Explanation About [email protected] Ransomware
[email protected] Ransomware can be detected as a new variant of encryption Trojans which was recently identified on 8th October, 2018 and categorized under the family of ransomware. It can be defined as an advance cyber malware which can use open-source ciphers for encrypting the essential files of the innocent victimized user and compels them for buying the decryption key. It can appends the file names with the wired file extensions also. It is intensionally created by the cyber spammers which secretly infiltrates into the system without any consent, locks all the crucial data using ASE and RSA sophisticated powerful algorithm and after encryption it demands for money using ransom warning note in exchange of decryption key from the innocent system end user. There is no assurance in paying ransom amount, the users may never get accessing to the corrupted files else they only get fooled by the cyber attackers. Hence, it is always recommended just to ignore these type of warning messages.
Sources Of [email protected] Ransomware
[email protected] Ransomware is a threatening file-locker which is functioning like a crypto-threat virus that uses encrypting technologies for making unreadable user files and always promotes to restore the affected files by purchasing the decryption program from the remote hackers. It may run from the temporary files and Application Data directories. It alters the encrypted files by adding .encr extension to the end of the file name. This malware virus can easily get into the system through various methods like from peer to peer file sharing, online gaming sites, infected external USB drives, porn sites, pop-up ads from free pirated software packages, through Spam mails or junked mail attachments and so on.
Weak Points Of [email protected] Ransomware
There are the some weak points which are caused due to the appearance of [email protected] Ransomware into the infected system such as:
- It can add odd extensions at the end of the infected files names.
- It can disables the accessing any of the stored files.
- It degrades the system performance.
- It can also delete some of the essential system files.
- It can drop a ransom note in the form of .txt or .html text files.
- It can keep threaten the user for deleting the important system files.
- It can able to lock the desktop screen so that it cant get accessed.
- It can completely stops the working of anti-virus software.
Erasing Of [email protected] Ransomware
The complete deletion of [email protected] Ransomware can be easily performed by using the automatic or manual tool methodology.
Free Scan your Windows PC to detect [email protected]
How To Remove [email protected] From Your PC
Start Windows in Safe Mode with Networking.
- Click on Restart button to restart your computer
- Press and hold down the F8 key during the restart process.

- From the boot menu, select Safe Mode with Networking using the arrow keys.
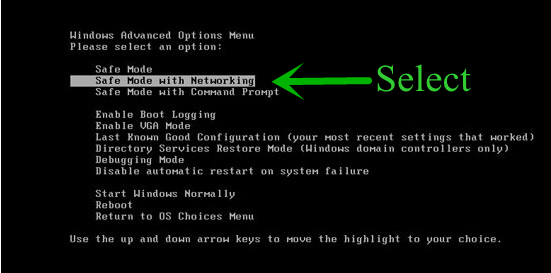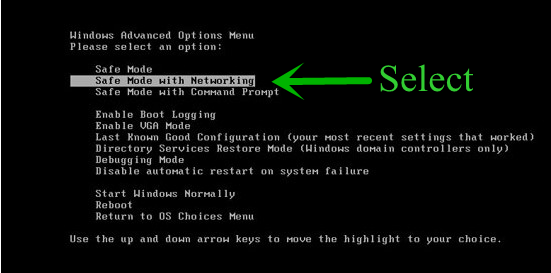
- Now your computer will get started in Safe Mode with Networking.
End [email protected] Related Process From Task Manager
- Press Ctrl+Alt+Del together on your keyboard.

- Task manager Windows will get opened on your computer screen.
- Go to Precess tab, find the [email protected] related Process.
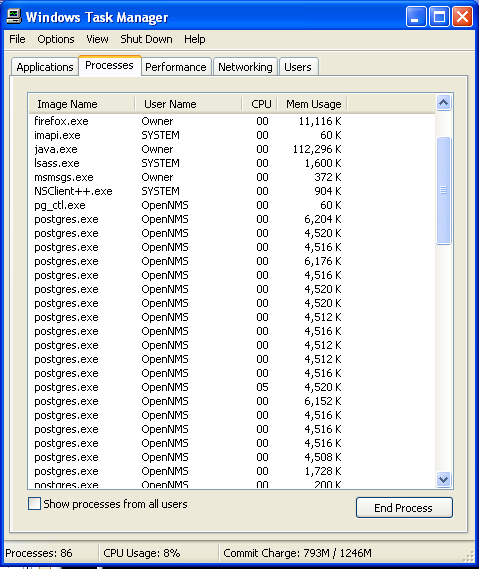
- Now click on on End Process button to close that task.
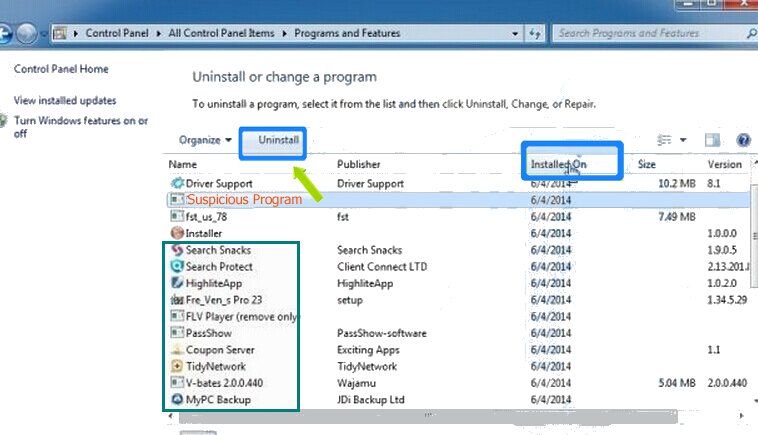
Uninstall [email protected] From Windows 7 Control Panel
- Visit the Start menu to open the Control Panel.
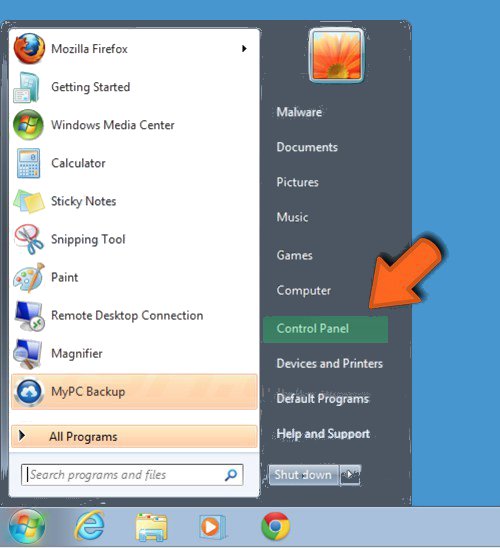
- Select Uninstall a Program option from Program category.
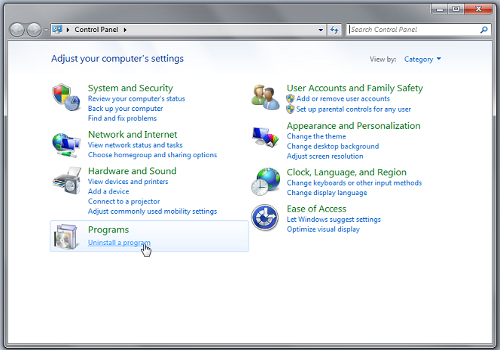
- Choose and remove all [email protected] related items from list.
Uninstall [email protected] From Windows 8 Control Panel
- On right edge of screen, Click on Search button and type “Control Panel”.

- Now choose the Uninstall a Program option from Programs category.

- Find and delete [email protected] related items from the programs list.

Delete [email protected] From Windows 10 Control Panel
- Click on Start button and search Control Panel from Search Box.

- Got to Programs and select the Uninstall a Program option.

- Select and Remove all [email protected] related programs.
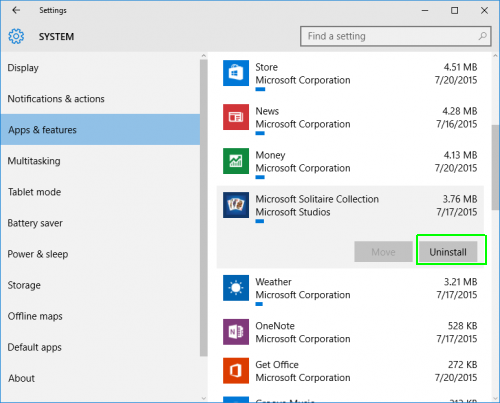
Remove [email protected] Related Registry Entries
- Press Windows+R buttons together to open Run Box

- Type “regedit” and click OK button.

- Select and remove all [email protected] related entries.
Remove [email protected] Infection From msconfig
- Open Run Box by pressing Windows+R buttons together.

- Now type “msconfig” in the Run Box and press Enter.

- Open Startup tab and uncheck all entries from unknown manufacturer.

Hope the above process has helped you in removing the [email protected] virus completely from your computer. If you still have this nasty ransomware left in your PC then you should opt for a malware removal tool. It is the most easy way to remove this harmful computer virus from your computer. Download the Free [email protected] Scanner on your system and scan your computer. It can easily find and remove this pesky ransomware threat from your PC.
If you have any questions regarding the removal of this virus then you can ask your question from your PC security experts. They will feel happy to solve your problem.