These days, a hot news is on the rise that developer of cryptocurrency mining malware hides itself into Fake Adobe updates that actually update the Flash to latest or current version. If you want to get all information about it then read this post completely.
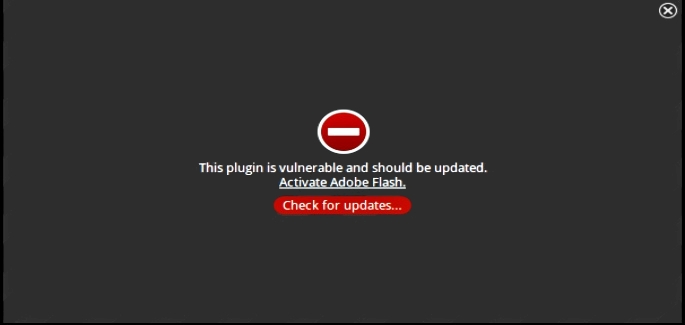
Fake Adobe : One of The Main Source of Crypto-Mining Malware Attack
With the enhancement in use of Internet, the malware attack grows rapidly at wide range specially cryptomining malware or cryptocurrency mining malware. Hackers often uses lots of channels to compromise machine with cryptomining malware but it mainly pushed into users PC in form of Fake Adobe update. However these fake adobe update notification make by team of cyber criminals by using pop-up notifications from official Adobe installer to convinces System user that it might be a genuine update.
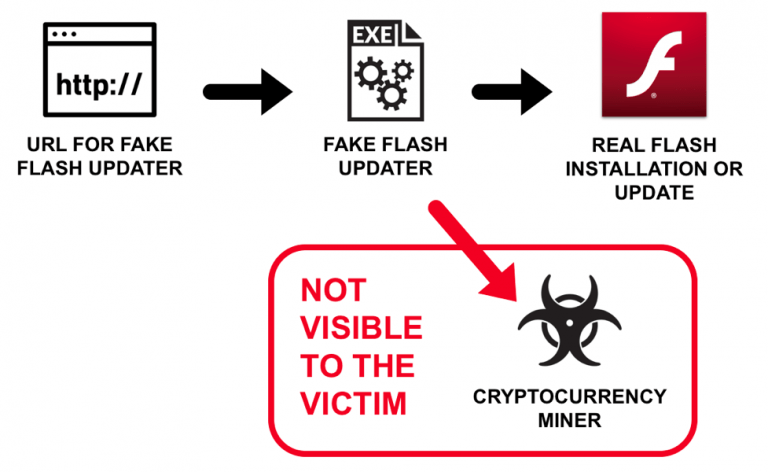
If you are one of those System user who take Fake Adobe updates notification as a real one then you have to really suffer with lots of negative traits and serious issues. When you will click on agree button to try to update Adobe by clicking on the appeared window then first of all Fake Adobe update install the crypto-miner malware and then after update Adobe to latest variant so that affected users don’t suspect any unusual thing.
Get Familiar With ‘Cryptojacking’ Term

There are several type of cryptocurrency related cyber crime but among all Cryptojacking is one of the most popular form and it is also the latest way of hackers for spreading the mining malware. By using the several script, hackers often install specific or certain programs on users PC which make use of their CPU power to mine the cryptocurrencies specially Monero. After mining cryptocurrencies hackers send the obtained currencies to wallet addresses of cyber hackers.
Negative Traits of Crypto-miner Malware
Once the cryptominer malware gets installed on user’s machine then immediately it initiates the mining processes which as a result slows down System overall performance speed. Due to the presence of such a malware user can observe the unusual process on task manager and several unusual things on affected machine including :
- Thousands of fake alert, notification or warning messages.
- Unnecessary modification in existing System settings.
- System behaves too much weird and slower than before.
- Highly consumes Computer & network resources and mine crypto currency.
- Disables the function of System’s crucial programs and many more.
