Here in this section you would get proper guide to remove this malware threat from the deceived computer system.
Threat Details
| Threat Name | Your System data has been compromised |
| Threat Type | Adware |
| Infected System | XP, Win 32/64, 8.1, Vista, 7, 10, 8. |
| Affected Browser | Mozilla Firefox, Google Chrome, Edge, Internet Explorer. |
| Risk level | Low |
| File Decryption | Possible |
| Distributive Ways | Corrupted external drives, download free things from untrusted websites, email spam campaigns, etc. |
Info About Your System data has been compromised
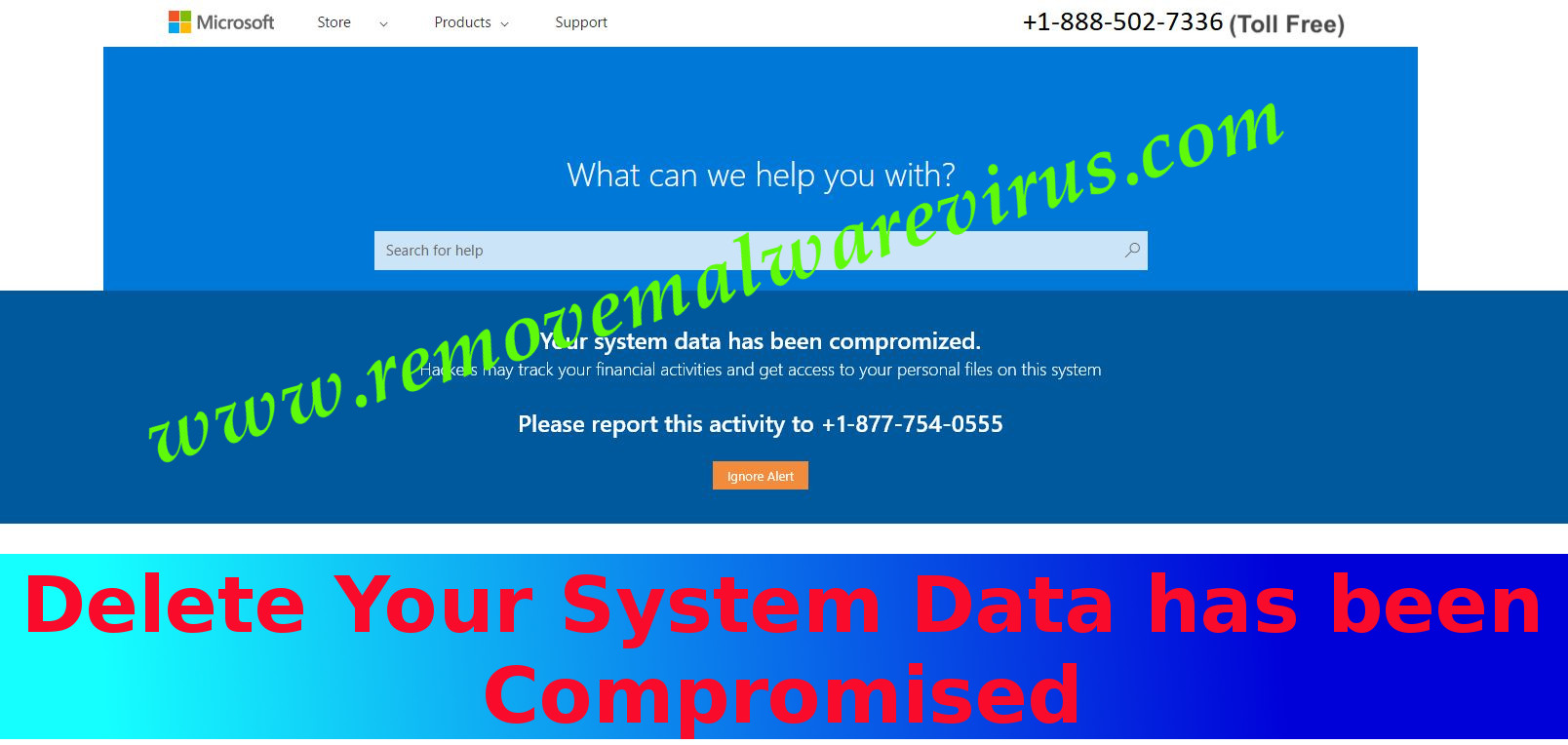
Your System data has been compromised is a deleterious kind of system infection which can be categorized under the adware classification of virus. This is just a deceptive push notification that appears on the desktop of the compromised machines during the browsing sessions. It is capable of contaminating different types of Windows based computer system like Vista, 8.1, 7, Win 32/64, 8, XP, 10 etc and several most well known Web Search Engine Browser like Internet Explorer, Safari, Microsoft Edge, Google Chrome, Mozilla Firefox, Opera etc. The main intension behind the creation of this malware is to extort some enormous amount of illegal revenue from the users of the deceived computer system. Its screen locking feature allows the misleading users into believing that actually their system are got contaminated with some serious infection and therefore must immediately take some serious action for its removal.
Properties Of Your System data has been compromised
Your System data has been compromised is a Tech Support Scam which is operated by the uncertified system assistance agents in India. It mainly aims to trick the victim into calling the provided tech support number like 877-754-0555 through displaying some misleading security alerts on the web sites. It can very soundlessly get encroached into the compromised Operating System by using various dispersal techniques such as fake software updater, download free things from untrusted websites, corrupted external drives, peer to peer file sharing network, email spam campaigns, free file hosting websites, untrustworthy downloading sources, software bundling method, pornographic or adult sites, clicking suspicious pop-up ads, hacked executable files, untrustworthy third party software down-loader, fake invoices, online gaming server, reading junked e-mail attachments, click commercial ads embedded malicious codes and many others. It is advertisement supported program which mislead the users by showing some kind of malicious pop-up windows for fake notifications on the screen of the victimized Operating System.
Defects Caused By Your System data has been compromised
Your System data has been compromised can very easily get connected to the suspicious servers and able to download several malicious programs directly into the affected system without any user authorizations. It can deactivates the antivirus programs and firewall protection settings of the polluted computer system. It is capable of gathering some confidential informations of the users by monitoring their browsing habits.
How To Get Rid Of Your System data has been compromised
As you detected your system is got contaminated by Your System data has been compromised then it becomes essential to get rid of such malware threat by using either automatic or manual techniques as soon as possible.
Click to Free Scan for Your System data has been compromised on PC
Learn To Remove Your System data has been compromised Using Manual Methods
Phase 1 : Show Hidden Files To Delete Your System data has been compromised Related Files And Folders
1. For Windows 8 or 10 Users : From the Ribbon’s View in My PC click on Options icon.

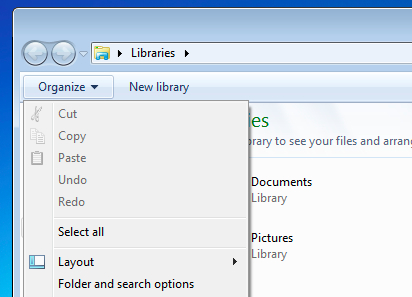
2. For Windows 7 or Vista Users : Open My Computer and tap on Organize button on the upper left corner and then to Folder and Search Options from the drop down menu.
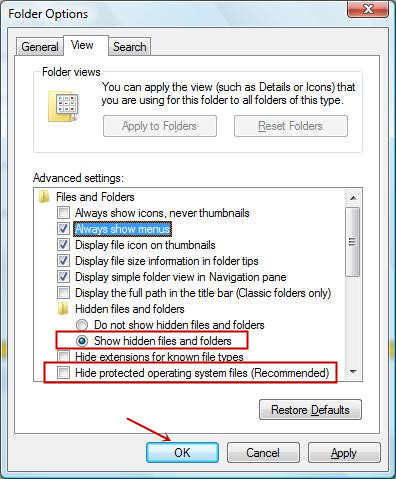
3. Now go to the View tab and enable Show hidden files and folder options and then uncheck the Hide protected system operating files checkbox option below.
4. Finally look for any suspicious files in the hidden folders as given below and delete it.
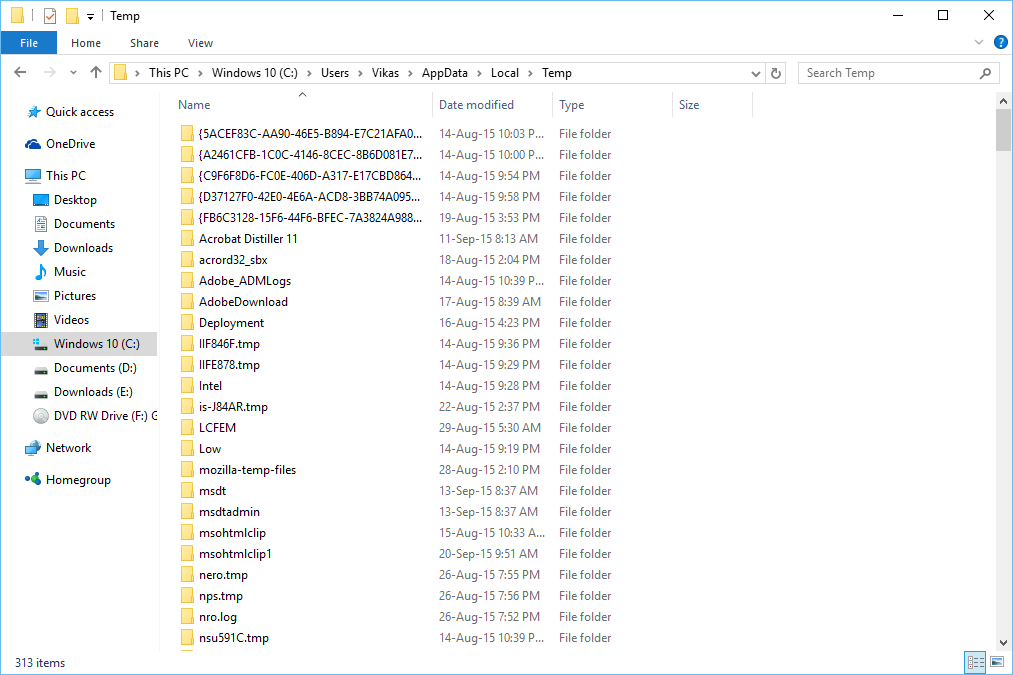
- %AppData%\[adware_name]
- %Temp%\[adware_name]
- %LocalAppData%\[adware_name].exe
- %AllUsersProfile%random.exe
- %CommonAppData%\[adware_name]
Phase 2 : Get Rid of Your System data has been compromised Related Extensions Related From Different Web Browsers
From Chrome :
1. Click on Menu icon, hover through More Tools then tap on Extensions.

2. Now click on Trash icon on the extensions tab there next to suspicious extensions to remove it.

From Internet Explorer :
1. Click on Manage add-ons option from the drop down menu on going through Gear icon.
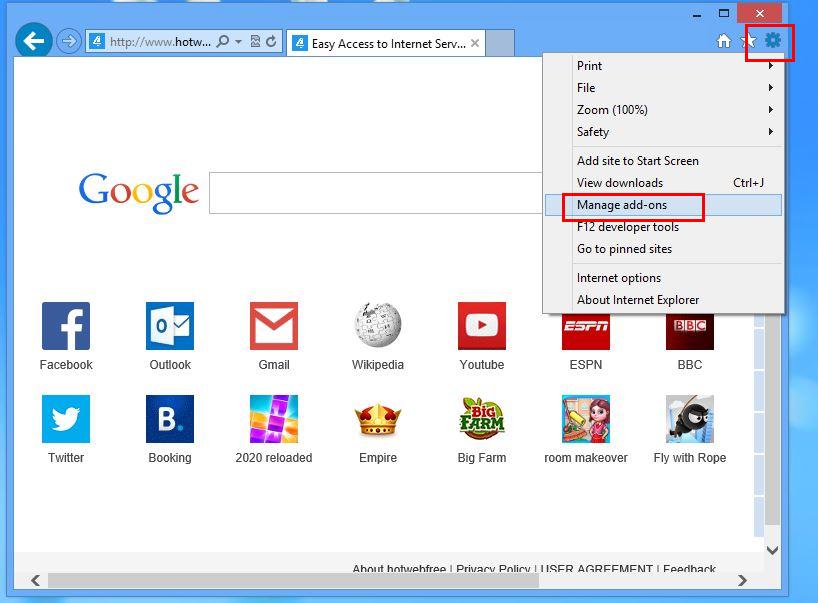
2. Now if you find any suspicious extension in the Toolbars and Extensions panel then right click on it and Delete option to remove it.
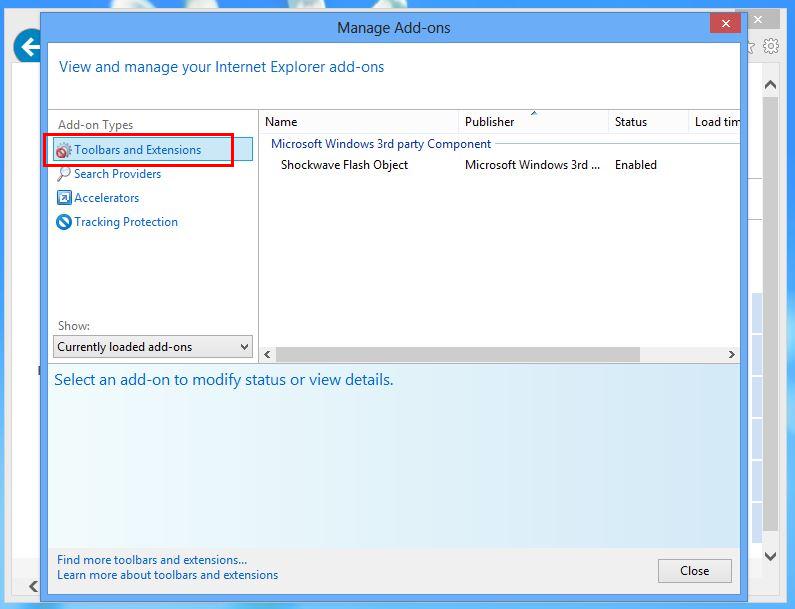
From Mozilla Firefox :
1. Tap on Add-ons on going through Menu icon.

2. In the Extensions tab click on Disable or Remove button next to Your System data has been compromised related extensions to remove them.

From Opera :
1. Press Opera menu, hover to Extensions and then select Extensions manager there.
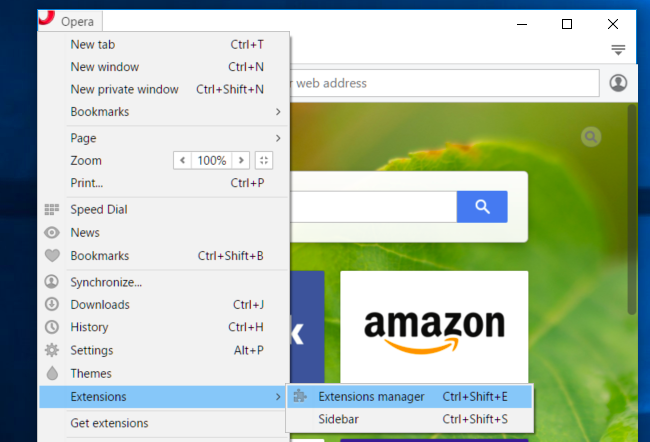
2. Now if any browser extension looks suspicious to you then click on (X) button to remove it.
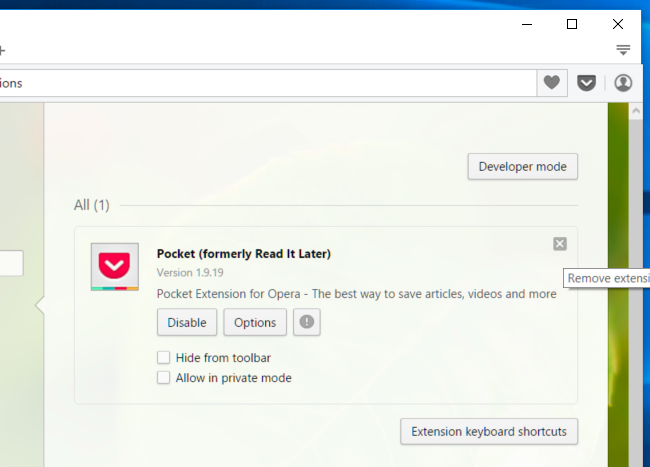
From Safari :
1. Click Preferences… on going through Settings Gear icon.
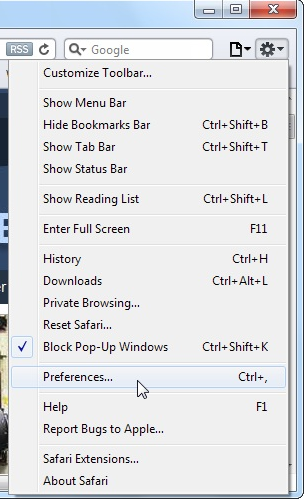
2. Now on Extensions tab click on Uninstall button to remove it.
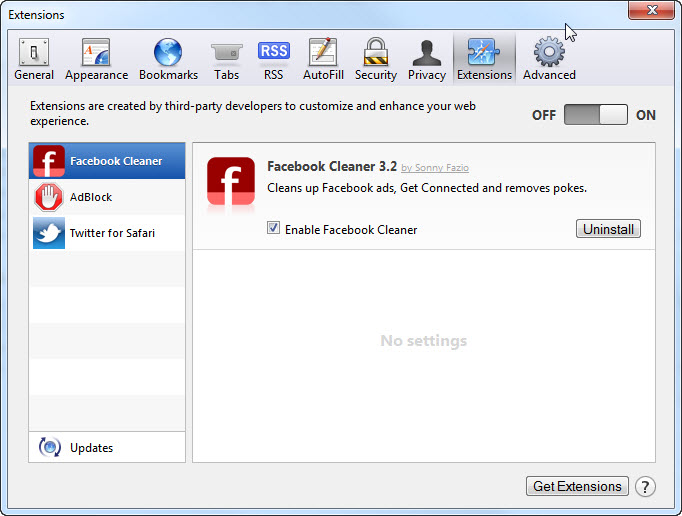
From Microsoft Edge :
Note:–As there is no option for Extension Manager in Microsoft Edge so in order to sort out issues related with adware programs in MS Edge you can change its default homepage and search engine.
Change Default Homepage of Ms Edge –
1. Click on More(…) followed by Settings and then to Start page under Open With section.

2. Now select View advanced settings button and then in Search in the address bar with section, you can select Google or any other homepage as your preference.
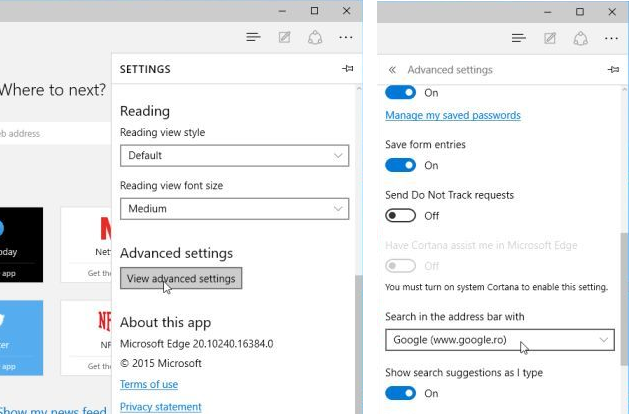
Change Default Search Engine Settings of Ms Edge –
1. Select More(…) then Settings followed by View advanced settings button.

2. Under Search in the address bar with box click on <Add new>. Now you can choose from the available list of search providers or add you preferred search engine and click Add as default.

Phase 3 : Block Unwanted Pop-ups from Your System data has been compromised On Different Web Browsers
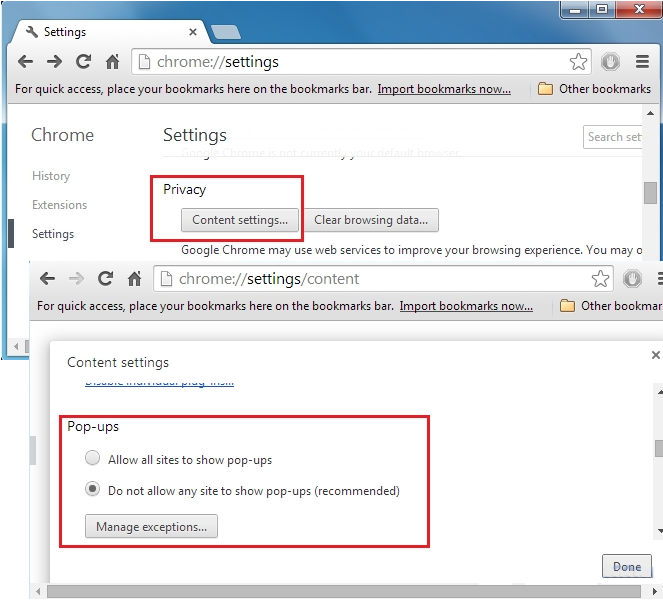
1. Google Chrome : Click Menu icon → Settings → Show advanced settings… → Content Settings… under Privacy section → enable Do not allow any site to show pop-ups (recommended) option → Done.
2. Mozilla Firefox : Tap on Menu icon → Options → Content panel → check Block pop-up windows in Pop-ups section.

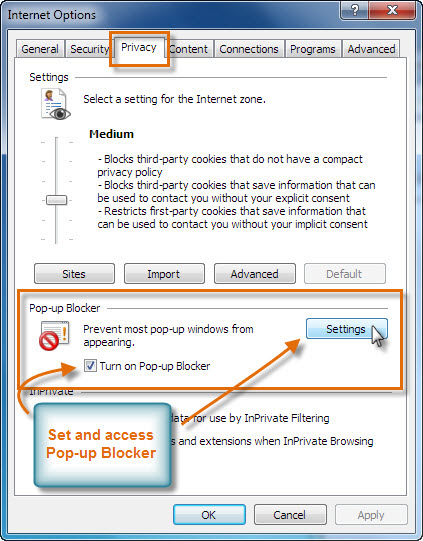
3. Internet Explorer : Click Gear Settings icon → Internet Options → in Privacy tab enable Turn on Pop-up Blocker under Pop-up Blocker Section.
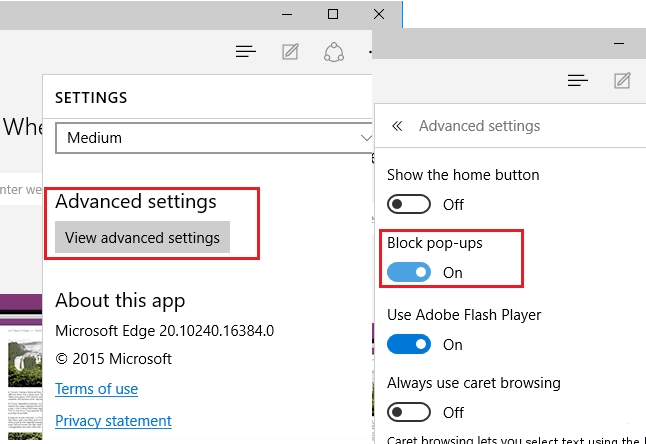
4. Microsoft Edge : Press More(…) option → Settings → View advanced settings → toggle on Block pop-ups.
Still having troubles in removing Your System data has been compromised from your compromised PC ? Then you don’t need to worry. You can feel free to ask questions to us about malware related issues.




