| 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc is a Trojan | |
| Trojan Dropped by 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc are PWSteal.Lmir.BMQ, Trojan.Tatanarg.B, Malware.Yero, Trojan.Fripmerd.A, PWSteal.Bzub.gen, Infostealer.Castov, Trojan-Downloader.Win32.Mufanom.aafz, Pushbot.RT, TROJ_STARTPA.AET, Trojan.Win32.Bzud.b, Trojan.StealthProxy.B | |
| Related spyware ICQ Account Cracking, SysSafe, TorrentSoftware, SearchTerms, MySpaceBar, XP Cleaner, WNAD, RaxSearch, EScorcher, Multi-Webcam Surveillance System, SafeSurfing, Trojan.Win32.CP4000, DataHealer | |
| Windows Error caused by 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc are – 0x80244003 WU_E_PT_SOAPCLIENT_GENERATE Same as SOAPCLIENT_GENERATE_ERROR – SOAP client failed to generate the request., 0x00000048, 0x00000018, 0x8024001D WU_E_INVALID_UPDATE An update contains invalid metadata., 0x0000009C, 0x0000001F, 0x00000017, 0x0000006E, 0x00000068, 0x80244022 WU_E_PT_HTTP_STATUS_SERVICE_UNAVAIL Same as HTTP status 503 – the service is temporarily overloaded., 0x8024D00E WU_E_SETUP_REBOOTREQUIRED Windows Update Agent setup package requires a reboot to complete installation. | |
| 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc infects these windows .dll files rdchost.dll, usmt2xtr.dll, ExplorerFrame.dll, hpfvuw73.dll, qdvd.dll, NCProv.dll, kbdfc.dll, msltus40.dll, ehiiTV.dll, dmdlgs.dll, rwnh.dll |
16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc may have entered your pc through these software. If you have not installed them , then get rid of them The Edge 1.3 , BookAssembler 2.0.1 , Submerge 3.2.1b2 , Tiffen Dfx v3.0.10.4 , mm2ical 1.0 , conformalizer 3.6 , gps4cam 6.1.1 , ToringoLib for REALbasic 1.0 , DRAMM 0.1 , 24U Preferences+Globals Plug-In 1.0 , Yahoo! Map of … 1.0 , Fluency Timer 1.4 , GrandPerspective 1.5.1 , Clementine , iSous 0.9.5 , The Darkness II 1.1.0 , CloudOsys Lite 2.6b8 , LogTen Pro 6.5.1 |
|

Kill 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc From PC Using Manual Guide
All Information Of 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc
16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc is a trojan virus which is considered as heuristic detection for computer systems. This vicious computer infection easily infects Windows system that has been designed by cyber criminals in such an analytic way that it penetrates into your PC without your permission. This penetration results in the transfer of crucial information such as IP address, login details, banking details, passwords, credit card and debit cards. A trojan virus infection is so critical that it can easily cause severe corruption issue in the targeted PC. The corruption is so severe that it can leads to loss of system files and important data. Typically, a trojan enters your PC in secret way such that no one notices its arrival on the targeted PC.
16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc is one such deadly virus infection that it may slip into your system in form or either an executable file or some other packed stuff. When it comes in form of executable file, you normally ignore such type of application because you wonder that this application might have some important function on your PC. And when it arrives as free software then you did not notice it and its presence on the system. In both ways, trojan is given an opportunity to stay for longer time on the compromised PC.
Being a silent sneaker, penetration in the computer is silent and secret. You will remain unaware and the virus reaches to its destination folder. The moment 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc is installed on your PC, it starts the destruction right away. However, the most devastating part about this cunning malware infection is that it can operate all kinds of malicious operations into the system and does not even require user’s permission. All the files it run gets executed automatically. These files are run simultaneously with the start of OS. Due to this cunning malware infection, it is very hard to perform all the functions and operations smoothly.
In the presence of the trojan virus, various types of problems start to occur and displays error messages on the screen. Further, 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc conducts malicious activities to damage the OS completely. This decreases the system efficiency and response time that annoys the user most. It can easily disable essential components and running system applications. Hence, what is needed is to remove 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc soon from your computer else it can lead to serious destruction.
Steps to Delete 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc
Step: 1 Restart your Windows PC in Safe Mode
Find the complete details on how to Reboot your PC in Safe Mode (if you are a novice, follow the above given instructions on how to boot up your PC in Safe mode irrespective of the Windows Version that is being used as Windows XP, 7, Win 8, 8.1 and Windows 10)
Step:2 Remove 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc from Task Manager
Press CTRL+ALT+DEL simulataneously to open Task manager. Find 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc Related processes or any other suspicious processes that are running on it. Now Select and delete 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc virus from Task Manager at once.

Step:3 How to Delete 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc Related Startup Items
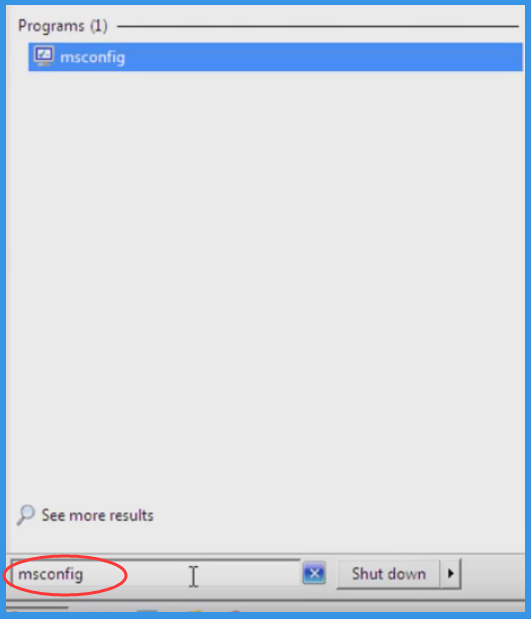
Press Win + R together and Type “msconfig”.

Now press Enter Key or Select OK.
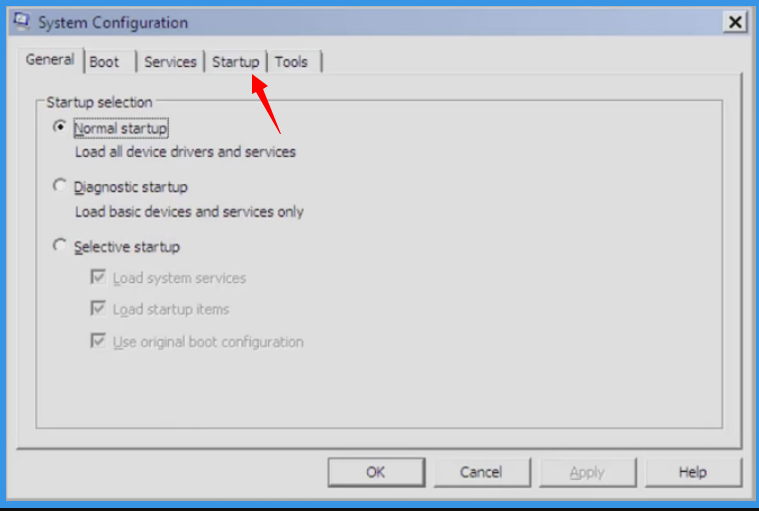
“Startup” option is to be selected on the Pop-up Window Tab
Now Search for 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc Related applications on Startup Items
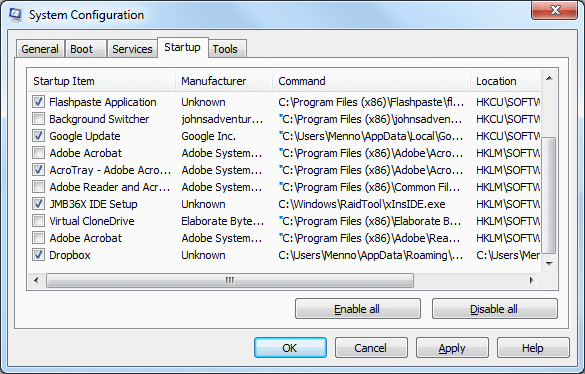
Now Uncheck all Unknown or Suspicious items from “System Configuration” related to 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc

Now Click and Select Restart to Start your Computer in Normal Mode
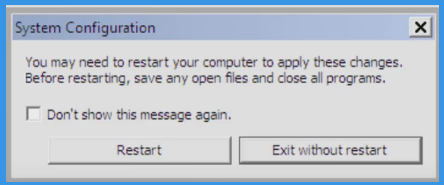
Step: 4 How to Delete 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc from Windows Registry
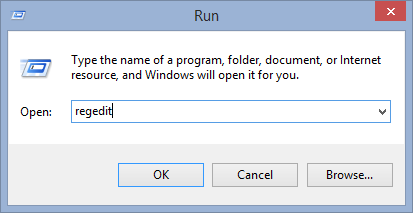
- Press Win + R in combination to Open Run Box, Type regedit on the search box and press enter.
- This will Open the registry entries.
- Find 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc related entries from the list and carefully delete it. However be careful and do not delete any other entries as this could severely damage the Windows Component.
Also, after completing the above steps, it is important to search for any folders and files that has been created by 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc and if found must be deleted.
Step 5 How to View Hidden Files and Folders Created by 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc
- Click on the Start Menu
- Go to Control Panel, and Search for folder Options
- Click on view hidden files and folders Options, For your convenience, we have included complete process on how to unhide files on all Windows Version. This will delete all the files and folders associated with 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc that was existing on your compromised system.
Still, if you are unable to get rid of 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc using manual steps, you need to scan your PC to detect 16qr2Req6AFZmYWeGnqtfTUYwhMayQX2Kc.
Don’t forget to submit your questions or any other queries if you have and get complete solution from our Expert’s Panel. Good Luck!


