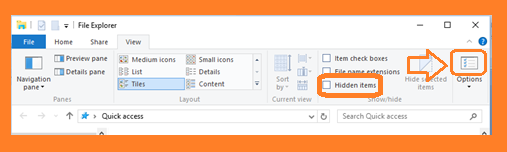
How to View Drive-by exploit Blackmail Scam associated folders on Windows 10
1. Open the folder if you wish to unhide files.
2. Search and Click on View in Menu bar
3. In Menu click on to view folder options.
4. Again click on View and Enable Radio Button associated with Show hidden files created by Drive-by exploit Blackmail Scam, folder and drive.
5. Press apply and OK.
Step 4: Press Start Key along with R- copy + paste the below stated command and Click on OK
notepad %windir%/system32/Drivers/etc/hosts
- This will open up a new file, in case if your system has been hacked, some IP’s will be shown at the bottom of the screen

Click on the Start Menu, Input “Control Panel” in the search box —> Select. Network and Internet —> Network and Sharing Center —> Next Change Adapter Settings. Right-click your Internet connection —> Select on Properties.
- In case if you find Suspicious IP in the local host –or if you are finding it difficult and have any problem then submit question to us and we will be happy to help you.


