Hello friends. My antivirus program has detected Trojan-Cliker.VBS.Agent.dj in my system a couple of days ago. I already knew that Trojan horse threats are very dangerous and hence I had immediately tried to remove it from my system. Once after the successful quarantine of this Trojan horse from my PC with the antivirus, it reappeared in the next system startup. From then I am searching for some effective removal solutions but nothing found useful so far. If anybody has some concrete idea about the removal this Trojan horse from Windows PC then their help will be greatly appreciated. Thanks in advance.
Well yes, its a very hazardous Trojan horse and you must need to remove Trojan-Cliker.VBS.Agent.dj immediately from your infected system as soon as possible. You may prefer to go through the below given post to get more details about this threat from Windows PC.

Know How Dangerous Is Trojan-Cliker.VBS.Agent.dj For Your Windows PC ?
As it name suggests, Trojan-Cliker.VBS.Agent.dj has been considered as one of the maleficent Trojan horse infection. This has been infamous to silently intrude into its target PC and cause severe destruction. This can spread into user's PC via multiple ways like clicking on malicious links, deceitful adverts, opening suspicious email attachments, visiting malicious sites and so on. Not only this it can also be transferred to your system along with some infected file transfer through networks or some external storage devices like pen drives.
What Harms Can Trojan-Cliker.VBS.Agent.dj Cause On Your Infected PC ?
- This firstly changes multiple system's parameters and alters the Windows startup processes.
- It can even injects malicious entries to the Windows registry in order to perform its harmful activities easily.
- Trojan-Cliker.VBS.Agent.dj also add malicious code snippets in the background processes of your infected system to hide its malicious activities from security softwares.
- Moreover it is also capable to disable the default antivirus software and firewall of your infected PC to avoid its detection and removal.
- This can eat up your system resources like CPU usage, RAM, storage space etc. to carry out its illegal operations.
- The worst thing is that it can connect the infected system to its remote servers and provide unauthorized access of your PC to the hackers.
No doubt, due to the misdemeanor of Trojan-Cliker.VBS.Agent.dj into your PC you may not only suffer from system related issues but also risks your privacy. In worst scenarios you may face issues like identity theft, financial losses, privacy issues etc. Therefore it has been strongly recommended by the experts to delete Trojan-Cliker.VBS.Agent.dj as early as possible from your infected PC. As the manual removal methods are quite complex and troublesome for most of the computer users, hence experts suggests victims to go for some well known Windows scanner for its removal.
Steps to Delete Trojan-Cliker.VBS.Agent.dj
Step: 1 Restart your Windows PC in Safe Mode
Find the complete details on how to Reboot your PC in Safe Mode (if you are a novice, follow the above given instructions on how to boot up your PC in Safe mode irrespective of the Windows Version that is being used as Windows XP, 7, Win 8, 8.1 and Windows 10)
Step:2 Remove Trojan-Cliker.VBS.Agent.dj from Task Manager
Press CTRL+ALT+DEL simulataneously to open Task manager. Find Trojan-Cliker.VBS.Agent.dj Related processes or any other suspicious processes that are running on it. Now Select and delete Trojan-Cliker.VBS.Agent.dj virus from Task Manager at once.

Step:3 How to Delete Trojan-Cliker.VBS.Agent.dj Related Startup Items
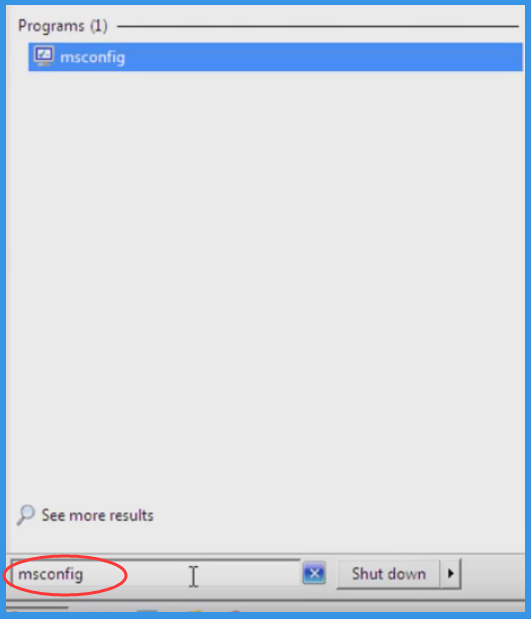
Press Win + R together and Type “msconfig”.

Now press Enter Key or Select OK.
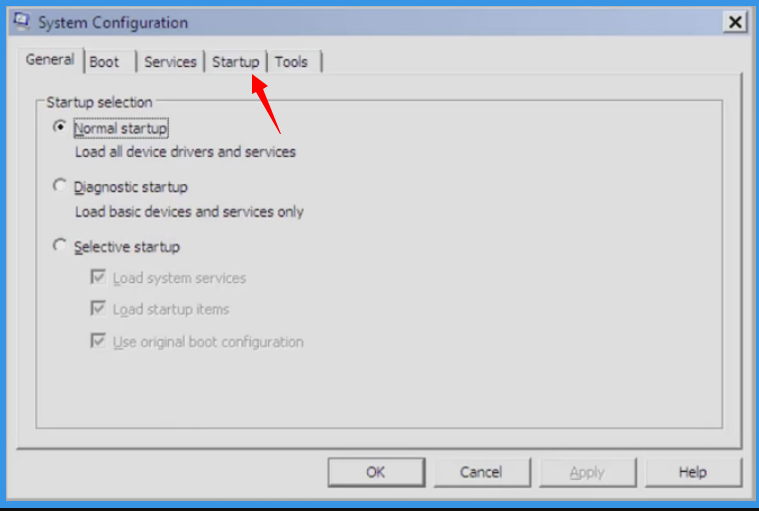
“Startup” option is to be selected on the Pop-up Window Tab
Now Search for Trojan-Cliker.VBS.Agent.dj Related applications on Startup Items
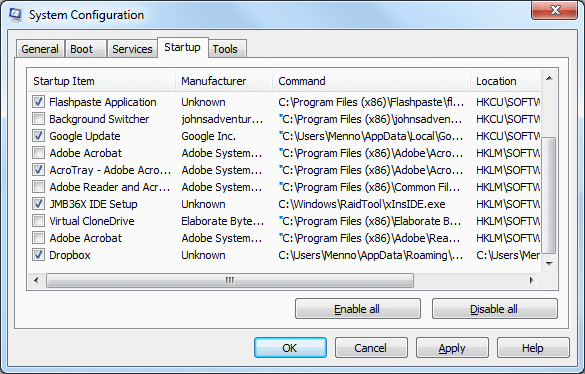
Now Uncheck all Unknown or Suspicious items from “System Configuration” related to Trojan-Cliker.VBS.Agent.dj

Now Click and Select Restart to Start your Computer in Normal Mode
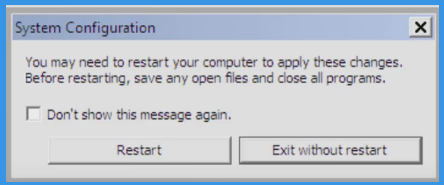
Step: 4 How to Delete Trojan-Cliker.VBS.Agent.dj from Windows Registry
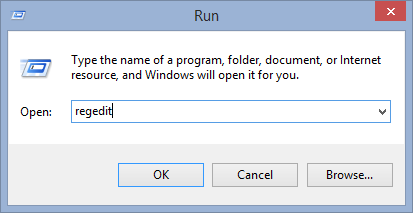
- Press Win + R in combination to Open Run Box, Type regedit on the search box and press enter.
- This will Open the registry entries.
- Find Trojan-Cliker.VBS.Agent.dj related entries from the list and carefully delete it. However be careful and do not delete any other entries as this could severely damage the Windows Component.
Also, after completing the above steps, it is important to search for any folders and files that has been created by Trojan-Cliker.VBS.Agent.dj and if found must be deleted.
Step 5 How to View Hidden Files and Folders Created by Trojan-Cliker.VBS.Agent.dj
- Click on the Start Menu
- Go to Control Panel, and Search for folder Options
- Click on view hidden files and folders Options, For your convenience, we have included complete process on how to unhide files on all Windows Version. This will delete all the files and folders associated with Trojan-Cliker.VBS.Agent.dj that was existing on your compromised system.
Still, if you are unable to get rid of Trojan-Cliker.VBS.Agent.dj using manual steps, you need to scan your PC to detect Trojan-Cliker.VBS.Agent.dj.
Don’t forget to submit your questions or any other queries if you have and get complete solution from our Expert’s Panel. Good Luck!




