In the summer of year 2018, a new ransomware has started to pick up in latest variant dubbed as Zorro Ransomware. This ransom virus has been also identified as Aurora Ransomware in the past. Still, there is unknown how Aurora / Zorro Ransomware is spread but there are some indications that indicate that Aurora / Zorro Ransomware may be installed on user machine by hacking into machine and executing Remote Desktop Services (RDP). Hackers often brute force password for the RDP accounts to gain access to user PC and install several infection like ransomware.
Get Familiar With File Encryption Procedure of Aurora / Zorro Ransomware
Upon getting inside the PC, Aurora / Zorro Ransomware connects user PC to C&C server in order to receive data and file encryption key that used to lock user files. Then after it connects to geoplugin.net/php/gp in order to determine from which country user is belonging. Experts revealed that Aurora / Zorro Ransomware may not locks user file who are living in Russia country. It performs a deep scan and target almost all file types. It appends .aurora file extension while locking file.
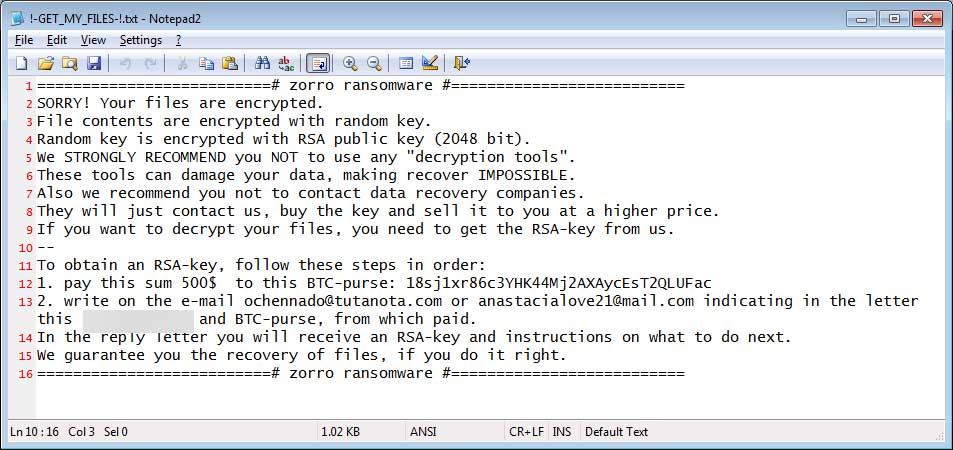
Upon locking files, Aurora / Zorro Ransomware creates ransom note in each folder entitled as !-GET_MY_FILES-!.txt, @[email protected] and #RECOVERY-PC#.txt that includes instruction on how to pay ransom fee. Ransom note also include an email address, [email protected] that urges victim to contact with hacker. Lastly, Aurora / Zorro Ransomware creates %UserProfile%wall.i file and set it as user default desktop wallpaper.
Tricks To Protect Your PC Against Aurora / Zorro Ransomware
- Use good security software and computing habit.
- Always keep a backup of your data.
- Be sure that RDP is locked correctly.
- Don’t open any suspicious or unknown attachment.
- Make sure that your OS and installed application is up-to-date.
- Use unique and strong password for several sites and many more.

