â
Description about Hidden-Peach Ransomware
Security Researchers detected that this Hidden-Peach Ransomware is still in the development phase. Experts discovered this ransom threat on Gifthub.com, it is a platform where you can write and share codes. According to the initial security reports of threats experts, the developers behind the Hidden-Peach project is not so skilled enough and it may possible that this ransom threat may achieve upgrades in future. It is proved that this ransom virus has been based on the educational ransomware project of Hidden Tear project that has been published by Utku Sen. It is worthless to explain that the Hidden-Peach Ransomware is not the only one that has been published under the category of educational ransomware based on educational ransom threat.
Hidden-Peach Ransomware : Designed to educate the users about ransomware
As the genuine version of Hidden Tear has been eliminated from the Open Web, many of threat makers have already copied the source code of it many a times. Researchers alerts the users that some of the new and enhanced variants of this Hidden Tear project may be found on the forums very easily. It is assumed that the developers of this Hidden-Peach Ransomware taken the source code copy of the Hidden Tear project and used it as the starting point into it. In the detections Hidden-Rear has been detected in the program information section for this ransom virus. Experts explains the users this ransom threat using Hidden-Peach similar as the Microsoft Corporation uses "Longhorn" to hiding the Windows Vista in the past times.
Hidden-Peach Ransomware has been designed with limited characteristics
In the initial stage Hidden-Peach Ransomware only programmed to target only one directory of the victims system. This ransom threat uses strong encryption method of AES-256 cipher to encipher the users files. Once the encryption has been successfully finished then the only way to decrypt your files back by using a decryption tool or key which can only provide you the hackers. It uses the limited encryption technique in order to identify the infected files of the victims and try to fix the problems after receiving the ransom payment. According to the suggestions of the experts users should always keep a backup of your files and folders to fight against this kind of ransom attacks. Infected victim can use a trusted anti-malware on their system to remove Hidden-Peach Ransomware completely and permanently.
Free Scan your Windows PC to detect Hidden-Peach Ransomware
Remove Hidden-Peach Ransomware From Your PC
Step 1: Remove Hidden-Peach Ransomware in Safe Mode with Command Prompt
- First of all disconnect your PC with network connection.
- Click restart button and keep pressing F8 key regularly while system restart.

- You will see “Windows Advanced Options Menu” on your computer screen.
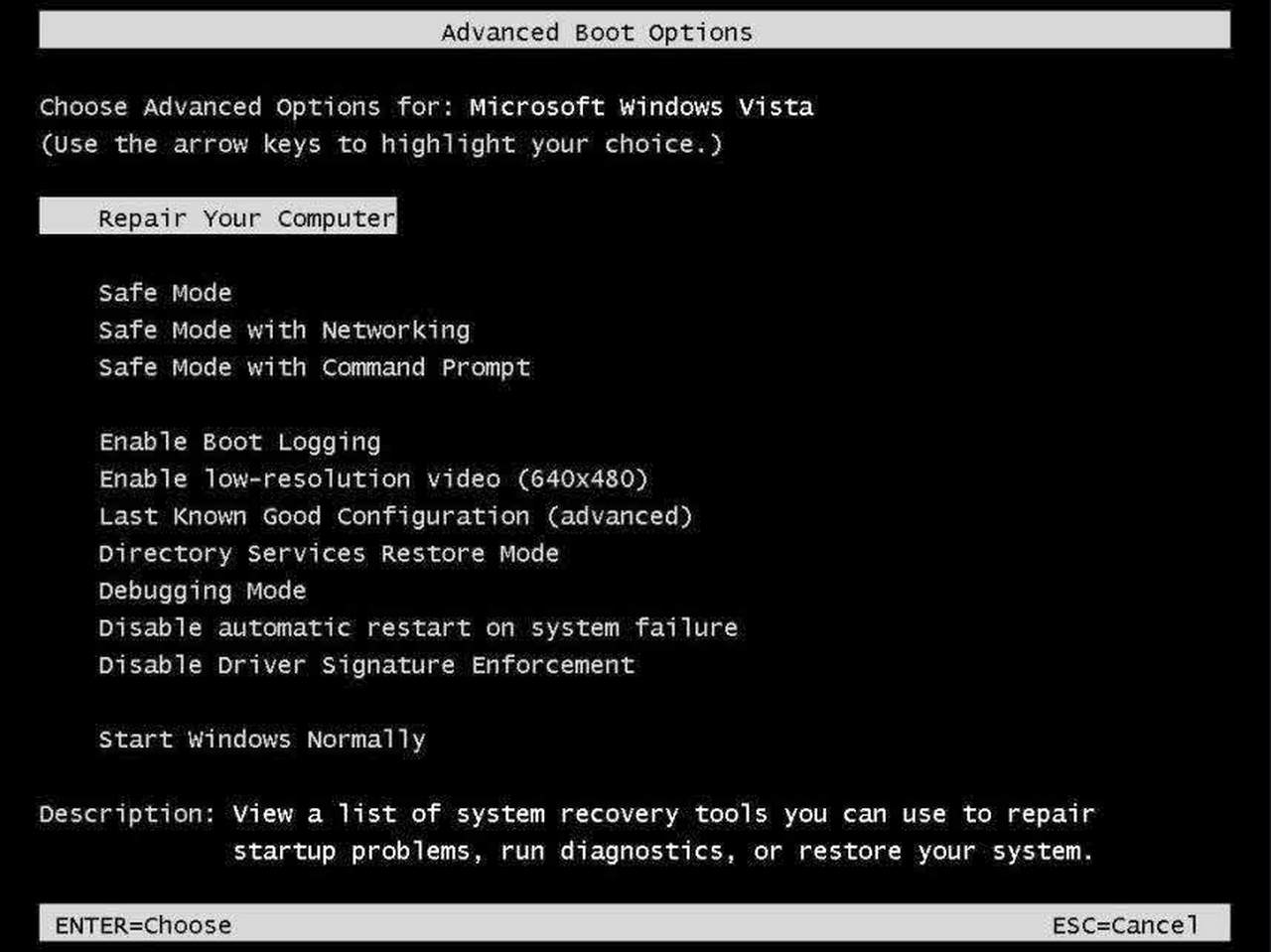
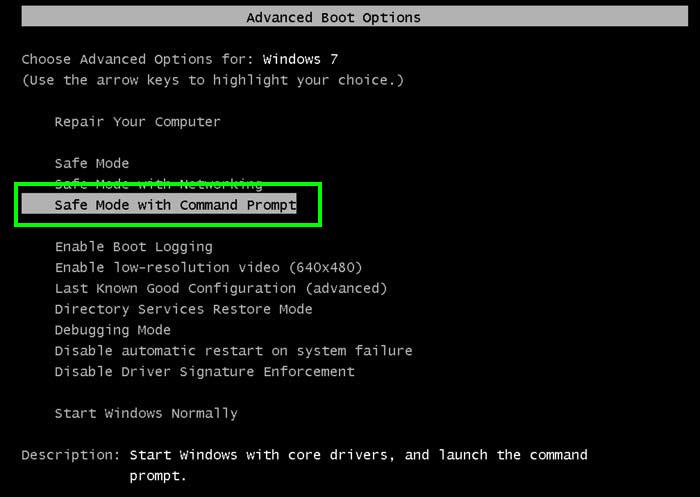
- Select “Safe Mode with Command Prompt” and press Enter key.
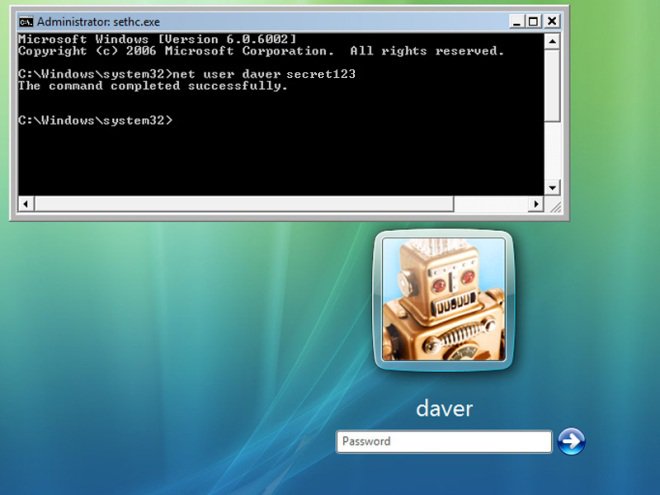
- You must login your computer with Administrator account for full privilege.
- Once the Command Prompt appears then type rstrui.exe and press Enter
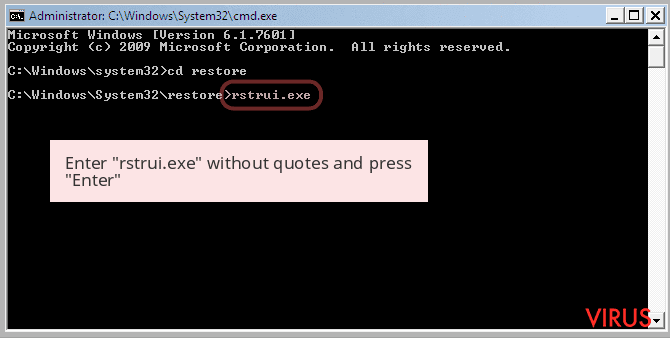
- Now follow the prompts on your screen to complete system restore.
Step 2: Remove Hidden-Peach Ransomware using MSConfig in Safe Mode:
- Power off your computer and restart again.
- While booting press the “F8 key” continuously to open “Windows Advanced Options Menu”.

- Use the arrow keys to select “Safe Mode” option and press Enter key.

- Once system get started go to Start menu. Type “msconfig” in the search box and launch the application.
- Go to the Startup tab and look for files from %AppData% or %Temp% folders using rundll32.exe. See an example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N1
- Disable all the malicious entries and save the changes.
- Now restart your computer normally.
Step 3 : Kill Malicious Process Related To Hidden-Peach Ransomware
- Press Alt+Ctrl+Del buttons together.

- It will open the Task manager on your screen.
- Go to Process Tab and find Hidden-Peach Ransomware related process.
- Click the End Process Now button to stop the running process.
Step 4 : Remove Hidden-Peach Ransomware Virus From Registry Entry
- Press “Windows + R” key together to open Run Box.

- Type “regedit” and click OK button.

- Find and remove Hidden-Peach Ransomware related entries.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Runonce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
Now hopefully you have completely removed the Hidden-Peach Ransomware virus from your computer. If you are still get ransom message from the threat or unable to access your files, then it means that virus still remain into your computer. In such situation you don’t have any other option except removing this virus using any powerful malware removal tool.
Whereas if you have any backup of your infected or encrypted files, then you can also reinstall your Windows OS. This will erase all your files and data as along with the Hidden-Peach Ransomware infection. You will get a completely empty computer system with no files. Now you can use your backup to get your files. If you don’t have any backup then using malware removal tool is a better option for you.
If you have any query or question regarding your computer, then you can easily ask your problem to our experts. Go to the Ask Any Question page and get the answer for your query directly from out experts.




