Ploutus is a Trojan malware which appeared in year 2013 in Mexico and resurfaced onto the security scan in the mid of November 2016 with an updated version. This malware is especially designed by the cyber offenders in order to work on ATMs powered by Windows operating system. It can interact with the with the latest versions of Windows OS and Windows XP as well. Cyber Security analysts that were investigating an empty ATMs revealed that physical integrity of machines was compromised to access inside mechanisms and install Ploutus malware. The initial release of this Trojan was designed to spews cash from the ATMs when the personal keyboard is connected to an infected ATM. However, the newer version features a significant improvement.
What is old and new in Ploutus Malware?
The newer version of Ploutus Trojan comes with a launcher which makes attempts at identifying the security tools and killing them. Samples of this malware also showed that it is using a better ‘.NET’ obfuscator called as ‘Reactor’. All versions of the Trojan does not require a master card to be inserted onto the compromised ATM. In addition, a legit software which runs on ATMs is introduced with the malware in order to make sure that the infection doesn’t depend on built-in components.
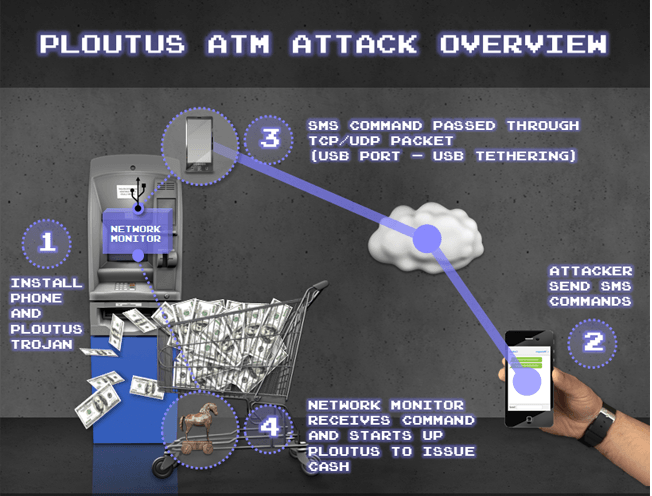
The older version of the Ploutus malware accepted commands from an external keyboard and numeric pad on ATM. When the money mule was on ATM, an 8-digit code had to be inserted in order to initiate the release of money. Although, the updated version of this Trojan threat is designed to pull the commands from a mobile phone which is attached to the compromised ATM, and this makes it possible for the virus operators to send commands through a simple text message. However, this practice is new among the ATM infections and makes the Ploutus superior to other nasty Trojans in this class such as SUCEFUL and Alice.
Mobile Phone Sends Commands To Ploutus Malware via USB Cable
The mobile device is designed to analyze messages received and transform them into the network package which is sent for processing into the compromised ATM. The packets are usually forwarded over a simple USB cable. Additionally, a foreign mobile phone tracks an inbound and outbound traffic onto the ATM, and feature may be improved upon in following releases of Ploutus malware. The tool can enable the Trojan operators to run as fast as possible and mobile operations where they break into the ATMs and attach a mobile communications device, that can be operated remotely.

The mobile phone would act as a controller and make the ATM machine release money from the machine’s cassettes on command. Thankfully, the bank debit and credit cards are not targeted by the Ploutus malware and you don’t need to worry for now. As mentioned above, this Trojan malware is introduced to the ATMs by compromising an outer layer, which involves the crude tools that leave marks onto the machine. Therefore, you may want to avoid the usage of ATMs which look like they were in a car crash and feature any unusual scratches.
