Crypt0L0cker Ransomware, also well known as Torrentlocker and simply Teerac, was first spotted in 2014 targeting Austria and European countries. But, afterwards, gradually its distribution was stopped. As a result, Crypt0L0cker started dying off in the middle of 2015. However, Crypt0L0cker Ransomware is back with spam campaigns especially designed to target European countries.
From few weeks, reports against Crypt0L0cker are being submitted on ID-Ransowmare site. According to the ID-Ransomware officials, thousands of computer users are uploading malicious file on their official site that directly point out toward Crypt0L0cker Ransomware (a.k.a. Torrentlocker/Teerac). Number of victims of the ransomware is increasing every day by 100 to 400. To present this fact more clearly, Daniel Gallagher created following ID-Ransomware submission chart:
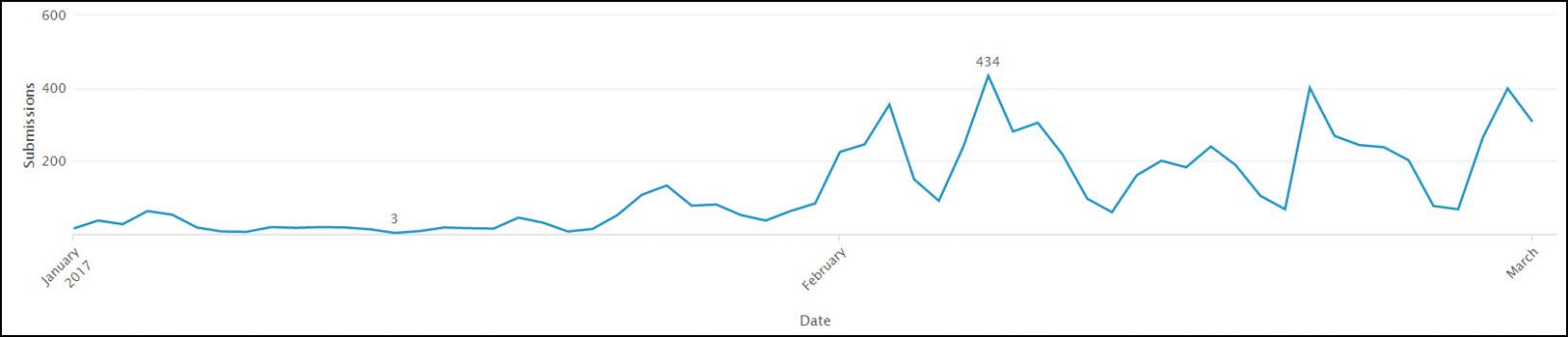
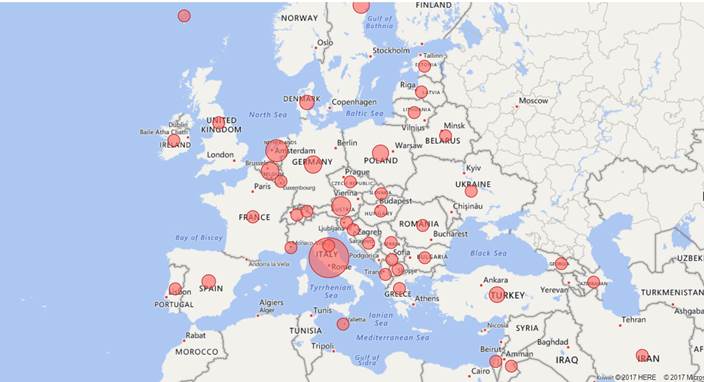
Further, security investigators at Microsoft Malware Protection Center also confirmed that Crypt0L0cker/Teerac, Being spread in European countries so quickly. Actually, increased activities of this ransomware can not be avoided. Crypt0L0cker Ransomware is apparently once again targeting European computer users to generate a huge revenue, say security experts. Further, latest report of Microsoft researchers reveals the Crypt0L0cker Ransomware campaigns appear to be heavily targeting Italy as shown in the following Telemetry Map:
 Crypt0L0cker Ransomware spam campaigns are utilizing Certified Electronic Email to deliver malicious JavaScript file that connects computer to a remote server and install Crypt0L0cker Ransomware with all of its components in back ground without any user’s knowledge. Such spam emails may feature a subject line Invio Fattura N. 391091 and contain .JS file with a name like fattura_398672.js.
Crypt0L0cker Ransomware spam campaigns are utilizing Certified Electronic Email to deliver malicious JavaScript file that connects computer to a remote server and install Crypt0L0cker Ransomware with all of its components in back ground without any user’s knowledge. Such spam emails may feature a subject line Invio Fattura N. 391091 and contain .JS file with a name like fattura_398672.js.
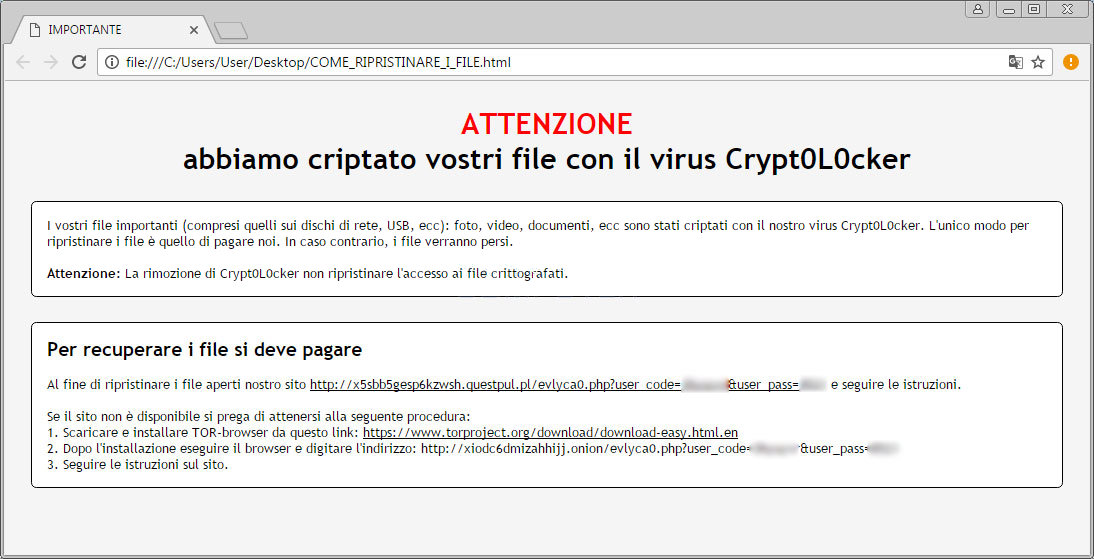
Interestingly, Crypt0L0cker spam campaigns use Italy’s Posta Electronica Certificata, in short PEC, enables anyone to send highly secured emails that having the same legal value as a registered letter. Of course, these emails are digitally signed to deceive potential targets into believing that the email is legitimate and official. Hence, it is important for all computer users, even corporate networks users to remain vigilant and practice safe computing habit, especially when it comes to checking emails.
