| Warning, many anti-virus scanner have detected [email protected] ransomware as threat to your computer | ||
| [email protected] ransomware is flagged by these Anti Virus Scanner | ||
| Anti Virus Software | Version | Detection |
| Zoner | 2018.1.3347 | Non-specific |
| CrowdStrike Falcon (ML) | 8.6.651813 | [email protected] ransomware.CC |
| AutoShun | 4.523124 | Variant of Win64/[email protected] ransomware.C |
| ZDB Zeus | 4.3.807 | Adware.Rotator, MalwareStopper |
| Suggestion: Uninstall [email protected] ransomware Completely – Free Download | ||
[email protected] ransomware may have entered your pc through these software. If you have not installed them , then get rid of them Artwork Locator 10.3.0.3.1 , Mr. Cats Quest 3.3.1 , SlingShot 2.0.3 , DoodleGeddon 1.6.5 , Froggy’s Songs 1.2.5 , Noatikl 2.5.22 , Youda Farmer 2: Save the Village 2.0 , Aspire 1.0 , Bus RATP Widget 1.0 , MapDiscovery 0.6 , TypeMetal 2.0.4 , MacBook Family Icons 1.3 , iFreeMem , GPL Arcade Volleyball 1.0 , iMusic Valet 1.0.2 , PocketiCalScreenSaver 1.0 , ViMediaManager 0.7.0.1.13 , Emicsoft iPod to Transfer |
|
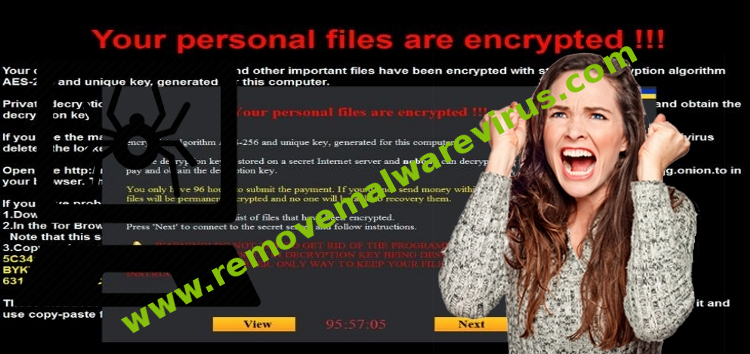
Detail Analysis Of [email protected] ransomware
[email protected] ransomware is a dangerous file encrypting virus that can also delete those files if the ransom amount is not payed within the specified time frame by the malware. It has been detected that the ransomware is based upon an open source code which is publicly available and has been exploited by other ransomware before. The virus has been designed to download the file encrypting scripts as soon as it installs within the system. [email protected] ransomware scans the system for the important files that need to be encrypted and which can help in bringing the system to a stop. Thus users will be left with no other option but to pay the ransom amount that they have been informed about. Upon successfully encrypting the files, it leaves a ransom note behind that is used to inform users regarding the attack and the process that they need to carry out if they want to obtain a decryption key that is promised to help them with restoring their files in working condition. [email protected] ransomware should not be trusted by users to fulfill its promise as such malware attacks are only designed to obtain money from the affected users. Ransomware such as these are also known to ask users to install a decryption software that will help in the decryption process, however such programs can hide other malicious scripts that can be used to damage the system further and carryout specific attacks.
[email protected] ransomware gets an easy access to a vulnerable system through means of spam mails and software bundles. The spam messages are specially crafted to deceive users and drop payload within the system. They carry design template of reputed firms that helps in making them appear legitimate. The contents within are embedded with scripts that seek permission from receiver to enable the macros that immediately install [email protected] ransomware payload. It can also use software bundles to hide itself as a legitimate program and can thus install when users select auto installation option. Such bundles are commonly available on freeware file sharing sites. Soon after establishing itself the ransomware makes changes to registry settings of the operating system to allow auto-run of its executable file. [email protected] ransomware then encrypts files of various formats using AES and RSA encryption algorithms and renames them with long character strings. The files become unusable as they cannot be executed by the operating system. It leaves a ransom note that warns users to pay the ransom amount or their files will be deleted at regular interval. Instead of paying a ransom amount users can remove it using this guide.
Free Scan your Windows PC to detect [email protected] ransomware
A: How To Remove [email protected] ransomware From Your PC
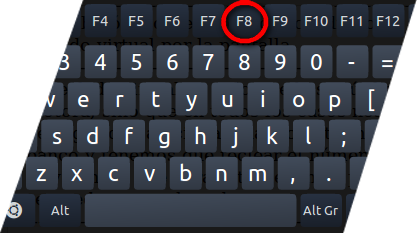
Step: 1 How to Reboot Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.
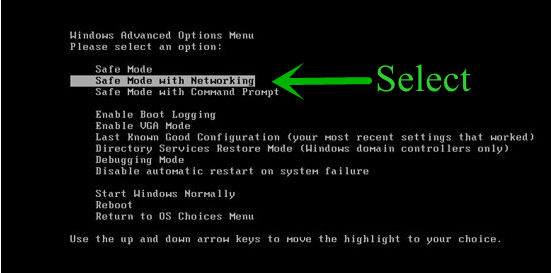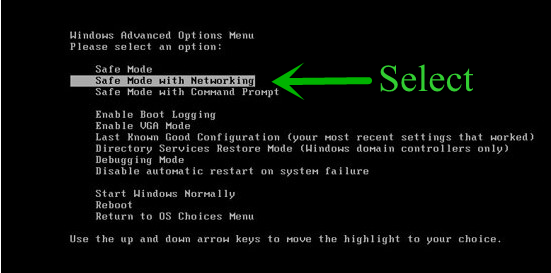
- From the boot menu, select Safe Mode with Networking using the arrow keys.
Step: 2 How to Kill [email protected] ransomware Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard

- It will Open Task manager on Windows
- Go to Process tab, find the [email protected] ransomware related Process.
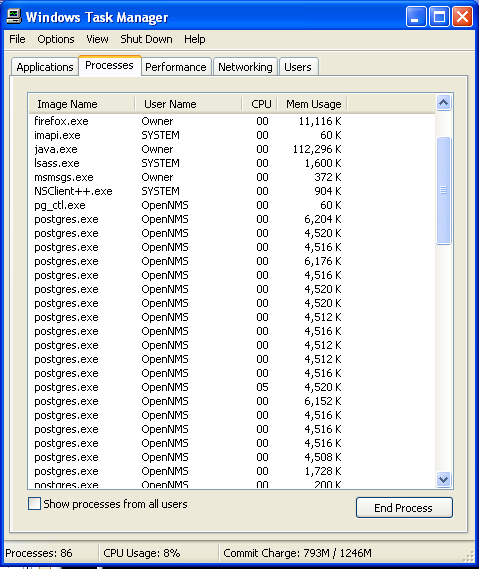
- Now click on on End Process button to close that task.
Step: 3 Uninstall [email protected] ransomware From Windows Control Panel
- Visit the Start menu to open the Control Panel.
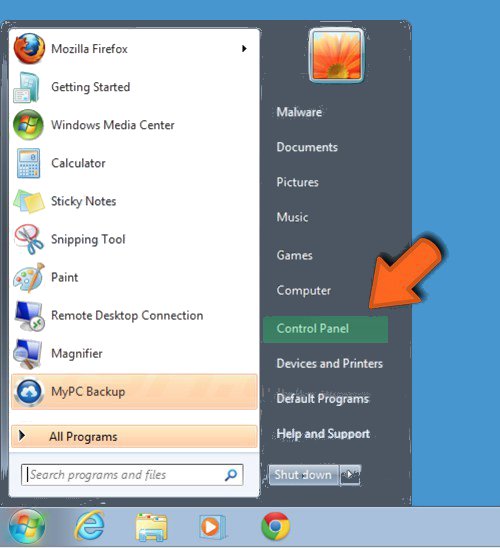
- Select Uninstall a Program option from Program category.
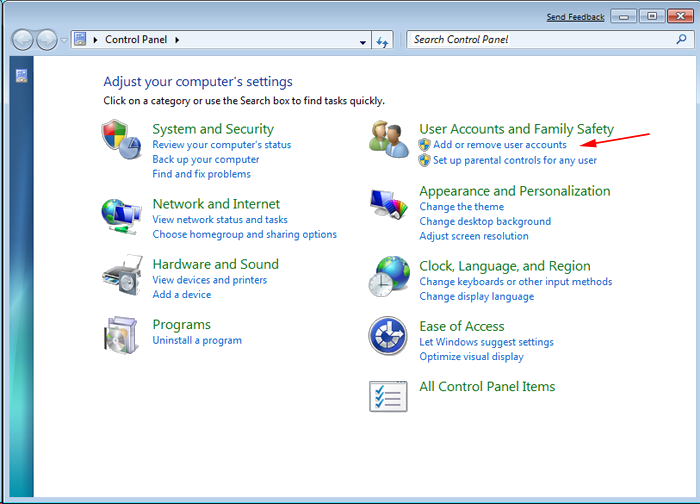
- Choose and remove all [email protected] ransomware related items from list.

B: How to Restore [email protected] ransomware Encrypted Files
Method: 1 By Using ShadowExplorer
After removing [email protected] ransomware from PC, it is important that users should restore encrypted files. Since, ransomware encrypts almost all the stored files except the shadow copies, one should attempt to restore original files and folders using shadow copies. This is where ShadowExplorer can prove to be handy.
Download ShadowExplorer Now
- Once downloaded, install ShadowExplorer in your PC
- Double Click to open it and now select C: drive from left panel
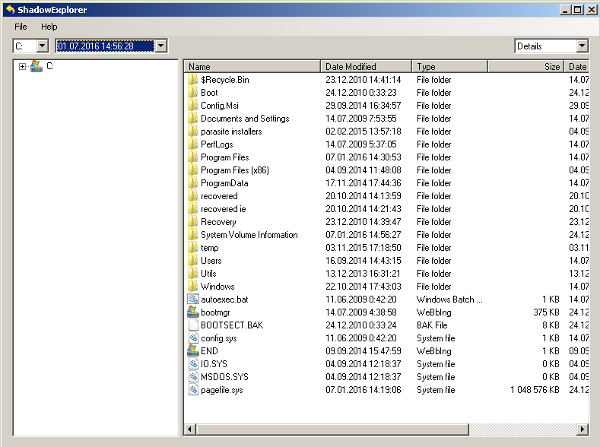
- In the date filed, users are recommended to select time frame of atleast a month ago
- Select and browse to the folder having encrypted data
- Right Click on the encrypted data and files
- Choose Export option and select a specific destination for restoring the original files
Method:2 Restore Windows PC to Default Factory Settings
Following the above mentioned steps will help in removing [email protected] ransomware from PC. However, if still infection persists, users are advised to restore their Windows PC to its Default Factory Settings.
System Restore in Windows XP
- Log on to Windows as Administrator.
- Click Start > All Programs > Accessories.
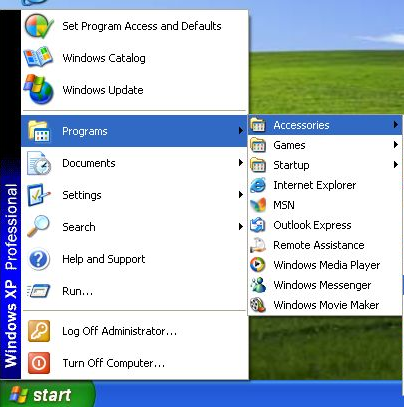
- Find System Tools and click System Restore
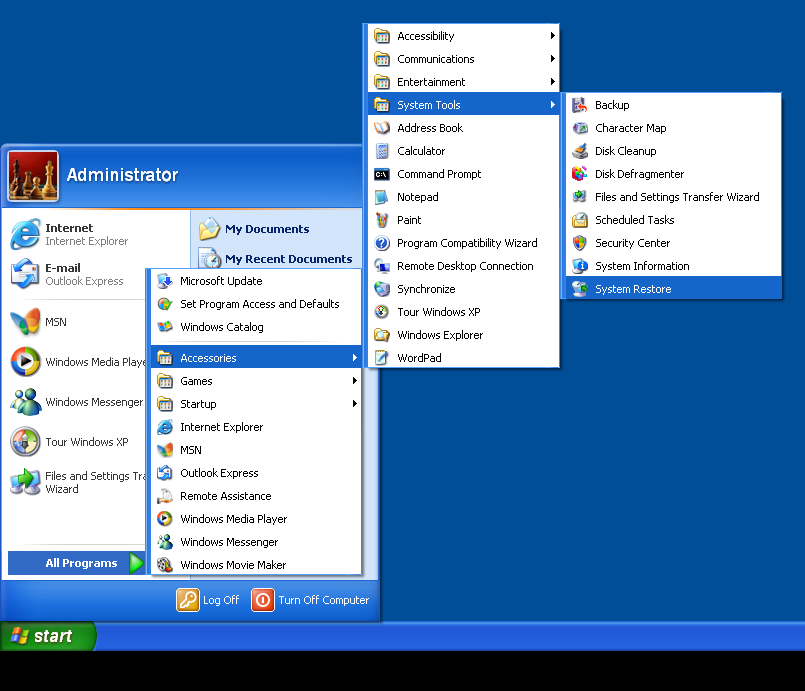
- Select Restore my computer to an earlier time and click Next.
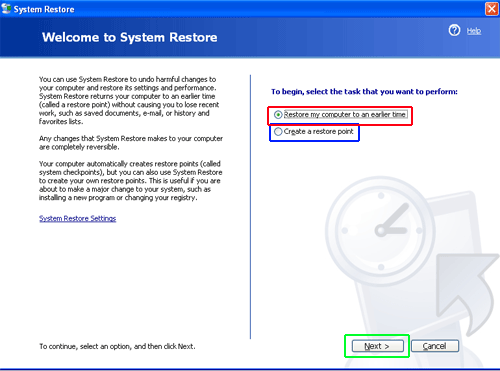
- Choose a restore point when system was not infected and click Next.
System Restore Windows 7/Vista
- Go to Start menu and find Restore in the Search box.

- Now select the System Restore option from search results
- From the System Restore window, click the Next button.

- Now select a restore points when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 8
- Go to the search box and type Control Panel

- Select Control Panel and open Recovery Option.

- Now Select Open System Restore option

- Find out any recent restore point when your PC was not infected.

- Click Next and follow the instructions.
System Restore Windows 10
- Right click the Start menu and select Control Panel.

- Open Control Panel and Find out the Recovery option.

- Select Recovery > Open System Restore > Next.

- Choose a restore point before infection Next > Finish.

Method:3 Using Data Recovery Software
Restore your files encrypted by [email protected] ransomware with help of Data Recovery Software
We understand how important is data for you. Incase the encrypted data cannot be restored using the above methods, users are advised to restore and recover original data using data recovery software.

