| Beapy is a Keylogger | |
| Trojan Dropped by Beapy are Spy.Keatep.B, IRC-Worm.Flying, Jane, Tatanga Trojan, Packed.Tdss, SearchClickAds, I-Worm.BWG, Virus.VBInject.gen!GS, I-Worm.Kazus.c, PNuke 1.0, I-Worm.Calil, Rizzo Trojan | |
| Related spyware Look2Me Adware, Windows Precautions Center, Windows Custom Settings, Spyware.Acext, Trojan-Spy.Win32.Dibik.eic, Surf Spy, 4Arcade PBar, CasinoOnNet, Fake Survey, MySpaceIM Monitor Sniffer, Securityessentials2010.com | |
| Windows Error caused by Beapy are – 0x80243004 WU_E_TRAYICON_FAILURE A failure occurred when trying to create an icon in the taskbar notification area., 0x000000A7, 0xf0822 CBS_E_ILLEGAL_COMPONENT_UPDATE Component update without specifying |
|
| Beapy infects these windows .dll files mcepg.dll, iisui.dll, ReachFramework.ni.dll, Groupinghc.dll, xpsp1res.dll, msvideo.dll, gpapi.dll, msnmetal.dll, cimwin32.dll, atiumdva.dll |
Beapy may have entered your pc through these software. If you have not installed them , then get rid of them ModTools 1.5 , PHOTORECOVERY Pro 2013 , Spinvaders 1.0.0 , Japanese FlashCards , AVCWare DVD to iPod Converter 6 , SaveCircle 1.2 , Power Amortize 1.6 , MathType 6.7h 14111000 , Plot , Machi Poco 1.4 , System Profile to iPod 1.1.2a , TripleSoccer 1.0.2 , Vowl 1.2 , Amseq 0.3.1 , GreaseKit 1.7 , Renamerox , Mahjong In Poculis , Math Helper 1.1 , SingleCrystal 2.3.3 |
|

Remove Quickly Beapy From Windows
An Illustration Of Beapy
Beapy is a Trojan program. It corrupts files and trigger the security bugs for the hackers to occupy the space in the computer. It steal data and execute malicious codes. It hide itself in the background and give chance to the remote hackers to take over your computer.
What Are The Methods By Which Beapy Get Enters Into Your System?
Beapy is penetrated by the several methods. The bundling technique is mostly used by the hackers for penetrating this trojan virus quickly without any user permission into the computer. The bundling technique means free downloading of software which contains viruses and when user download this free software the computer viruses attack inside it. It sneak from the backdoor system and give more vulnerability to the computer. It is also capable to support other threats to attack inside the system. Spam email, peer to peer network file sharing system, and junk email attachments are the vital sources from which Beapy can come inside your computer. The other methods are also useful to this trojan virus to attack into your computer like clicking on the suspicious links, visiting porn or other malicious websites, and etc.
What Are Symptoms That Beapy Uses For Creating Problems Into Your System?
- It modify the default system settings without user authorization.
- It mislead to the phishing sites produces numerous ads and make browser work-less.
- Capable to gather important information.
- It causes system crash.
- It makes PC compromised which helps to the remote attacker.
- It helps the hackers to disturb your privacy.
What Are The Harmful Activities Of The Beapy?
The hackers inject the malicious code in the browser and starts bad activities. It steal the information of the user like bank account details, credit card number, password,login ID and so on. The hackers generate money illegally from stealing your information. They cheat you and you will get victim. They used your data for marketing campaign. So, it is much better to remove quickly Beapy from your computer.
What Are The Preventive Action Which Can You Take For Beapy?
Stop executing any kind of program in your system unless you faith that it is from a secure source. Stop opening of unknown sender’s email or junks mail attachments. Update your antivirus program regularly inside your computer. Install latest version of your operating system regularly. Scan pen drive, DVDs, CDs or any other hard drive before using it. Do not accept the instant messaging apps program scan the downloaded program quickly before using it.
Steps to Remove Beapy
Step 1>> How to Boot Windows in Safe Mode to isolate Beapy
Step 2>> How to View Hidden Files created by Beapy
for Windows XP
- Exit all Program and Go to Desktop
- Select My Computer icon and Double Click to Open it
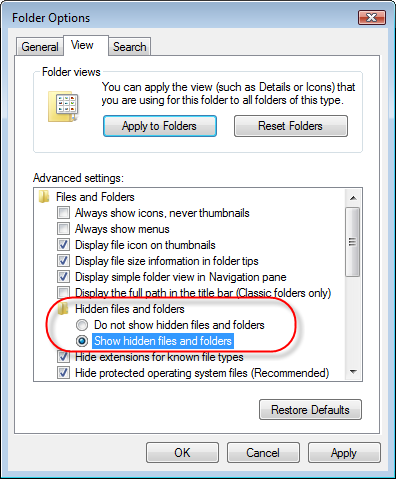
- Click on the Tools Menu and now select and Click on Folder Options.
- Select on View Tab that appears in New Window.
- Check mark on the box next to Dispaly the Contents of System Folders
- Now Check the box in order to Show Hidden Files and Folders
- Now press on Apply and OK to close the Window.
- As soon as these steps are performed, you can view the files and folders that were created by Beapy and hidden till now.
for Windows Vista
- Minimize all Window and Go to Desktop
- Click on the Start Button which can be found in lower lef Corner having Windows Logo
- Click on the Control Panel on the Menu and Open it
- Control Panel can be opened in Classic View or Control Panel Home View.
- If you have Selected Classic View, follow this
- Double Click on the Folder icon to open it
- Now select the view tab
- Click on Option to Show Hidden Files or Folders
- If you have Selected Control Panel Home View, follow this
- Appearance and Personalization link is to be Clicked
- Select on Show Hidden Files or Folders
- Press Apply Option and then Click on OK.

This will Show all the Folders including those created by Beapy
Know how to view Hidden Folders on Windows 7, Win 8 and Windows 10
(Following the above steps are necessary to view all the files created by Beapy and that is known to exist on Compromised PC.)
- Open the Run Box by holding together the Start Key and R.

- Now Type and input appwiz.cpl and press on OK
- This will take you to the Control Panel, Now Search for Suspicious programs or any entries related to Beapy. Unistall it once if you happen to find it. However be sure not to Uninstall any other program from the list.
- In the Search Field, Type msconfig and press on Enter, this will pop-up a Window

In the Startup Menu, Uncheck all the Beapy related entries or which are Unknown as Manufacturer.
Step 3>> Open the Run Box by Pressing Start Key and R in Combination
- Copy + Paste the following Command as
- notepad %windir%/system32/Drivers/etc/hosts and press on OK
- This will Open a new file. If your system has been hacked by Beapy, certain IP’s will be displayed which can be found in the bottom of the screen.
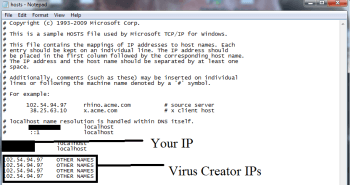
Look for the suspicious IP that is present in your Localhost
Step 4>> How to Terminate Beapy Running Processes
- Go the Processes Tab by pressing on CTRL+SHIFT+ESC Keys Together.
- Look for the Beapy Running Processes.
- Right Click on Beapy and End the Process.

Step 5>> How to Remove Beapy Related Registry Entries
- Open Registry by Typing Regedit in the Run box and Hit Enter Key
- This will open all the list of entries.
- Now Find and search the entries created by Beapy and cautiously delete it.
- Alternatively, you can manually search for it in the list to delete Beapy Manually.
Unfortunately, if you are unable to remove Beapy, Scan your PC Now
Also submit question and let us know in case you are having some doubt. Our Experts will definitely respond with some positive suggestions for the same. Thanks!


